This installment is part of a broader series to keep you up to date with the latest features in Azure Sentinel. The installments will be bite-sized to allow you to easily digest the new content.
While the primary function of a SOC is providing situational awareness through the detection, containment, and management of security threats; this is coupled with the responsibility to track metrics to measure performance and to make changes to increase SOC efficiency.
From our Microsoft CDOC, we have learned that the metrics you choose to measure has a significant effect on the behaviors and outcomes of security operations. Focusing on the right measurements will help drive continuous improvement in the right areas that meaningfully reduce risk.
Today, we are happy to release the improved incident closing experience!
This feature is meant to help customers track more detailed information on why incidents are closed. Being able to measure these metrics can allow you to enforce alert quality across your SOC, tune out false positives, and adjust processes to improve prioritization and focus.
Today, incident’s status can be either New, In Progress or Close. When changing a status to ‘Close’ you have an option of specifying whether the incident was a False Positive or a True Positive.
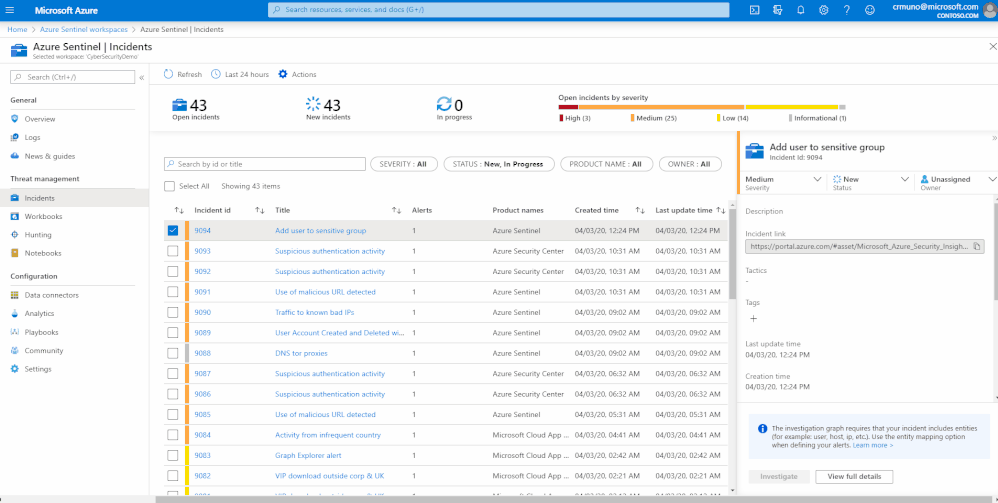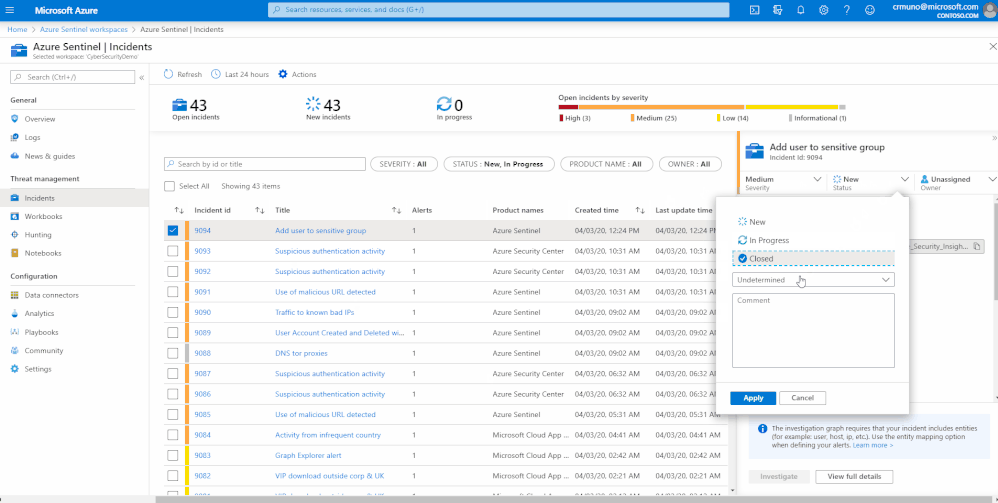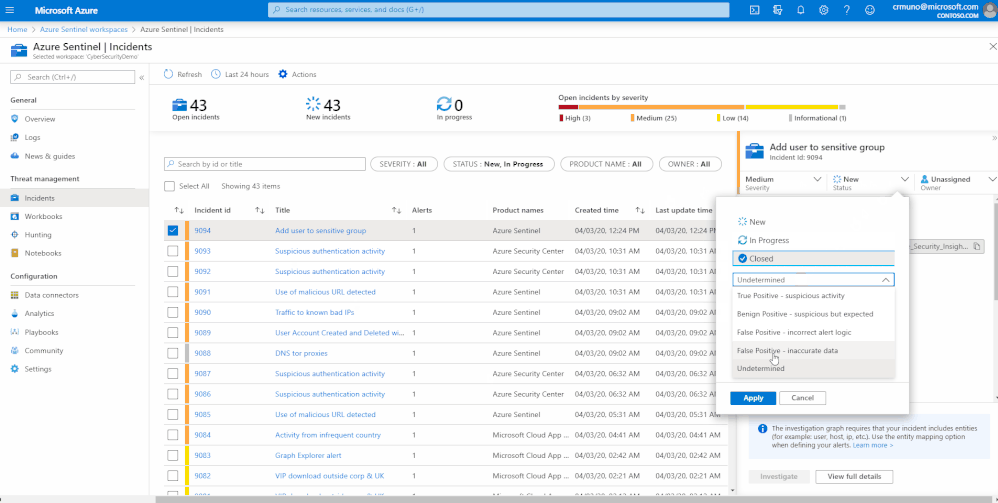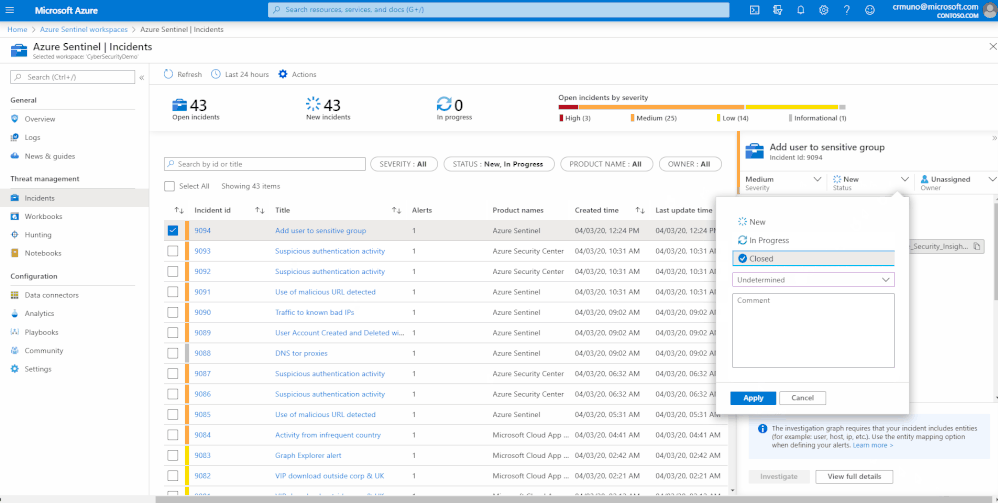
In order to collect more information on the incident closing, we made this a mandatory field and provided a set of closing reasons that are based on researchers and customer references:
- True Positive, suspicious activity
- Benign Positive, suspicious but expected
- False Positive, incorrect alert logic
- False Positive, inaccurate data
- Undetermined
We hope this feature will help customers better tune their rules and measure their SOC’s performance and will help us get more detailed information on our own detection’s.
Get started today!
We encourage you to use the improved incident closing experience in your environment.
Note – The official documentation will be available in 1-2 weeks.
Try it out, and let us know what you think!