Cross-Tenant Label Visualization
Sharing information securely in documents is one of the main use cases for Information Protection technologies. This enables an organization to persistently protect shared data and have it consumed both inside and outside the context of their tenant. However, labels are, by design, visible only in the context of the author’s tenant. This means that users of other tenants are not aware of labels that are attached to the shared document.
If your company has more than one tenant, or you are sharing documents with a partner company that uses Azure Information Protection to label content, being aware of the labels set by users of the other tenant would be very beneficial. Although this is not something that is possible by default, you can create a mapping between labels across tenants so that a matching label can be displayed from your own tenant. This is not a solution for sharing labels, but rather a method to view the confidentiality set by the sender. If you want to create distinction between the labels of two tenants, you will need to create specific labels to reflect this within your tenant configuration.
This method does have a few limitations that you should be aware of:
- This is a one time operation after an AIP label has been applied by the author, and there is no sync if/when the document is updated.
- Because this procedure relies on advanced settings in the AIP profile, this feature is currently only available on Windows hosts running the AIP client. This functionality is not implemented in the Unified Labeling client or in Native Office integration and there is no timeline for this feature to migrate.
- There is also no sync back to the original sender/tenant. If you need to create a two way mapping, you must implement the solution on both Tenants, switching source and target labels.
NOTE: This works for Office and PDF documents, but not for E-mails. We will discuss Email later in this post.
Mapping Labels in documents
This mapping of the labels is based on an advanced capability of AIP that allows the reading classifications set by a different classification software. This uses the metadata contained in the original document to create a one to one mapping from the metadata item to a label. To create this mapping, you will need the labels IDs from the source tenant and the label IDs you want to map the source label IDs to within your tenant. The steps to perform this mapping are listed below:
Retrieve the label ID necessary for mapping
You can retrieve an external label ID directly from the AIP portal or from a labeled office document. To retrieve the label IDs from labeled Office documents, the external organization must provide these. This is useful, as you will also need these documents for testing.
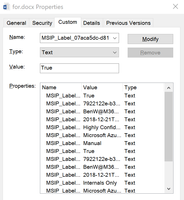
To retrieve the information from an Office document, follow the steps below:
- Right-click on the first document and select Properties from the context menu.Select the Custom tab from the properties dialog box to find the list of custom properties.
- Find the property MSIP_LABEL_<GUID>_ENABLED for the external label you want to create a mapping for and copy this property name.
If you have access to the AIP admin console for the external tenant, you may retrieve the label ID for the external label directly from the portal. To do this, follow the steps below:
NOTE: These are also the steps you will follow to capture the label ID for the labels you are mapping to.
- In the Azure Information Protection admin console (https://aka.ms/AIPConsole), select Labels in the blade on the left, and then click the label you want to create the mapping for (you will need the label ID for both the target label and source label to create this mapping).
- Copy the label ID located at the bottom of the page to a document for use later.
Repeat this for each label in the target and source tenant you wish to create a mapping for.
NOTE: If you do not have access to the AIP console for the source tenant, you will need to ask the external tenant admin to perform this procedure, or you may use the labeled document method discussed earlier.
Defining advanced settings
To define the necessary advanced settings for policy mapping, follow the steps below:
- In the AIP console, select Policies on the left.
- Right-click on the relevant policy you want this mapping to apply to, and click Advanced properties.
NOTE: If you set this value on a scoped policy, you can restrict the behavior to a smaller group of users. - Add the following property for each label you want to map
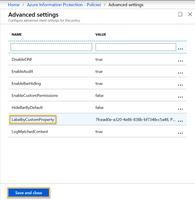
- Key: LabelByCustomProperty
This is a single, multi-part field with 4 comma separated values (example values provided below): - The Target label ID -> 7fcead0e-a320-4e86-838b-bf7348cc5a48
- An arbitrary name for the mapping rule -> ProtectedByMS
- The custom property Name for source label -> MSIP_Label_f42aa342-8706-4288-bd11-ebb85995028c_Enabled
- The custom property Value for the source label ->True (Case sensitive)
WARNING: The target label will only be applied if the recipient has edit rights on the source document.
The final value should look like:
7fcead0e-a320-4e86-838b-bf7348cc5a48, ProtectedByMS, MSIP_Label_f42aa342-8706-4288-bd11-ebb85995028c_Enabled,True
- Key: LabelByCustomProperty
- Press the Save and close button at the bottom of the page.
Now, when sending an office document from the Source tenant to the Target tenant, the specified target label will be displayed, and it will be applied when the document is saved.
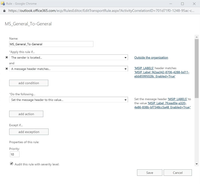
Converting Email labels
The procedures above described the mapping of labels in Office and PDF documents. Labeling of Emails can achieve a similar label mapping by using Exchange mail flow rules.
As before, you will need both the Source and the Target label IDs. In this case, we will use them to create a mail flow rules in the Exchange Online control panel to modify the value of a header called MSIP_LABELS and change it to reflect the value of the mapped label.
- In the Exchange Online Control Panel (https://outlook.office365.com/ecp), select Mail flow on the left.
- Click the + button in the top left corner of the rule list to create a new rule.
- In the presented dialog box define the following values:
- Apply this rule -> if the sender is located -> outside the organization (this condition is optional)
- And a message header matches –> “MSIP_LABELS” header matches “MSIP_Label_f42aa342-8706-4288-bd11-ebb85995028c_Enabled=True;”
- Set the Message header to this value -> Set the message header “MSIP_LABELS” to this value “MSIP_Label_7fcead0e-a320-4e86-838b-bf7348cc5a48_Enabled=True;”
- Save the rule.
WARNING: Ensure that each of the header values contains a semicolon in the end of the value.
NOTE: If you are configuring a sub-label, you will need to include both the parent and sub-labels in the set value. An example of this is shown below:
- Set the Message header to this value -> Set the message header “MSIP_LABEL” to this value “MSIP_<Parent label>_Enabled=True; MSIP_<Sub label>_Enabled=True;”
Conslusion
The steps above can enable two organizations to visualize labeled content and increase awareness of each other’s sensitive documents and emails. As mentioned above, you will need to perform this process for all labels you wish to map between the two organizations. This process can be repeated between any number of organizations, but the mapping must be configured for each pair of organizations. Please let us know in the comments below if you have any questions on this procedure.
Thanks,
The Information Protection Customer Experience Engineering Team