This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
In the big wide world of security, it can be hard to know what Azure resource settings give you the best possible security posture. Organisations like the USA-based National Institute of Standards and Technology and the Center for Internet Security publish security best practices, but how do you translate those into your Azure deployments?
You might immediately look to Azure Policy for this.
Azure Policy does include built-in Policy Initiatives (a group of policies) for a number of security and compliance recommendations, including HIPAA, PCI, NIST, UK NHS and more. With Azure Policy, you can audit your resources to see areas of non-compliance or you can enforce settings when resources are added or modified.
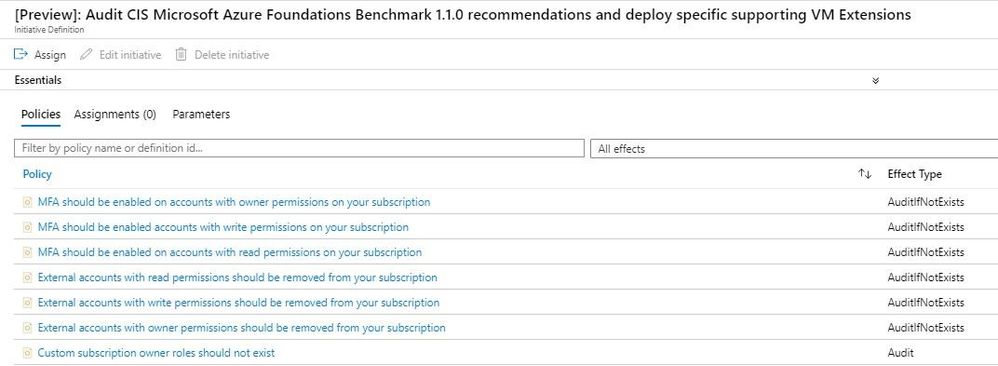
CIS Microsoft Azure Foundations Benchmark recommendations have recently been added to Azure Policy, as the initiative "[Preview]: Audit CIS Microsoft Azure Foundations Benchmark 1.1.0 recommendations and deploy specific supporting VM Extensions" You can find it in the Azure Portal or download the definition from GitHub. This Policy Initiative includes the relevant individual Azure policies that map directly to CIS Microsoft Azure Foundations Benchmark recommendations.
These include:
Recommendations regarding the security of accounts that can access your Azure resources
Recommendation: Ensure that multi-factor authentication is enabled for all privileged users
Policies:
- MFA should be enabled on accounts with owner access on your subscription
- MFA should be enabled on accounts with write permissions on your subscription
Recommendations that check your resources are able to be monitored for security issues
Recommendation: Ensure that 'Automatic provisioning of monitoring agent' is set to 'On'
Policy:
- Automatic provisioning of the Log Analytics monitoring agent should be enabled on your subscription
Recommendation: Ensure ASC Default policy setting "Monitor OS Vulnerabilities" is not "Disabled"
Policy:
- Vulnerabilities in security configuration on your machines should be remediated
Recommendations regarding security settings for specific resource types
Recommendation: Ensure that 'Secure transfer required' is set to 'Enabled' (for storage accounts)
Policy:
- Secure transfer to storage accounts should be enabled
Recommendation: Ensure that 'Data disks' are encrypted
Policy:
- Disk encryption should be applied on virtual machines
Recommendation: Ensure web app is using the latest version of TLS encryption
Policies:
- Latest TLS version should be used in your API App
- Latest TLS version should be used in your Function App
- Latest TLS version should be used in your Web App
Note: One of the recommendations maps to the policy "Security Center standard pricing tier should be selected." Each Azure subscription comes with Azure Security Center at the free tier, but upgrading to the Standard tier extends your security management capabilities. Click here for more details on the Standard tier and click here for pricing.
For a full list of the recommendations and mappings, visit https://docs.microsoft.com/azure/governance/blueprints/samples/cis-azure-1.1.0/control-mapping?WT.mc_id=itopstalk-blog-socuff
And the CIS Benchmarks checklist for securing Microsoft Azure can be found here: https://www.cisecurity.org/benchmark/azure/
Also note: Each control is associated with one or more Azure Policy definitions.
These policies may help you assess compliance with the control; however, there often is not a 1:1 or complete match between a control and one or more policies. As such, Compliant in Azure Policy refers only to the policies themselves; this doesn't ensure you're fully compliant with all requirements of a control. In addition, the compliance standard includes controls that aren't addressed by any Azure Policy definitions at this time. Therefore, compliance in Azure Policy is only a partial view of your overall compliance status. The associations between controls and Azure Policy definitions for this compliance blueprint sample may change over time. To view the change history, see the GitHub Commit History.
So far so good - Azure Policy has us covered, right?
Yes it does, but there may be a better way to deploy this into your environment - using Azure Blueprints!
Azure Blueprints have a couple of features that Azure Policy does not. With Azure Blueprints, you can version and comment on the blueprint assignment as you apply it to a scope. Resource locks can also be enforced by a Blueprint and cannot be removed, even by a subscription owner.
And you can also include other things (known as artifacts), like RBAC settings, templates or required resource groups that will also be applied as part of the Blueprint.
For the CIS Microsoft Azure Foundations Benchmark Blueprint, you can use this sample as a starting point to build your own comprehensive security blueprint, to which you can also add the RBAC settings etc that your organization has identified as important.
What's next?
Applying the blueprint and the associated policies is just one part of managing the security of your Cloud resources. The policies will deploy in "Audit" or "AuditifNotExists" mode and will not change any settings, so you need to check the Azure Policy Compliance dashboard (inside the Azure Portal) to see which existing resources do not meet the policies you've applied, and remediate those resources to bring them into alignment.
For more information:
- Read the announcement blog: New Azure Blueprint for CIS Benchmark
- Learn how to deploy the CIS Microsoft Azure Foundations Benchmark blueprint sample: https://docs.microsoft.com/azure/governance/blueprints/samples/cis-azure-1.1.0/deploy?WT.mc_id=itopstalk-blog-socuff