This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
This article is authored by Priscila Viana
Follow these easy steps for connecting your Threat Intel feed on Azure Sentinel and take full advantage of this solution focused on empower your Blue Team.
Pre-Requisites
You should have an Active Subscription on Azure Sentinel with an active Log Analytics workspace. On IBM X-Force, follow the steps provided in the “Obtaining an API Key and Password” section in the URL - https://api.xforce.ibmcloud.com/doc/#introduction to create a new API Key and Password for the registered user on this service.
API Root and Collections ID
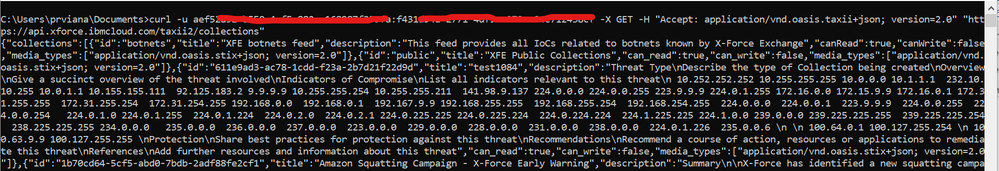
Navigate on https://api.xforce.ibmcloud.com/doc/#TAXII2_get_taxii2 section and you’ll see a Curl example like this, which return us the API Root information:
curl -u {apikey:password} -H "Accept: application/vnd.oasis.taxii+json; version=2.0" https://api.xforce.ibmcloud.com/taxii2
Check if you got a successful response like this:
Now, if you go to: https://api.xforce.ibmcloud.com/doc/#TAXII2_get_taxii2_collections you’ll another example via curl, where you easily can extract the collections IDs you need to make the connection:
curl -u {apikey:password} -H "Accept: application/vnd.oasis.taxii+json; version=2.0" https://api.xforce.ibmcloud.com/taxii2/collections
Check if you got a response like this bellow:
In this scenario, we’ll choose one of the Collections IDs returned by the command above. But you can customize with your needs.
Add the Connector
Azure Sentinel provides interesting ways to ingest your Threat Intel feed. You can do this via: Threat Intelligence Platforms connector, Threat Intelligence TAXII connector or you can easily build a custom connector for this. In this scenario, we’ll connect via Threat Intelligence TAXII connector.
For more detailed information about others connectors, I do recommend you read the article: https://techcommunity.microsoft.com/t5/azure-sentinel/bring-your-threat-intelligence-to-azure-sentinel/ba-p/1167546
Now that we’ve all information we need, let’s add the Connector.
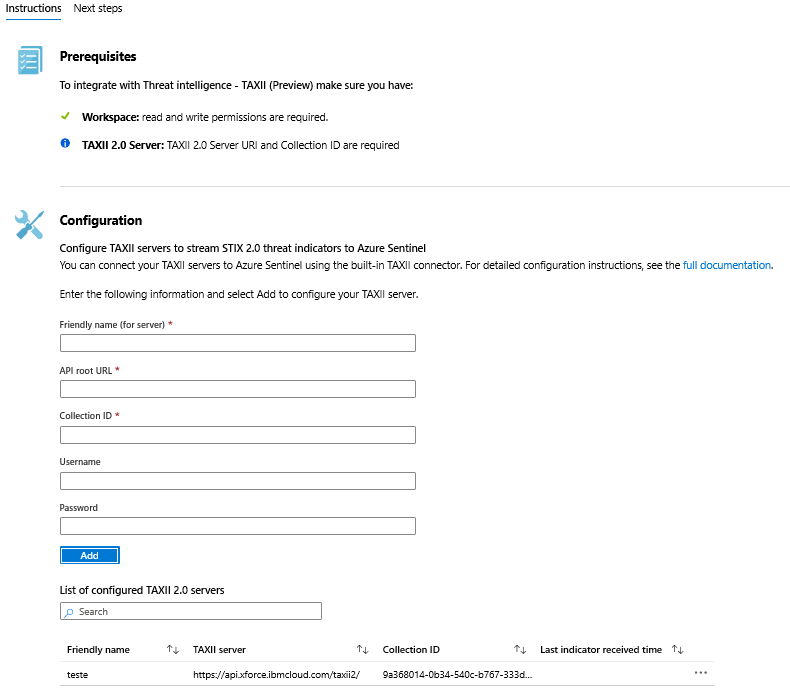
On Azure Sentinel go to: Data Connectors >> Threat Intelligence (TAXII) >> click Open connector page
Fill-out the connector page with the information:
|
Friendly name: write any name |
|
TAXXI server: https://api.xforce.ibmcloud.com/taxxi2/ |
|
Collection ID: put any collection ID you grab on the earlier step (in this example, I’ve chosen 9a368014-0b34-540c-b767-333d32d66924) |
|
Username and password: put the API key and password you’ve got on the earlier steps |
Finally, click Add button. After a few seconds, you’ll see the server being listed below:
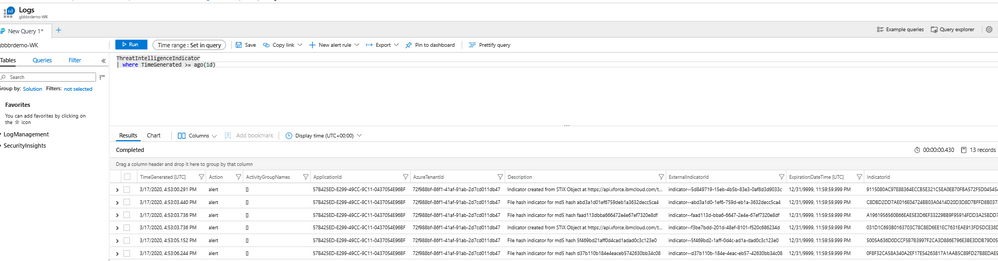
Ok. Now, since we want to be sure everything is running smoothly, take the advantage of the built-in queries provided by the solution and execute as the example below:
ThreatIntelligenceIndicator
| where TimeGenerated >= ago(1d)
We can see the events being ingested on Azure Sentinel, but we need to enable the Analytics Rules related this Threat Intel Connector correlating them with our existing infrastructure Data connectors (Office365, Azure AD, Syslog, SecurityEvents, etc) in order to trigger Incidents.
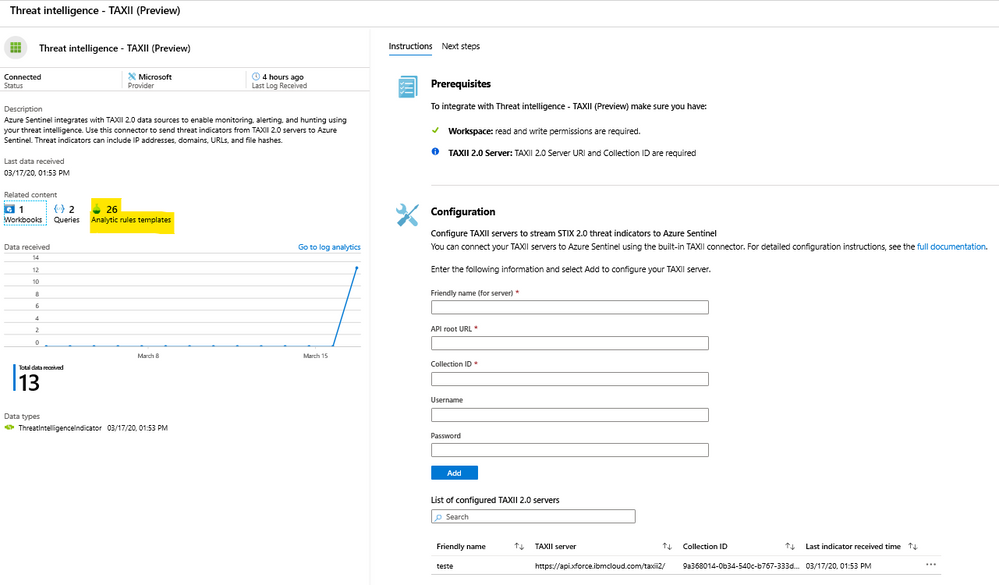
To enable this, come back to Threat Intel connector page and open it.
You’ll see in the description pane, the information regarding 26 built-in rules templates that can be enabled to create related incidents
Create the Analytics rules
Create rule for each one of the Threat Analytics information that you want to correlate. For this, check what rule is most appropriate for what you want and click create rule:
Tip: Note that each rule have at least two Data Sources (in Data Sources column). One for the Threat Intel we’ve just added and another for the related use Case. For instance: If I need to correlate the Threat Intel information with my Office365 activities, I need to have Office365 Data connector connected on my Azure Sentinel workspace.
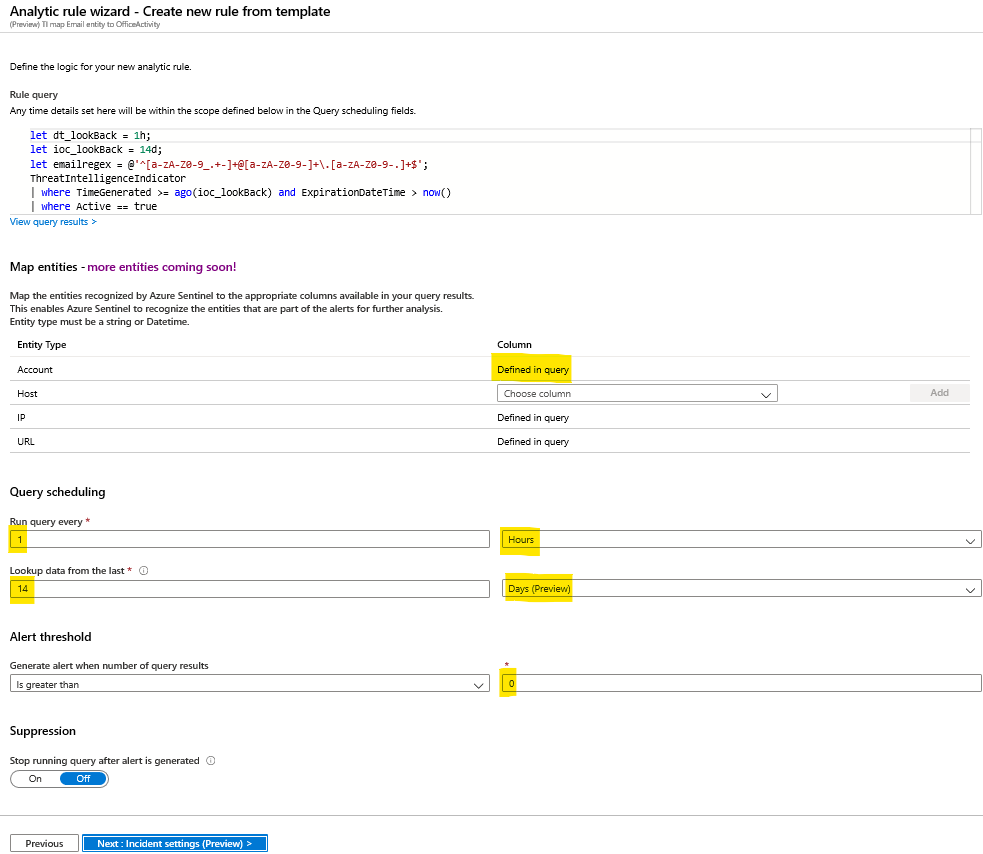
After clicking Next, you’ll be assisted by rule wizard process creation. Adjust the frequency, lookback data and threshold for this schedule rule. All KQL rule is already automatically filled-out in the Rule query section. Click Next.
Another cool thing you can take advantage of is the Alert aggregation feature on Azure Sentinel. As best-practice, for this scenario, be sure this feature is enabled.
Finally, you can attach an Automated response everytime the incident is triggered, using the Playbooks feature. Since this could extend this article, let’s take this in another opportunity.
That’s all. Basically, now you have your connector enabled and running, I do recommend explore Workbooks feature for a management overview of what’s is happening.
Workbooks
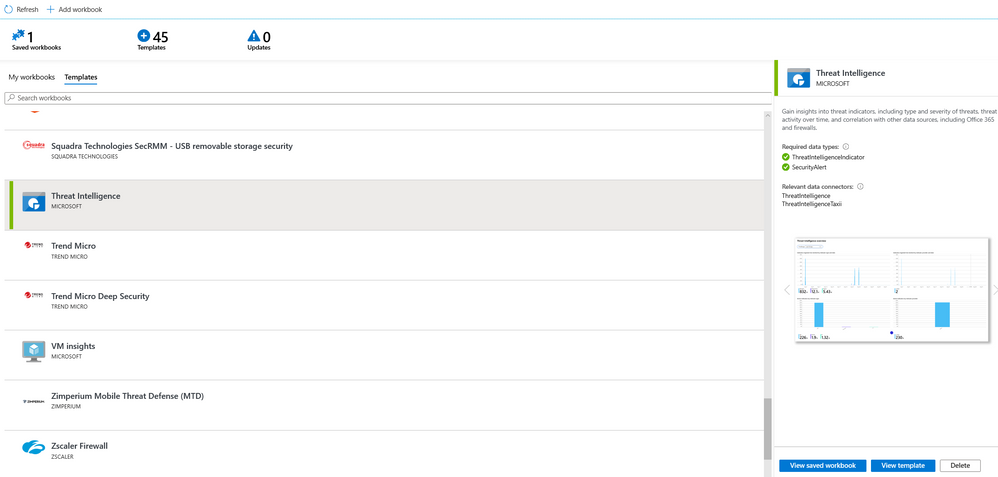
Azure Sentinel provides couple of built-in Workbooks for most used SOC scenarios. In this example, we’ll use “Threat Intelligence” from Microsoft, on which you can build you own using this built-in as a template.
On Azure Sentinel go to: Workbooks>> Threat Intelligence >> click Save button then, click View saved workbook
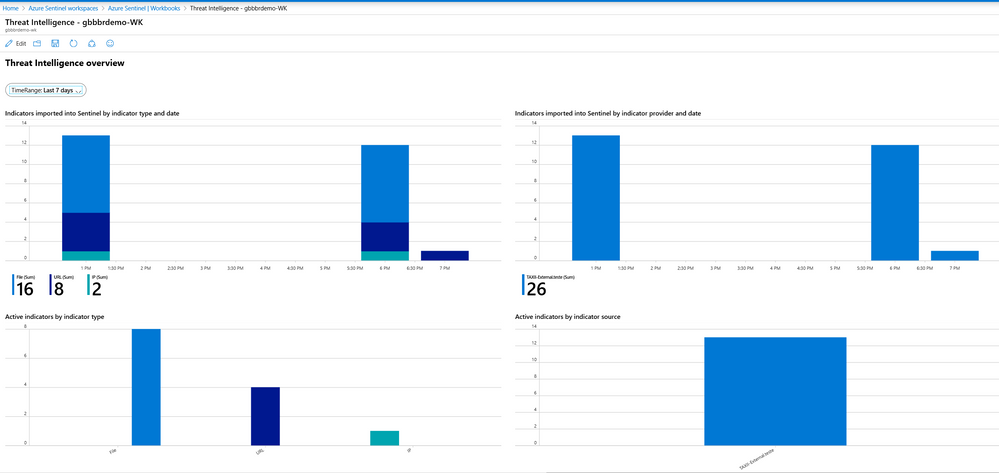
Note that this is a dynamic dashboard, meaning that if you click on a specific indicator, the graph will be automatically updated to reflect this.
Hope you enjoy!.