This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Through the rapidly growing adoption of Azure PaaS offerings, customers need to access data and services privately and securely from their networks grow exponentially. This is more pronounced in hybrid environments – on-premises, cross-cloud and cross-platform. We have been incrementally adding support for network isolation through VNet Service Endpoints and Firewall rules. Today, we’re excited to announce the public preview of Azure Private Link support for Azure Service Bus Premium tier.
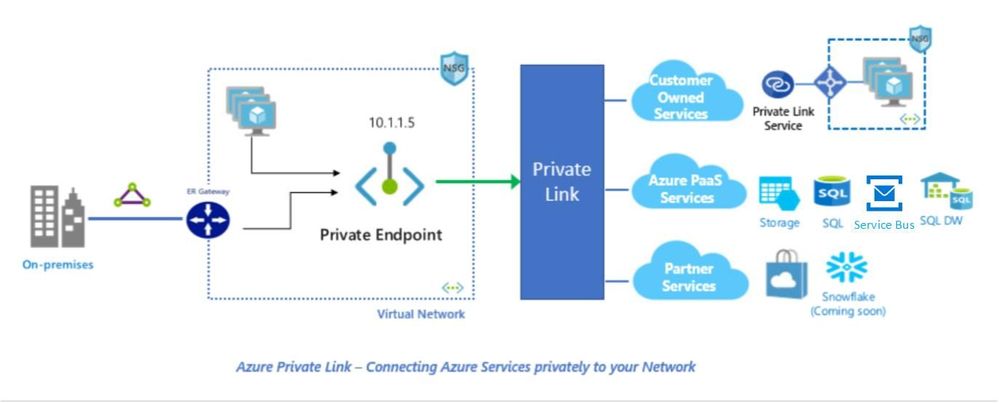
Azure Private link is a secure and scalable way for Azure customers to address their Azure Service Bus namespace privately from within their Azure Virtual Network. The technology is based on a provider and consumer model where the provider and the consumer are both hosted in Azure. A connection is established using a consent-based call flow and once established, all data that flows between the service provider and service consumer is isolated from the internet and stays on the Microsoft network. There is no need for gateways, network address translation (NAT) devices, or public IP addresses to communicate with the service.
Azure Private Link essentially brings Azure services inside the customer’s private VNet. The Service Bus namespace can be accessed using the Private IP address just like any other resource in the VNet. This significantly simplifies the network configuration by keeping access rules private.
Benefits of using private link for Azure Service Bus
- Data exfiltration protection: With Private link for Azure Service Bus, customers can now set up network access controls like NSG to restrict access to the private endpoint. Individual Azure PaaS resources are then mapped to specific private endpoints. Since a malicious insider can only access the mapped PaaS resource (for example an Azure Service Bus namespace) they cannot use some other resource for data exfiltration.
- Private on-premises access: Since the Azure Service Bus namespace is mapped to private IP address in the customer’s VNet, they can be accessed via Azure ExpressRoute private peering. Additionally, Microsoft peering is also supported for VNets that are not on the customer’s private network.
This effectively means that the data will traverse a fully private path from on-premises to Azure. The configuration in the corporate firewalls and route tables can be simplified to allow access only to private IP addresses. With Private link, customers can enable cross-premises access to private endpoint using Express Route(ER), private peering, Microsoft peering or VPN tunnel. They can subsequently disable all access via public endpoint and not use the IP-based firewall. - Simple to setup: Azure Private Link for Azure Service Bus is simple to setup with minimal networking configuration. Connectivity works on approval call flow and once a Service Bus namespace is mapped to a private endpoint, the connectivity works out of the box without any additional configurations on route tables and Azure Network Security Groups (NSGs).
How to setup private link for Azure Service Bus
To learn more about how to setup Azure Private Links for Azure Service Bus Premium tier using PS, CLI or the Azure Portal, please refer to the below documentation.
Note: Private endpoints is supported for Azure Service Bus only in the Premium tier.