This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Several federal initiatives such as CDM (Continuous Diagnostic and Mitigation), TIC (Trusted Internet Connection) increasingly becoming similar, in that identical tools and approaches such as Zero Trust can be used to meet multiple federal mandates. This convergence provides an opportunity to reduce complexity while helping agencies improve their security posture and increase IT efficiency.
This blog, the third of a four-part series on meeting federal mandates with SaaS services, provides a deep dive on securing the platform.
Using Microsoft Secure Score to implement cloud controls
Implementing proper cloud controls is imperative to an organization as more data moves to the cloud. Most Cloud breaches can be traced back to an attacker compromising credentials, because the proper controls were not enabled to protect the identity. To help gain a holistic view of your cloud estate,
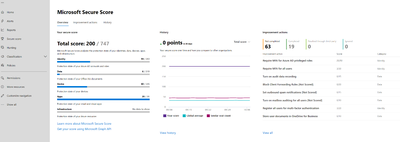
Microsoft has introduced a scoring concept called Microsoft Secure Score. Microsoft Secure Score provides recommendations across your entire data estate to include identity, data, apps, and infrastructure. Secure Score will provide recommendation to your organization and increase your score as you enable the recommended security controls.
Figure 1 Microsoft Secure Score
Using Azure Identity Governance
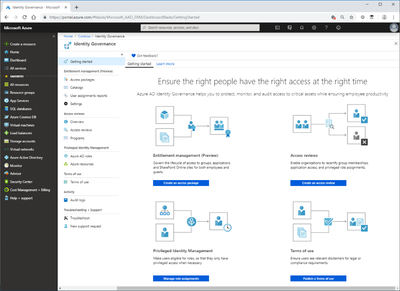
A common question from customers is, how do we protect the platform now that it is internet accessible all the time? If we go back to a Zero Trust model and the concept that Identity is the perimeter, we start by securing our sensitive accounts. Azure Identity Governance is a combination of Access Reviews, Privileged Identity Management, Entitlements, and Terms of Use. If you are wondering why we are talking about Azure governance when the focus is Office 365, remember, Office 365 uses Azure Activity Directory for its identity service.
Figure 2 Azure Identity Governance getting started page
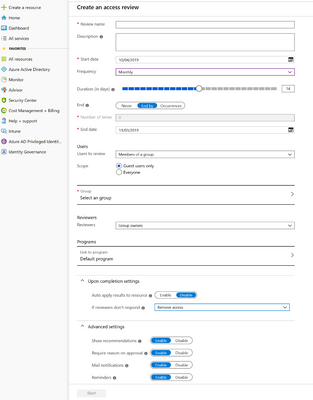
Azure AD access reviews allow organizations to configure polices and control group membership. Organizations define how often they want to review group membership, who can approve the users, and what action to take if the review process does not occur. Controlling and reviewing sensitive accounts on regular basis helps protect organization from mis-configuration and reduces risk.
Figure 3 Access Review creation wizard
Configuring Azure AD PIM
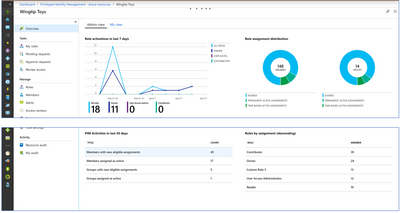
The second component of Identity Governance is Azure AD PIM (Privileged Identity Management); PIM follows the rule of least privilege. When PIM is enabled on an account, that account has zero standing rights. This forces staff to go through a process to “request” elevation of privilege. Organizations can configure several options for this process. The most common is to require an approver before rights can be elevated.
Example:
- Admin.1 logs into Microsoft Azure, but when Admin.1 logs on, he/she does not have administrative access.
- Admin.1 must request access to their administrative role.
- When requesting access, Admin.1 must use multi-factor authentication to increase privilege.
- Admin.1 becomes Global Admin for 2 hours, after which the rights are removed.
The PIM services audits and logs the entire process, providing organizations a detailed set of information to review while keeping the rule of least privilege.
Figure 4 Privilege Identity Management dashboard
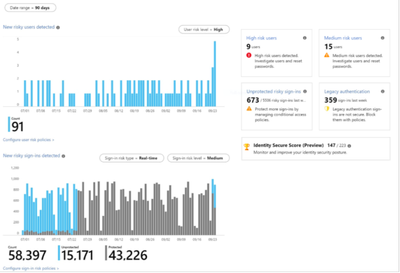
Using Azure Identity Protection
Azure Identity Protection generates risk levels, alerts, and reports that can be analyzed by your organization to help identify any suspicious activity. When users attempt to access your applications, a conditional access policy can determine if access is acceptable or should be denied based on the user risk level. This allows organizations to determine their acceptable level of risk and helps with three key concepts:
- Automate the detection and remediation of identity-based risks
- Investigate risks using data in the portal
- Export risk detection data to third-party utilities for further analysis
Figure 5 Azure Active Directory Identity Protection dashboard
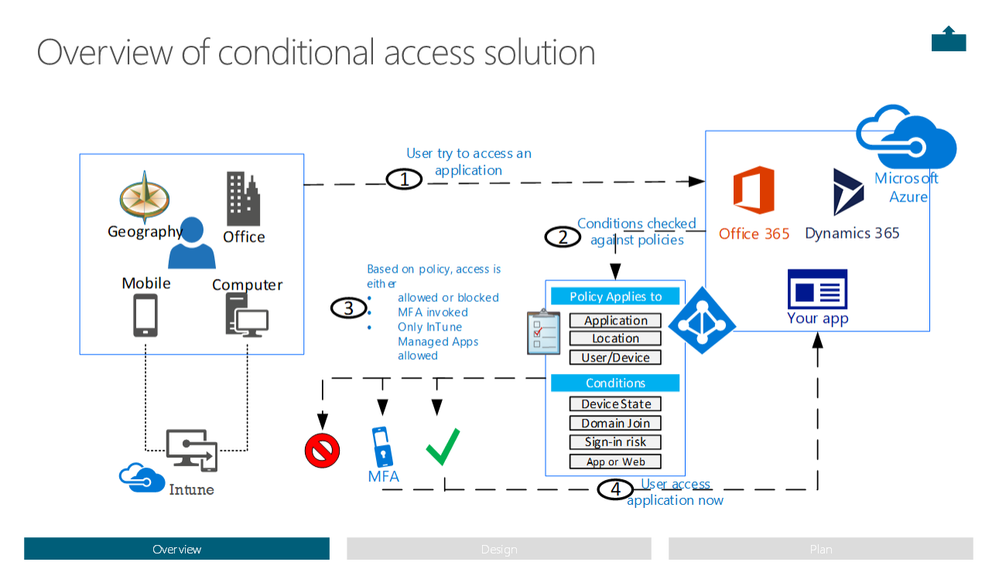
When accessing Office 365, authentication/authorization is controlled with Azure Active Directory. Since authentication is centrally controlled and Microsoft cloud solutions are natively integrated, organizations may additionally leverage conditional access policies to further block access. Organizations can require that privileged accounts can only logon from a corporate network, require multi-factor authentication, and the device must be healthy. Setting conditions on all accounts is critical, especially for privileged identities to help mitigate a potential breach.
Figure 6 Overview of Conditional Access
Office 365 is a suite of solutions that include Microsoft Exchange Online, SharePoint Online, Teams, and more. To cover all the configurations is outside the scope of this article. We will focus on protecting Microsoft Exchange Online, however many of the controls we introduce are global to Office 365. Exchange Online has numerous controls to help organization protect, discover, and monitor the flow of data through the system. Exchange Online offers traditional services like connection filtering, spam and malware scanning, as well as modern threat protection with Office 365 Advanced Threat Protection (ATP); providing Safe Attachments, and Safe Linking.
Regulating spam and protection
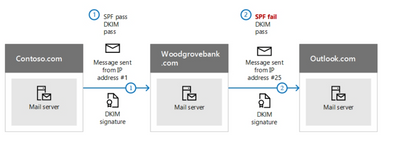
Organizations need to continually protect themselves from spoofing, spam, and phishing. Office 365 provides native support for solutions like Domain Keys Identified mail (DKIM), Domain-based message authentication (DMARC), and Sender Policy Framework (SPF). These solutions are well established technology and can help regulate spam and protect organizations from common attacks.
Figure 7 Overview of DKIM, DMARC, and SPF
Threat intelligence and management
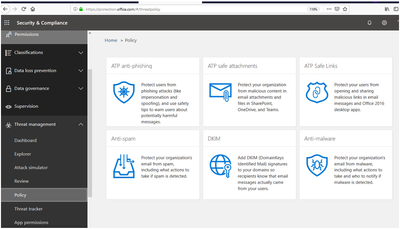
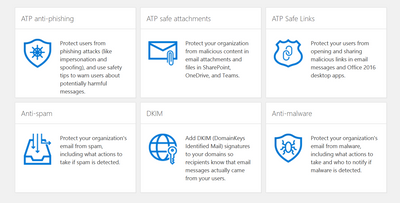
With all the security tools organizations implement to date, Phishing is still one of the most common methods of attack. Office 365 provides built in tools to help organizations configure anti-phishing and anti-malware policies to better protect your organization.
Figure 8 Office 365 Threat Management Policies
User training is a recursive process and Office 365 provides a built-in attack simulator. The attack simulator allows administrators to create content, track, and report on users. This helps organizations identify and find vulnerable users before a real attack impacts your organization.
Figure 9 Office 365 Attack Simulator
Office 365 provides several built-in solutions to help organizations view their threat landscape. Microsoft provides 9 key capabilities under the Threat management section in the Office 365 portal:
- Dashboard
- Investigations
- Explorer
- Submissions
- Attack Simulator
- Review
- Policy
- Threat Tracker
- App Permission
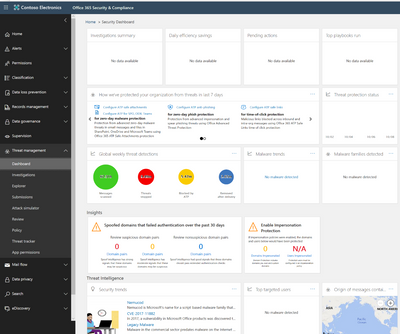
The security dashboard provides an overview of your organizations threat landscape. Microsoft surfaces global attack trends, malware summaries, and several other key indicators for an organization to review and investigate.
Figure 10 Office 365 Threat management dashboard
Signal sharing
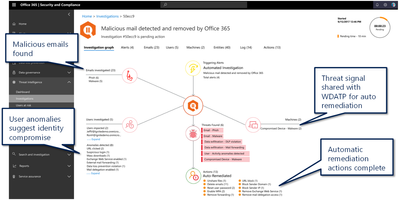
Most organizations bounce between tools attempting to discover which node was infected first after a compromise has occurred. One reason this happens is the lack of signal sharing between tools. Microsoft solutions share signals between services like Office 365 and MDATP. The signal sharing provides security teams a view of the entire kill chain in one location and starts investigating the endpoint immediately. The auto investigation helps expedite the security teams’ tasks by pulling logs and several key data points, from the endpoint, and correlating those events.
Figure 11 Office 365 investigations
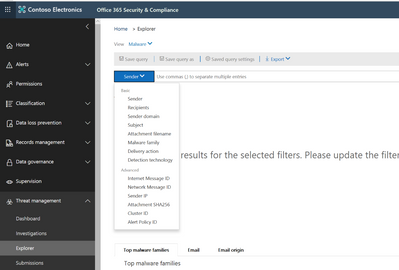
Using Threat Explorer
Dashboards are good visualizations however; security teams need the ability to hunt through data to investigate potential issues. Explorer allows your security team to hunt through your message data looking for SHA hashes, malware, and many other key attributes, to track down potentially malicious payloads.
Figure 12 Office 365 Threat Explorer
Getting a detailed analysis from Microsoft
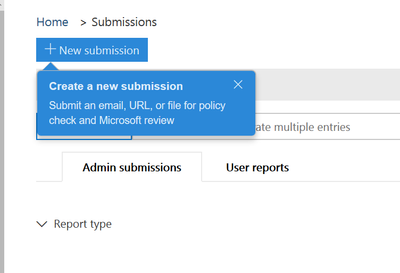
Organizations often find files they believe to be malicious but are uncertain. Office 365 provides the ability to submit messages/files to Microsoft for more detailed analysis. When you submit an email, you get information about any policies that may have allowed the incoming message into your tenant, as well as examination of any URLs and attachments in the message.
Figure 13 Office 365 submission
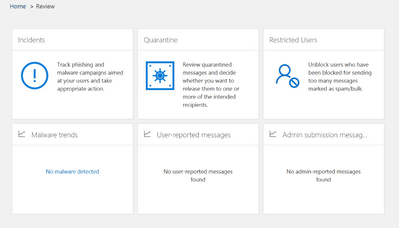
Organizations often create rules and filters that can capture legitimate messages or unintentionally block users. Providing administrators, the ability to review any incidents, quarantined messages, or restricted users is critical to business productivity.
Figure 14 Office 365 Admin Review
Using Advanced Threat Protection (ATP)
Organizations are under constant threat and simple techniques like Phishing happen every day. As attack techniques evolve, so must organization security practices. Office 365 lets your organization create Advanced Threat Protection (ATP) policies to accomplish this.
Figure 15 Office 365 Threat Management Policies
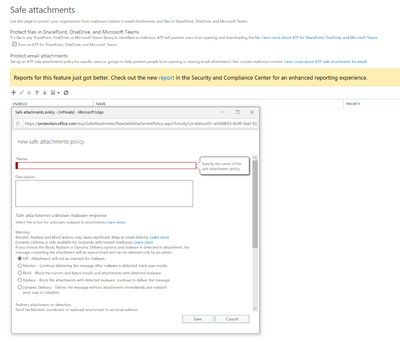
Office 365 ATP has two key capabilities; Safe Links and Safe Attachments. Office 365 Safe Attachments allows organizations to configure policies to "detonate" attachments before delivering files to the user. During this process, Microsoft uses ML and behavioral analytics enriched by the Security Graph to determine if the attachment is malicious. Office 365 ATP policies work across various services like SharePoint, Exchange, Teams and OneDrive to protect the entire platform.
Figure 16 Office 365 Safe Links policy creation setting
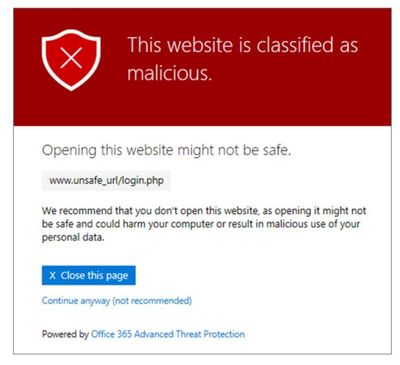
Office 365 ATP helps protect your organization by providing time-of-click verification of web addresses (URLs) with Safe Links policies. Each URL that is embedded in a document, message, or chat, will be run through Microsoft’s threat protection to prevent users from following links to web sites recognized as malicious.
Figure 17 example of Office 365 Safe Links block
Data Protection
When talking about Data Loss Prevention (DLP) or “data leakage”, we know data moves, and quite often moves to cloud services such Box, Google Drive, and other commercial cloud services. Data protection is a constant struggle for IT, and it is only getting harder. In the “Securing Mobile” article we talked about how AIP polices move with the document but what if documents haven’t been labeled and sit outside the corporate boundary. Microsoft has several solutions that work together to help organizations gain visibility and control of your data estate. Each solution provides a key control point for your organizational data from discovery and control to protection.
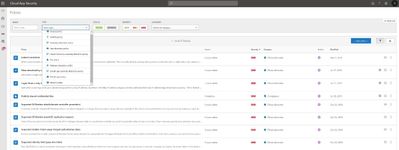
Microsoft Cloud App Security (MCAS) is designed to give insight into how cloud apps are being used in your organization. It provides an at-a-glance overview of what kinds of apps are being used, your open alerts, and the risk levels of apps in your organization. MCAS integrates natively with the Office 365 service to allow organizations to create policies to govern data and access.
Figure 18 Microsoft Cloud App security policy page
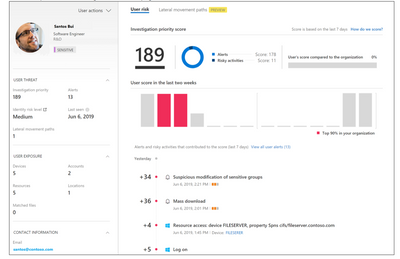
Identifying risk is critical for an organization, especially when it comes to user’s activity. Microsoft believes identity is the new security perimeter and understanding user activity is imperative. Azure ATP is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Azure ATP, Microsoft Cloud App Security (MCAS), and Azure AD Identity Protection adds powerful User and Entity Behavioral Analytics (UEBA) capabilities into Microsoft’s Threat Protection solutions.
Figure 19 MCAS User Behavior Analysis
In this scenario, we demonstrated how an organization can use the native Microsoft cloud tools to help protect the Office 365 platform. There are numerous features this article did not cover like legal hold, regulatory compliance, and more that are native to Microsoft’s cloud platform. Be on the lookout for the next blog of the series where you’ll learn more about auditing and logging.