This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
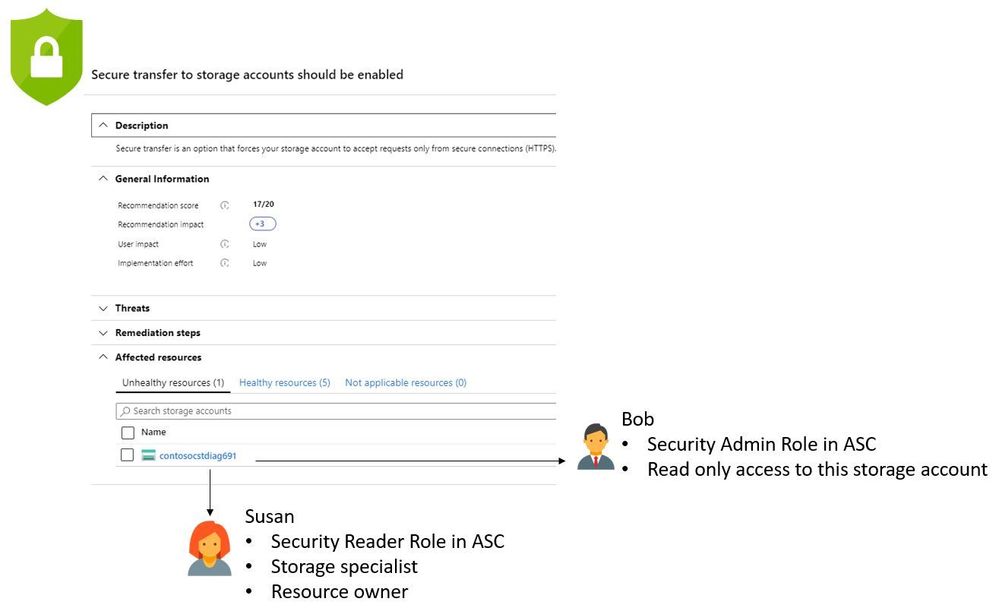
As customers continue their journey to improve their security posture in Azure by leveraging Azure Security Center Secure Score, they are realizing that collaboration among different teams is critical. The reason behind this statement is because usually the Security Team that manages Azure Security Center may not have privileges to change the settings in the workload in order to remediate a recommendation. This is a very common scenario as shown in the diagram below:
In this scenario, Bob is responsible for the cloud security posture management for their organization, but Bob doesn’t have privileges to remediate this storage recommendations. Bob needs to contact the resource owner and ask her to remediate. The question that Bob has is: how can I send a direct link to this page to Susan, so she can read about this security recommendation and follow the remediation steps? The answer is: send the security recommendation deep link!
Sharing Deep Link with Workflow Automation
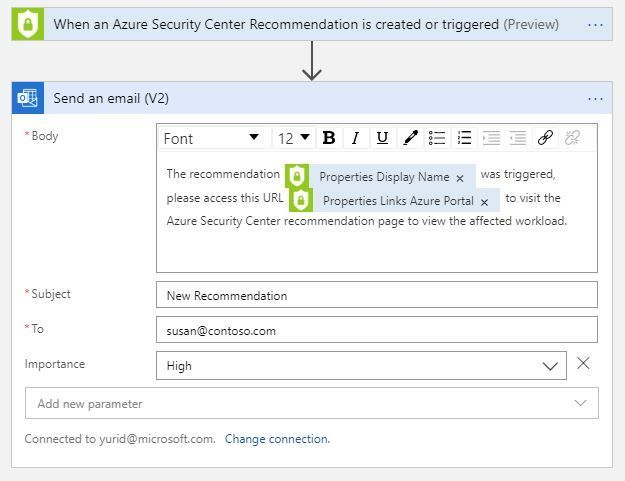
One way to do that is by creating a workflow automation that triggers a Logic App that sends an email to Susan and let her know that there is an open recommendation related to storage, and provide her the deep link to this recommendation. To configure that, you need to execute two major tasks:
Task 1: Create a new Logic Apps that has the following structure:
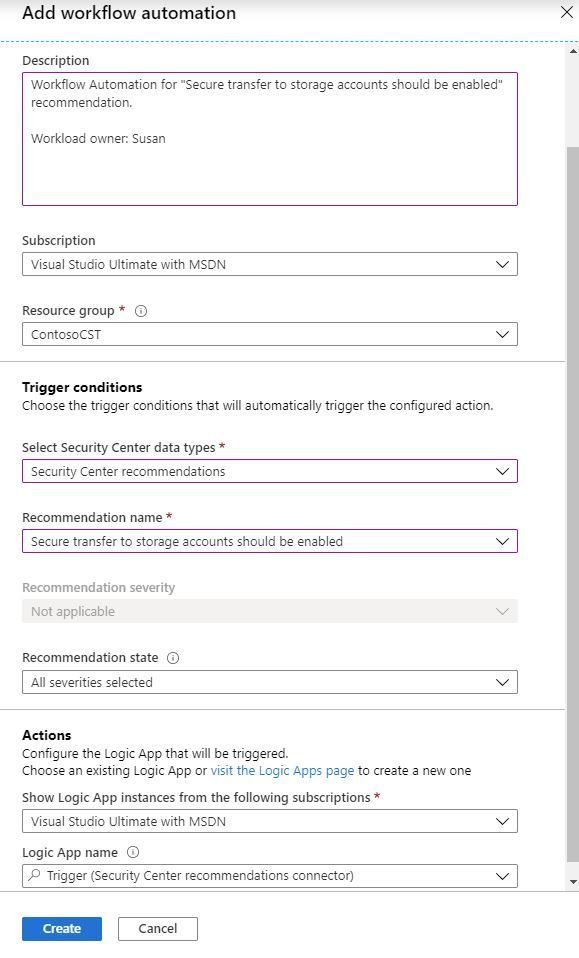
Task 2: Once you finish creating the Logic App, go to Azure Security Center, click in Workflow Automation and create an automation for the storage recommendation that calls this Logic App, as shown below:
Now that you finished, you just need to wait for the recommendation to trigger and Susan will receive an email with the deep link for the recommendation.
Obtaining Deep Link via API
You can also obtain the deep link for a recommendation using the following API call:
The fields that you must replace are:
- resourceId: the resource identifier
- assessmentName: this is actually the assessment key, which is a unique key for the assessment type
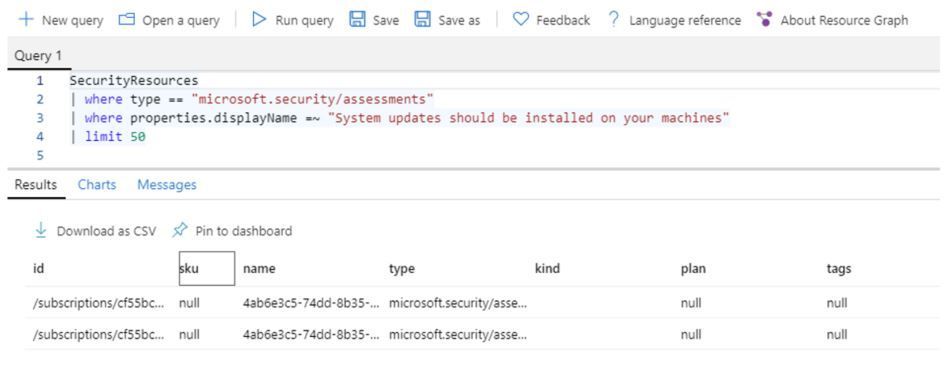
You can obtain this information via Azure Resource Graph (ARG) query, as shown in the example below:
Note: to learn more how to obtain Azure Security Center related data via ARG, read this blog post.
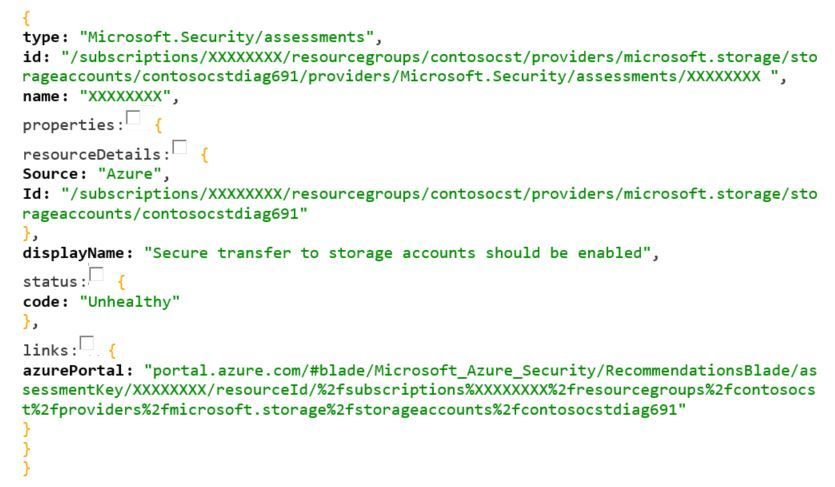
The resourceId is located in the Id column and the assessmentName is located in the name column in the result above. Below you have an example (X’s were added to replace private information) of the body result of this HTTP GET:
If you want to access the deep link, copy the entire string under azurePortal field and paste in your authenticated browser session.
Reviewers
Special thanks to the reviewers of this blog post:
Shahar Weiss, Senior Software Engineer (ASC Team)
Yoav Francis, Senior PM (ASC Team)