This post has been republished via RSS; it originally appeared at: Azure Data Explorer articles.
Network isolation is a requirement shared by many of our security-conscious customers. After a private preview phase of over one yeare we are very happy to announce that deployment of an ADX into a virtual network is now generally available.
The intent is the ability to isolate the network traffic and limit the attack surface for Azure Data Explorer and their corresponding communications. This means that the customer can block all traffic originating from non-ADX network segments and assure that only traffic from known sources to reach ADX endpoints. This includes traffic originating on premises or outside of Azure, with an Azure destination and vice versa.
Service Tags to management endpoints help to isolate a virtual network down to specific IP addresses necessary for such traffic (in- and out-bound).
How to start?
Before you deploy your Azure Data Explorer int a VNet make sure that you read our HowTo guide. This will help you to understand all necessary dependencies in order to make sure that the deployment will be successful.
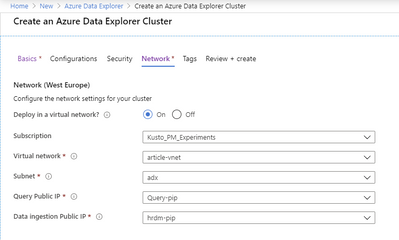
Afterwards go to the Azure portal and choose to deploy an ADX. Make sure you configured the new "Network" section and you are all set.
Instructions and templates on how to deploy it via ARM can be found here.
Troubleshooting
In the last couple of months we were in close collaboration with our private preview customers and worked on improving the overall experience including the documentation. Moreover we invested into a detailled troubleshooting guide which will teach you on how to find issues faster.
A highlight is for sure the diagnostics enpoint which can be called with an armclient: