This post has been republished via RSS; it originally appeared at: Azure Active Directory Identity Blog articles.
Howdy folks,
Today we’re announcing the public preview of custom role management in the Azure portal, making it easier for you to customize the permissions you grant your users or applications to access Azure resources. Adelle Dimitui, one of our program managers on the Identity team, has written a guest blog post with additional details. You’ll find her blog post below.
As always, we’d love to hear any feedback or suggestions you may have. Please let us know what you think in the comments below or on the Azure AD feedback forum. If you have more detailed insights, you can also fill out Adelle's feedback form.
Best regards,
Alex Simons (Twitter: @Alex_A_Simons)
Vice President of Program Management
Microsoft Identity Division
--------------------------------
Hi everyone!
I’m excited to share some details on a new experience we are bringing to the Azure portal, which allows you to manage custom roles that can be used to grant permissions to Azure resources. This is an evolution of the current experience only available in the command-line and Azure Resource Manager API.
Many of you are familiar with Role Based Access Control (RBAC) in Azure, but if you need a quick refresher, please read What is RBAC for Azure resources. Azure RBAC provides a set of built-in roles which can be used to delegate permissions to your users and applications, restricting the amount of access they have to your resources. If a built-in role provides too much or too little access, you can create a custom role with your desired set of permissions. That way, we can ensure your users and apps operate with least privilege!
Let’s explore the new experience
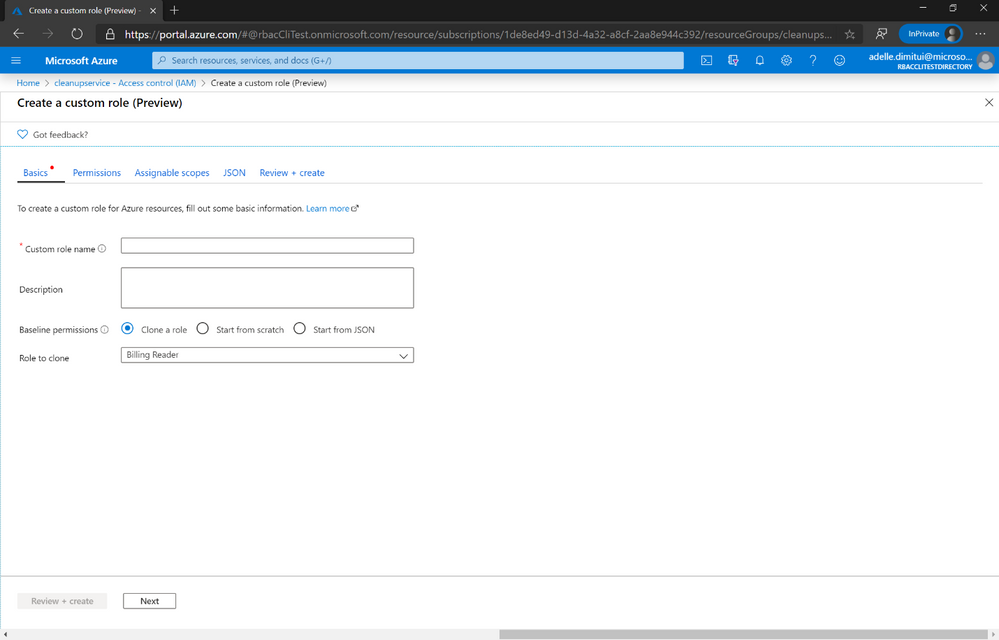
When you are ready to create a custom role in Azure, you start out by picking one of these options:
- Clone a role: Clone an existing Azure RBAC role from within your Azure Active Directory tenant, and copy over its permissions
- Start from scratch: Start from an empty list of permissions, then use our selectors to choose permissions and assignable scopes
Start from JSON: Upload a JSON file or use our JSON editor to write out the attributes of your custom role
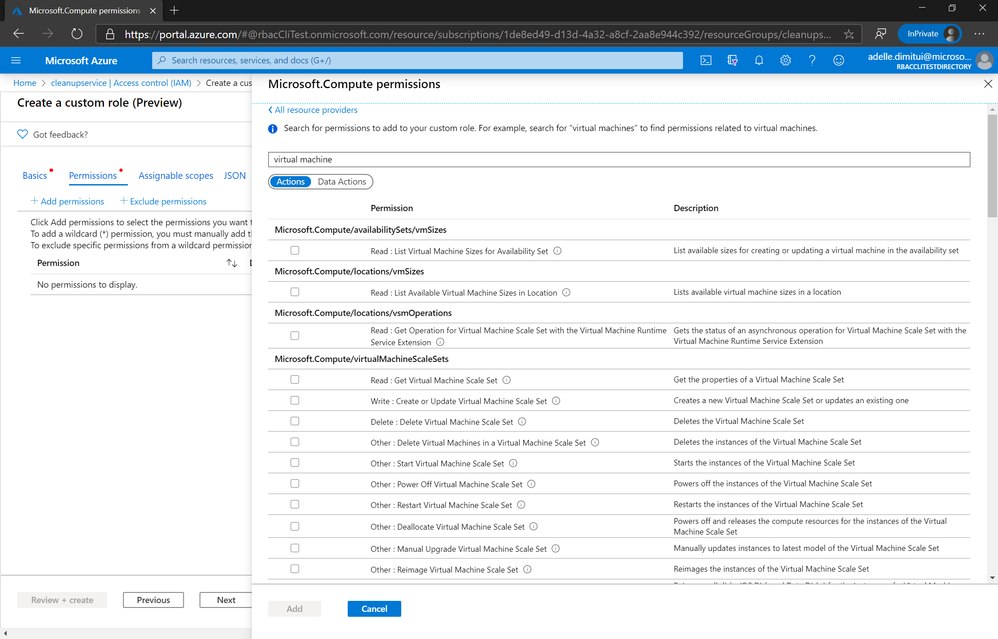
Next, you can determine what permissions are suitable for this role.
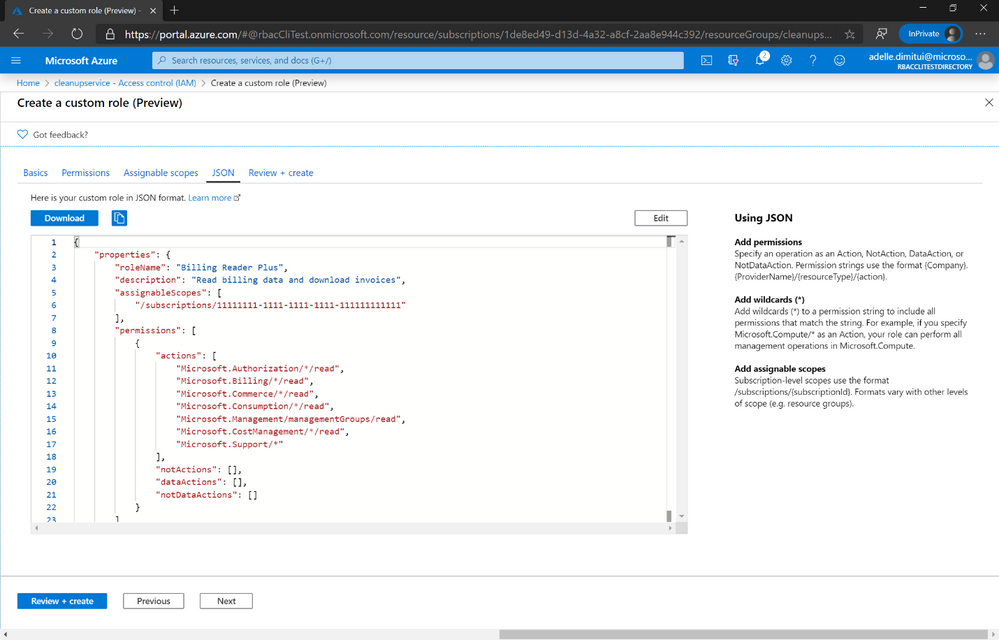
You can even switch to the JSON editor to make more changes before completing the creation process!
So how do you get started?
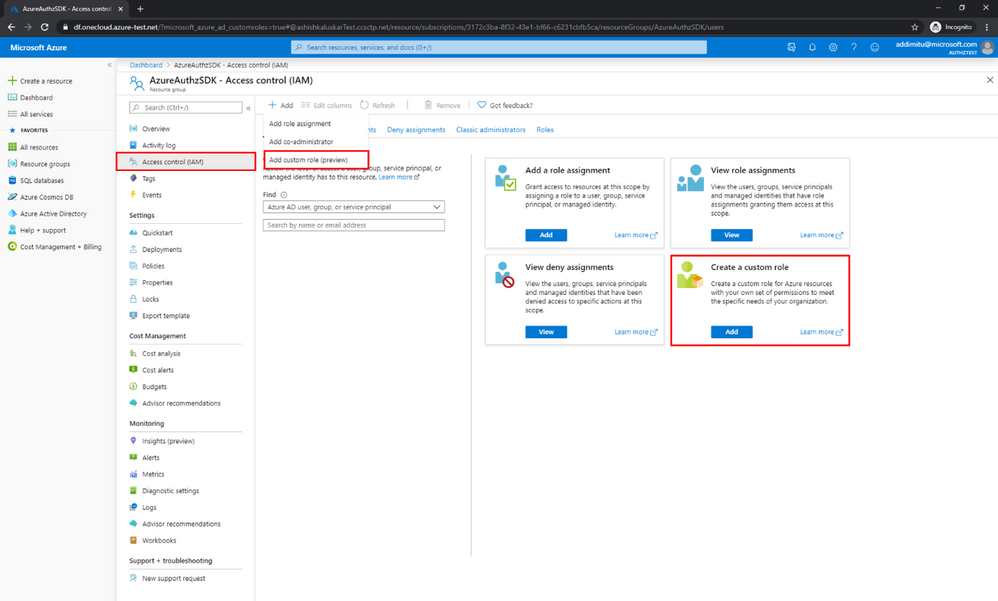
To get started, sign into the Azure portal, navigate to a subscription or resource group, then select the Access control (IAM) blade. From there, click the Create a custom role launch point to try the new experience!
For more detailed steps on how to use the new experience, see our custom role docs.
Let us know your feedback!
To provide detailed feedback on the experience, click here to fill out our feedback form.
We highly encourage you to fill out this form. We greatly value your insights, big and small, and everything you tell us will help us make our products better for you and the rest of our Azure customers!
Best regards,
Adelle Dimitui (Twitter: @AdelleDimitui)
Program Manager
Microsoft Identity Division