This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
This installment was written as a collaboration between
Today’s cybersecurity landscape is filled with a variety of evolving threats, demanding new ways to protect your assets and stay on top of emerging security threats.
In the second installment of this blog we focus on the second integration point with SOC Prime, that is, the ability to advance your security analytics with SOC Prime’s extensive threat detection marketplace. In Part 1, we covered the steps to convert Sigma rules to Azure Sentinel using SOC Prime’s Uncoder.io tool.
Today, we cover the steps to enable the integration with SOC Prime’s threat detection marketplace that will enable you to consume detection rules into Azure Sentinel with a single click. In the next installment of this blog series, we will cover the steps to consume hunting queries out of SOC Prime.
What is SOC Prime Threat Detection Marketplace (TDM)?
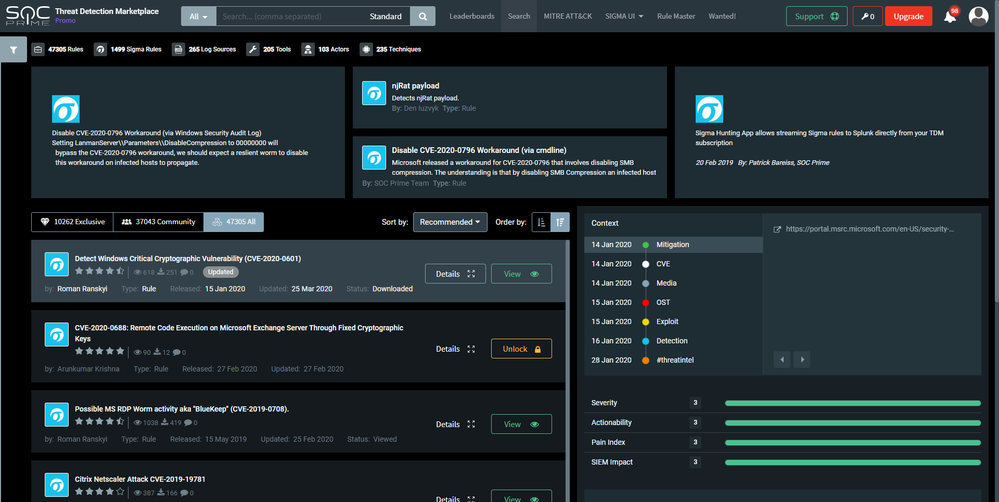
SOC Prime’s Threat Detection Marketplace (TDM) was developed by security incident responders for fastest threat detection content delivery to CISO’s, SOC Managers and SOC Analysts. Threat Detection Marketplace provides actionable and relevant use cases to defend against cyber threats and to enhance SOC operations significantly. It has about thousands saved searches, queries, and correlation rules that improve the efficiency of ArcSight, Elastic, QRadar, and Splunk, and now also Azure Sentinel. Select use cases that were already built and tested for the technologies you have in your organization and save the time of your security experts that is wasted on re-inventing Use Cases.
Access to interactive MITRE ATT&CK exploration section and global cyber attack statistics allows you to determine the most relevant cyber security threats and measures to protect your organization from them.
Get more information about Threat Detection Marketplace: https://my.socprime.com/en/tdm/
Azure Sentinel Queries and Rules
SOC Prime’s intuitive platform enables you to filter and consume rules for your desired platform, in our case - Azure Sentinel rules or queries.
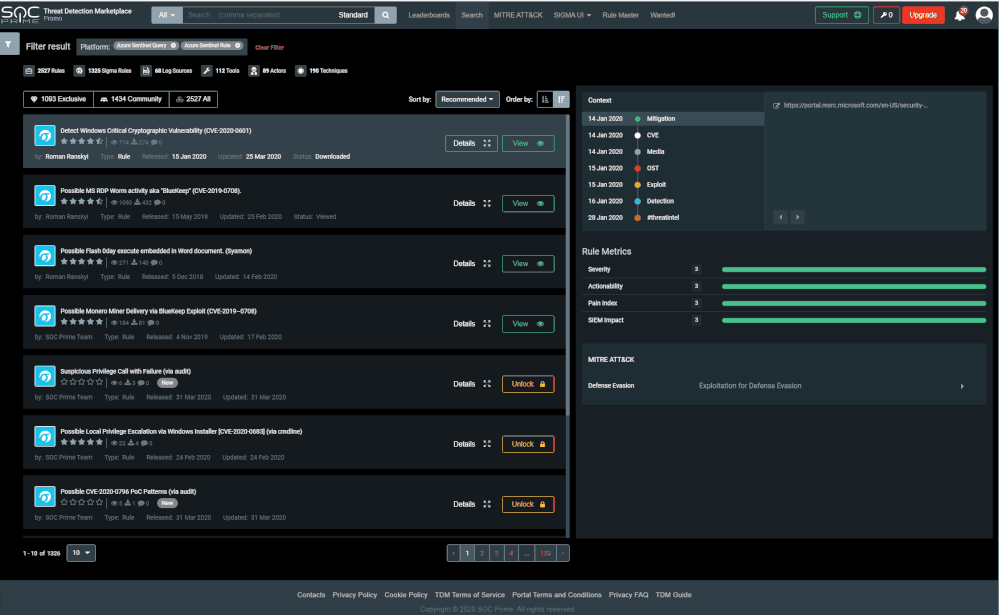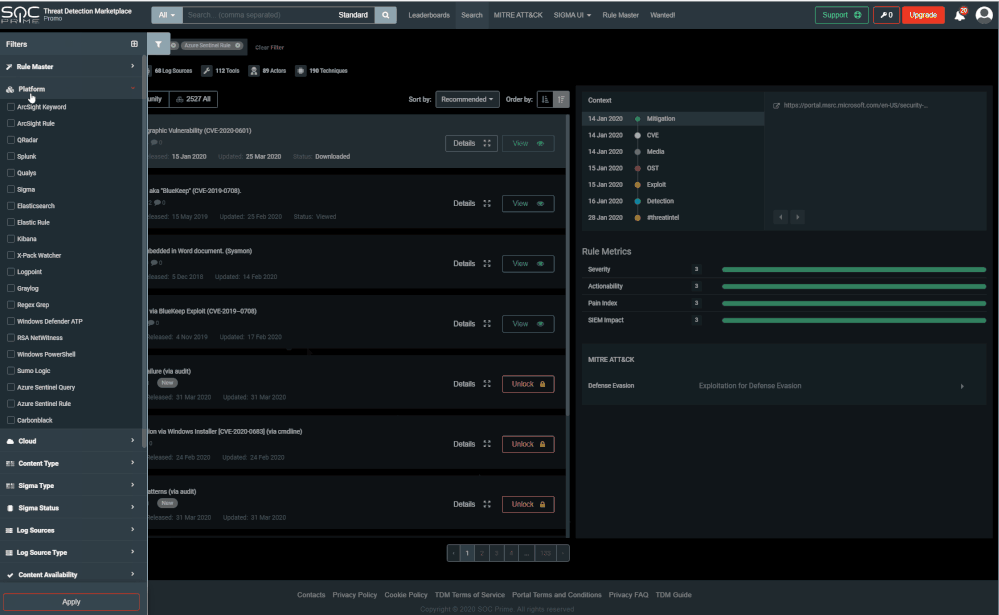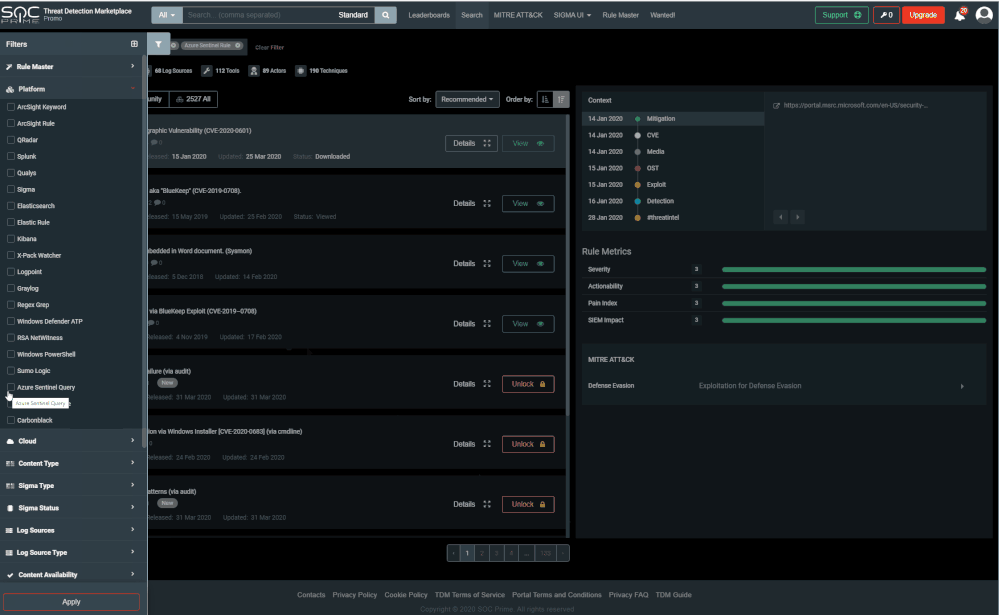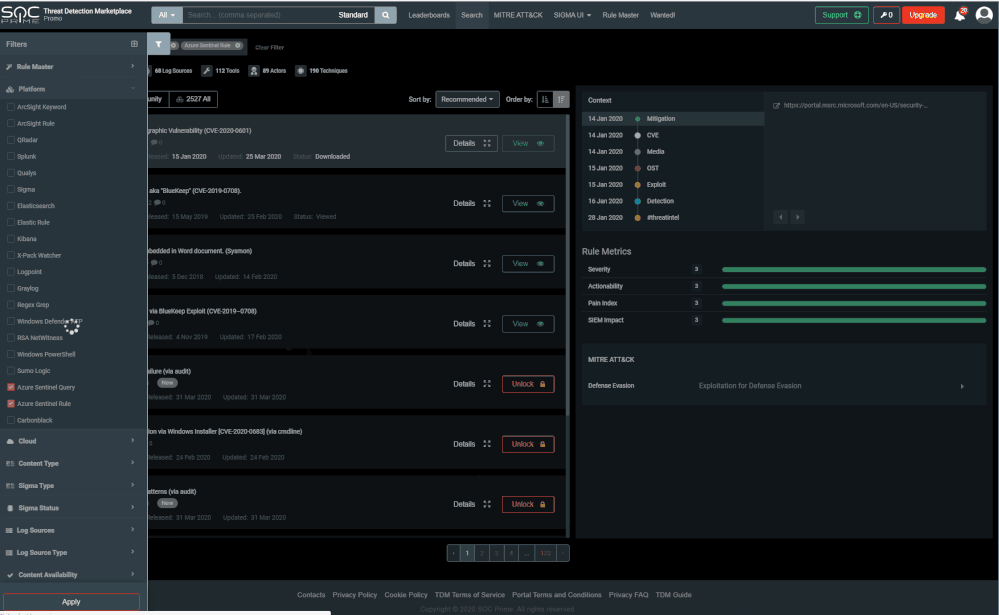
To do so, click on the filter button on the top left, click on “Platform”, then select “Azure Sentinel Query” or “Azure Sentinel Rule”. Queries provide bare-bone KQL queries. Use them in different Azure Sentinel modules including hunting, workbooks or logs. Rules provide a full Azure Sentinel analytics scheduled query rule as a JSON file. Copy the fields from the file to the Azure Sentinel rule creation wizard, or use the Azure Sentinel API to upload the file definition as is. Or better! Deploy the rules directly from TDM to your Azure Sentinel workspace as described in the next section.
Configure the parameters required to deploy rules
In order to enable automatic deployment, you need to configure TDM with just a few parameters. First click on your “Account”, then click on “Microsoft Azure Sentinel API” from the dropdown.
After clicking on the “Microsoft Azure Sentinel API” button, the configuration page for the API will load.
There is a set of parameters that need to be configured for the Microsoft Azure Sentinel API Configuration:
- Client ID,
- Client Secret,
- Tenant ID,
- Subscription ID,
- Resource Group,
- Sentinel Workspace
In the following sections we will learn how to obtain those parameters.
Register an Azure AD App
To receive a client secret, you must register an application in Azure AD App Registrations
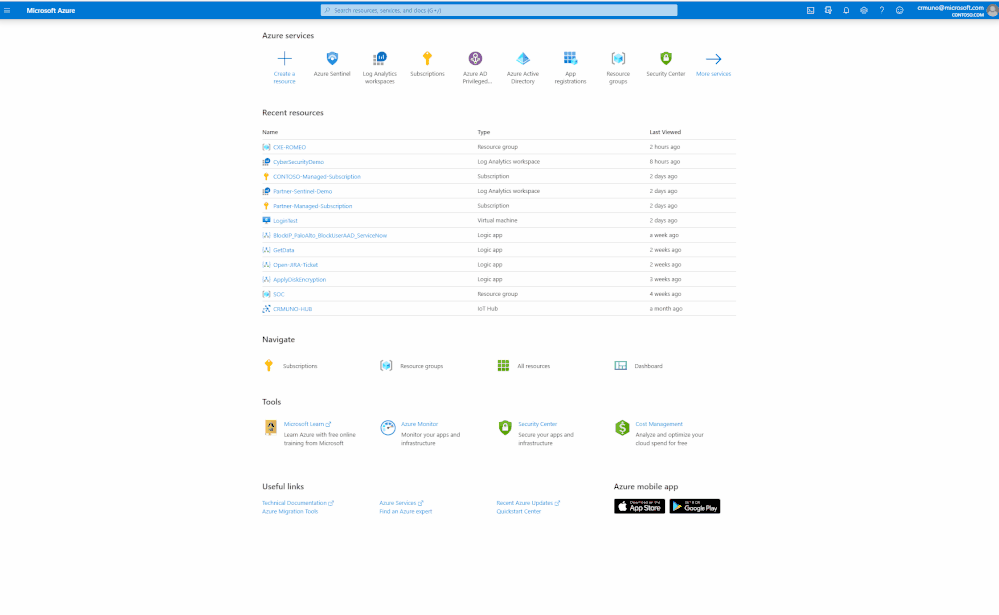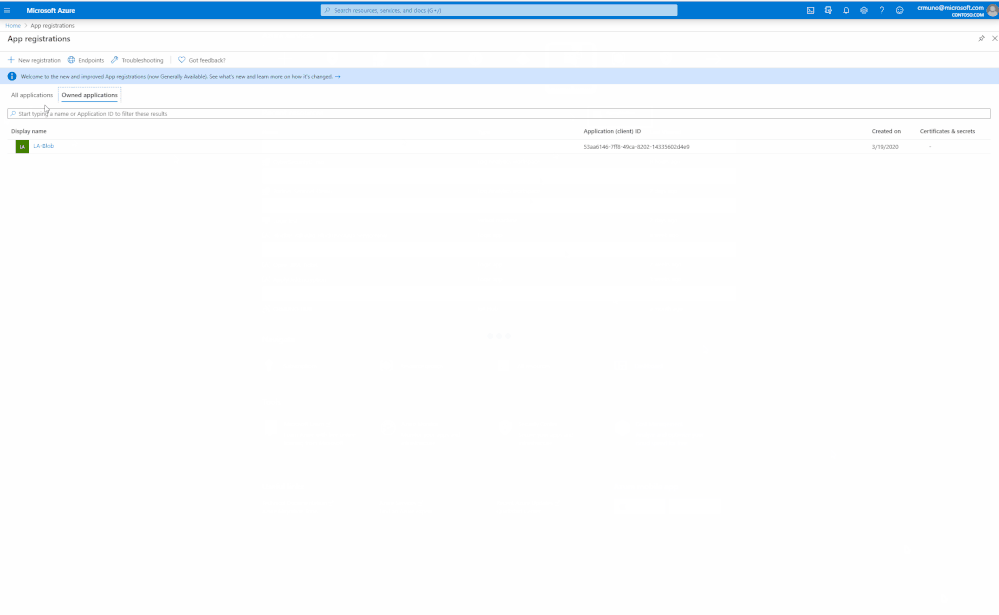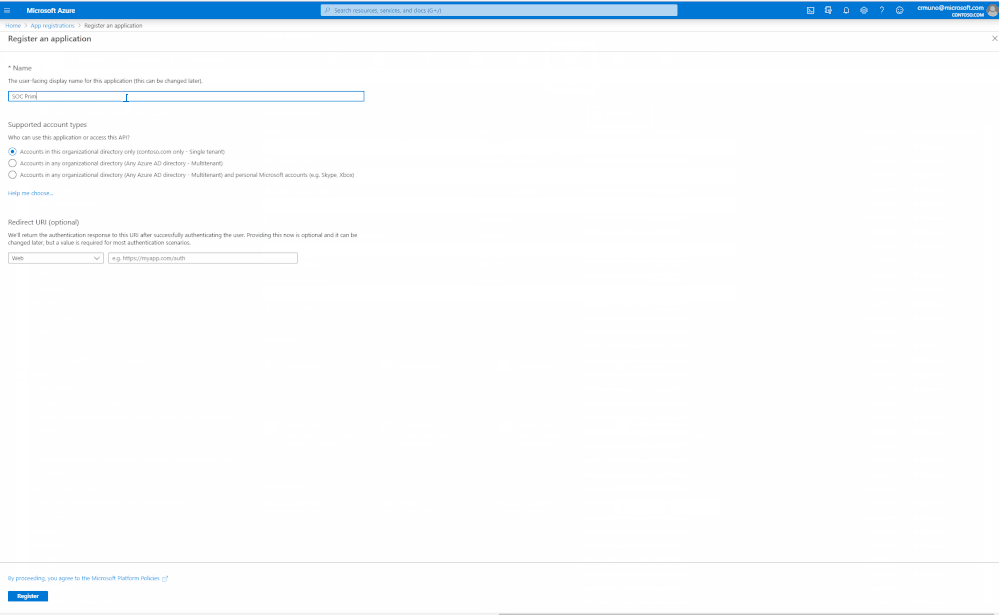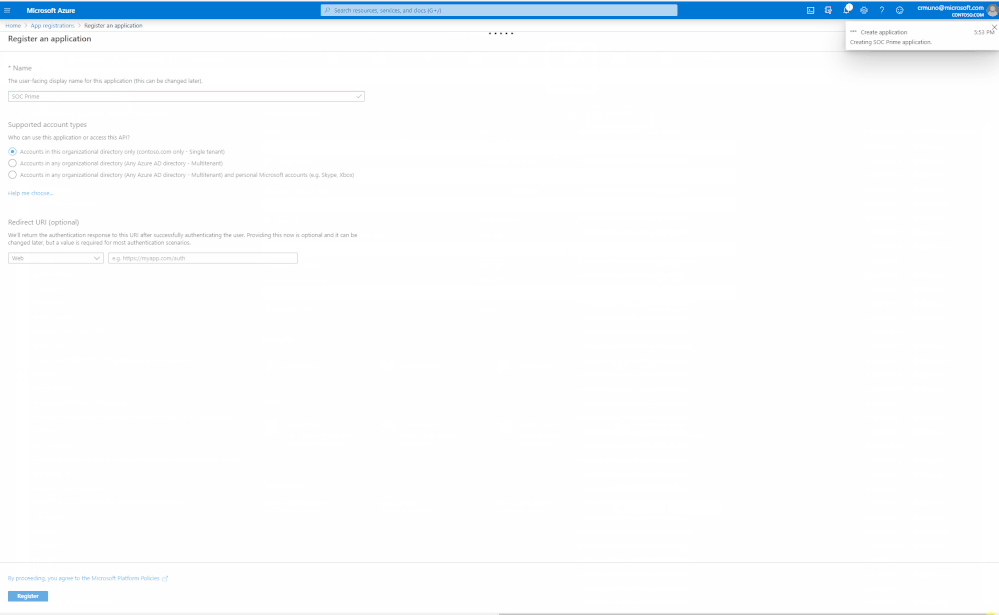
- Login to Azure AD and at home screen, click on App Registrations, and select New Registration
- Specify a name for the application and click Register, for example SOC_Prime_Sentinel
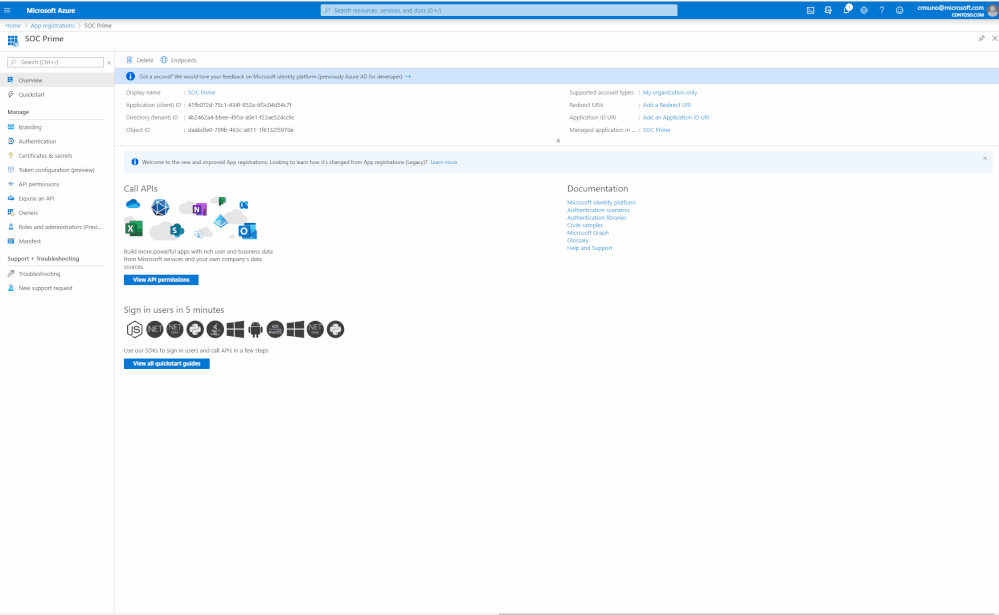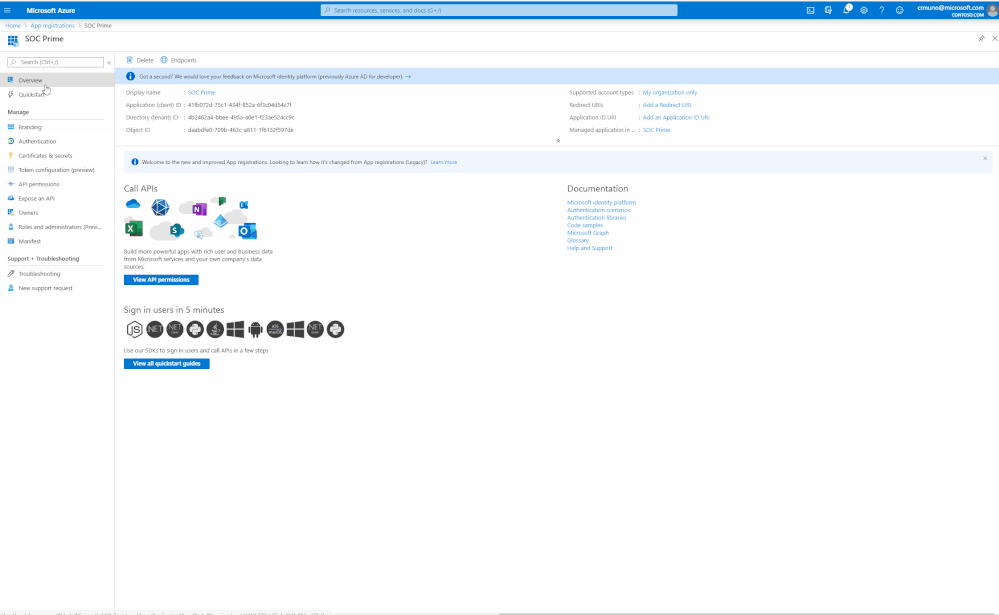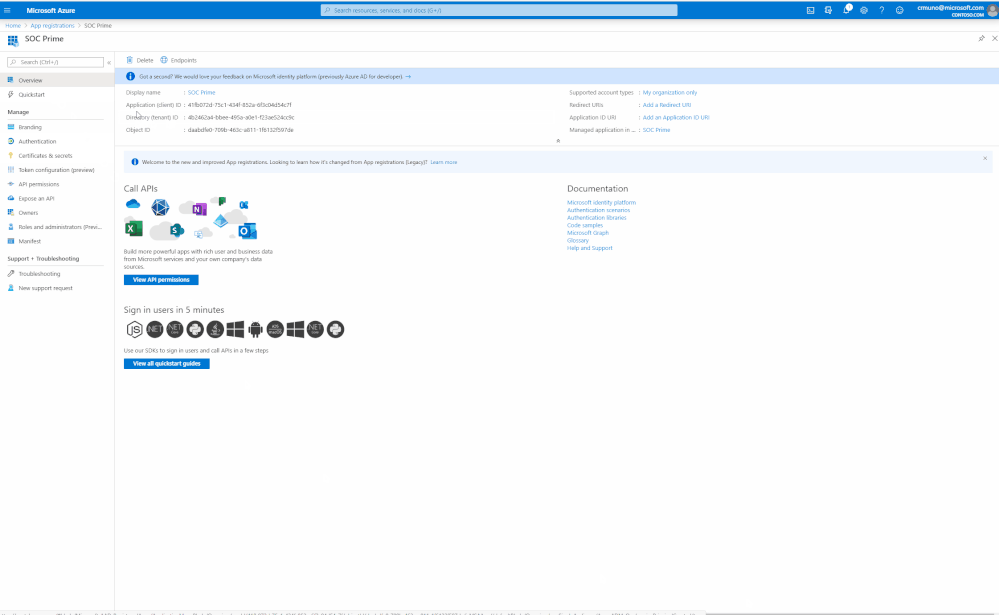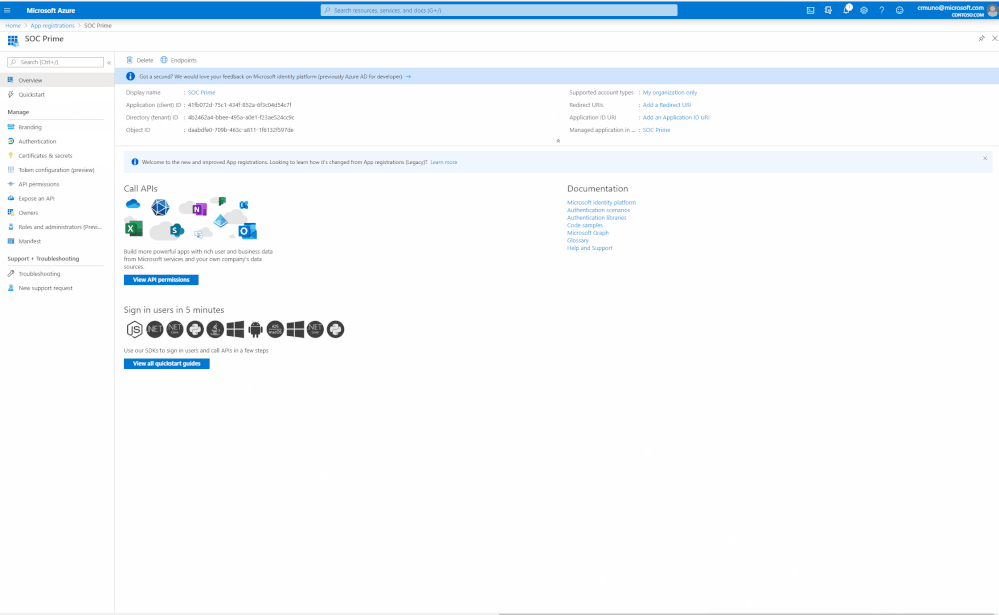
3. Navigate to the created application page, you will be automatically navigated to the 'Overview' section.
4. Copy the 'Tenant ID' & 'Client ID', which you will use as parameters (3) and (1) respectively in the "Microsoft Azure Sentinel API" in TDM.
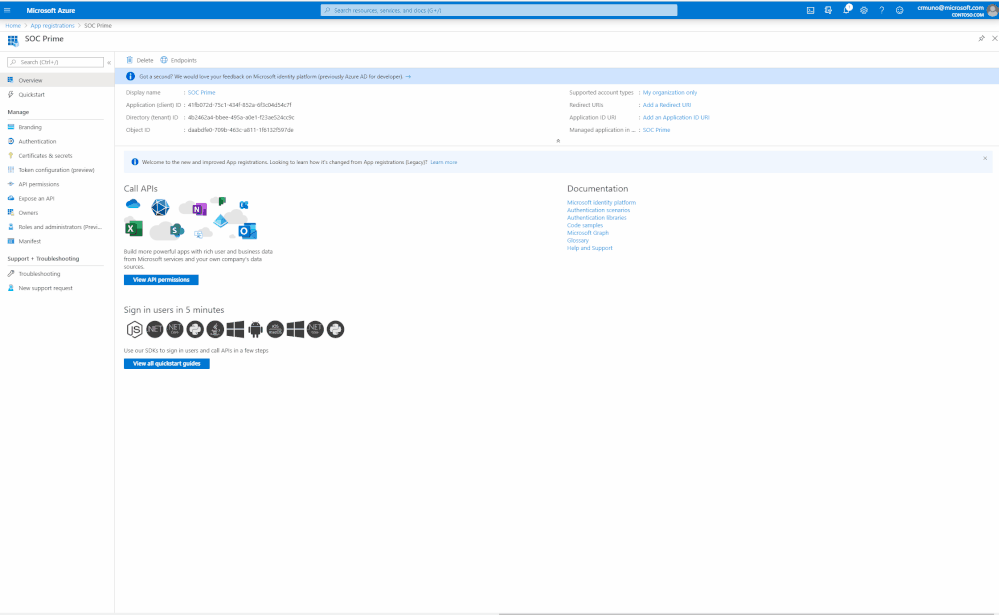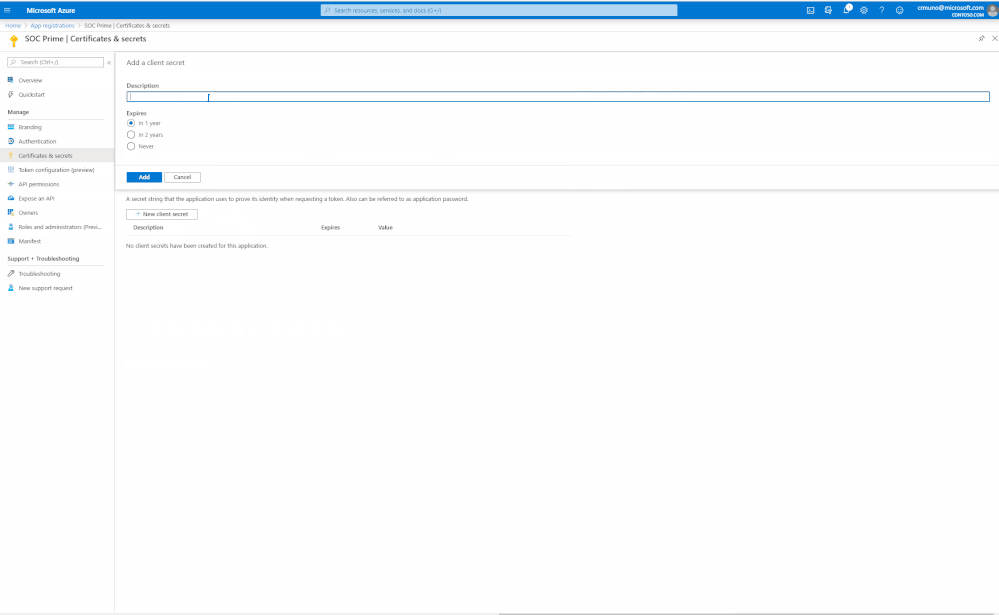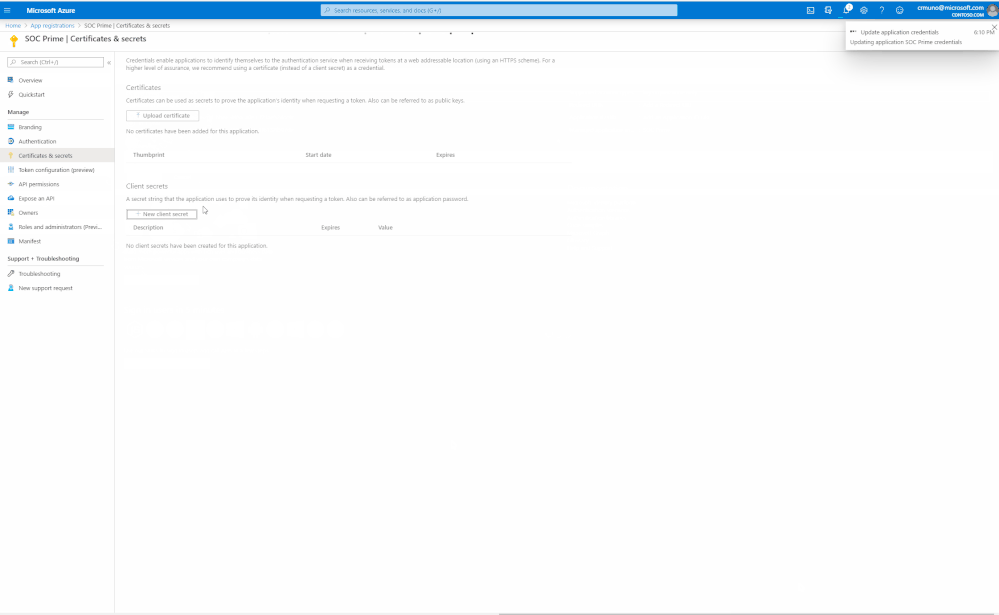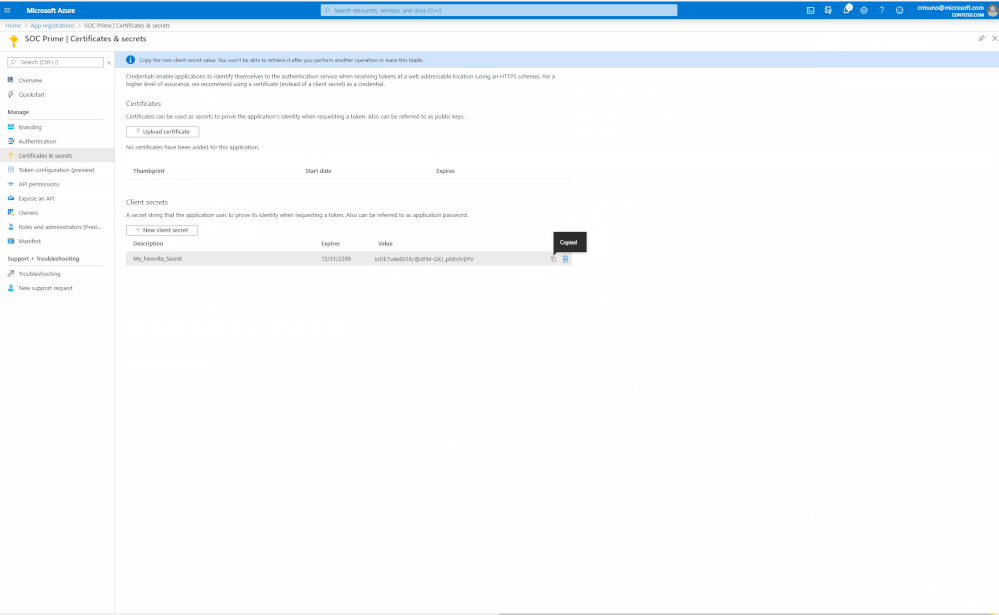
5. Then, navigate to the’ Certificates & Secrets’ section and register ‘Client secrets’. To do this, click the 'New client secret button', type the description and set the Expire.
6. You will then be directed to the ‘Certificates & Secrets’ page where the client secret is created. Use it as the parameter (2) in the "Microsoft Azure Sentinel API" in TDM.
IMPORTANT - Click copy next to the new secret and store it somewhere temporarily. You cannot come back to get the secret once you leave the blade.
Find your subscription, resource group and workspace IDs
- Browse to your Azure Sentinel workspace and select settings from the left side menu.
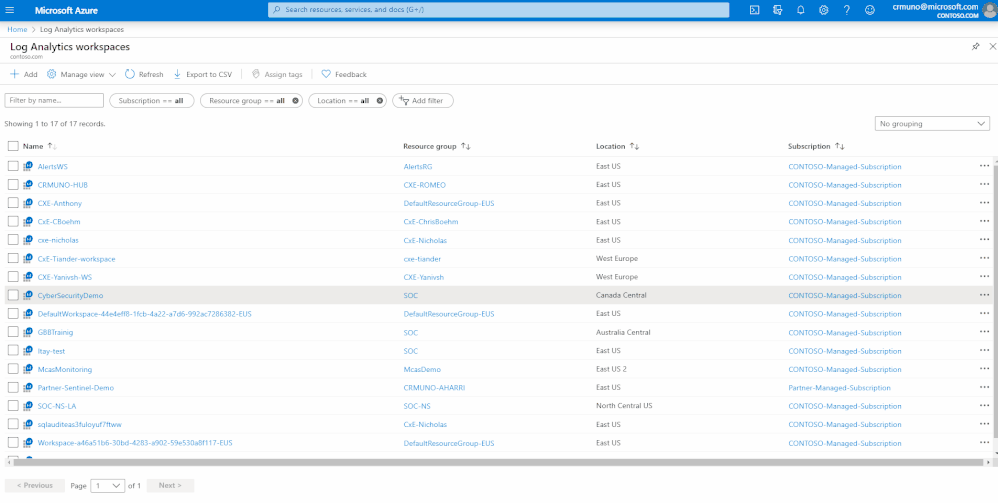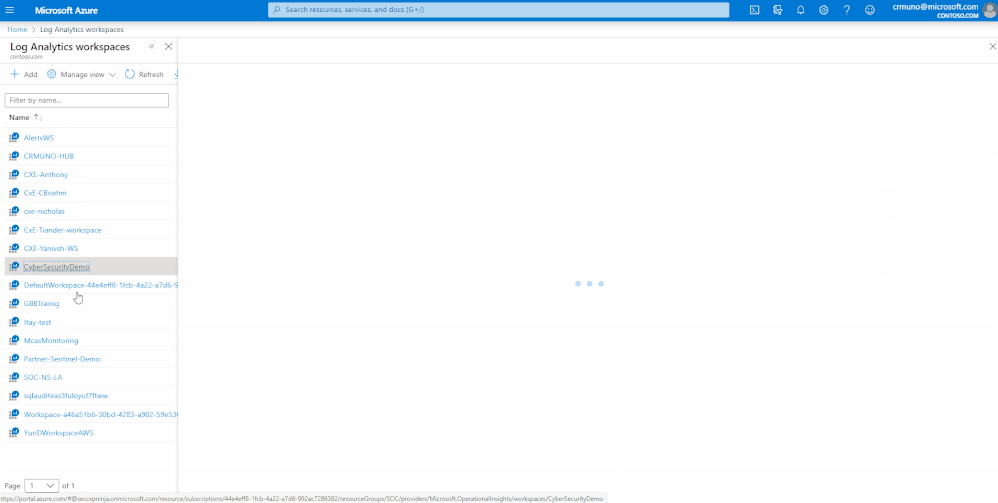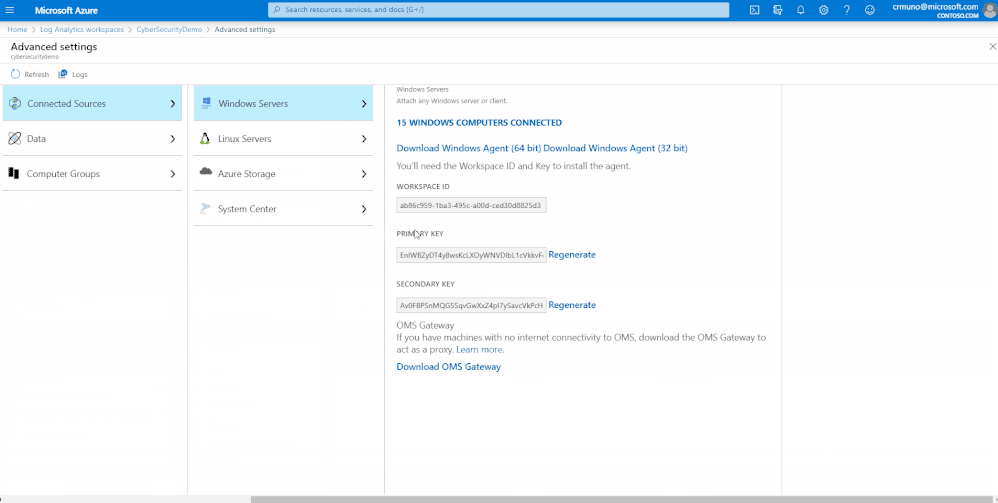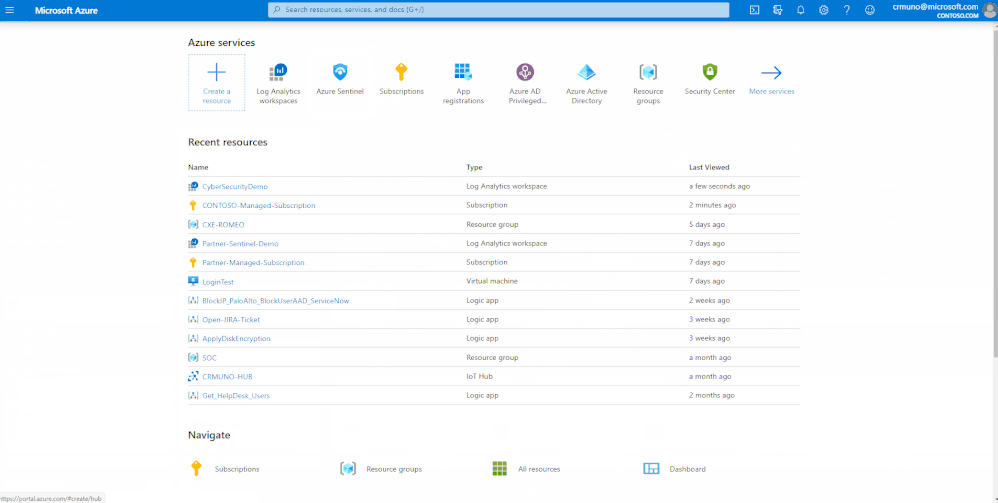
- Select the "Advanced Settings" tab. Copy the subscription ID, resource group, and workspace ID as parameters (4), (5), and (6) respectively in the "Microsoft Azure Sentinel API" in TDM.
Assign Permissions to the registered App
To allow the application to write and create rules , we need to provide the app the permissions to do so.
- Navigate to the Azure subscription in which includes the Azure Sentinel workspace
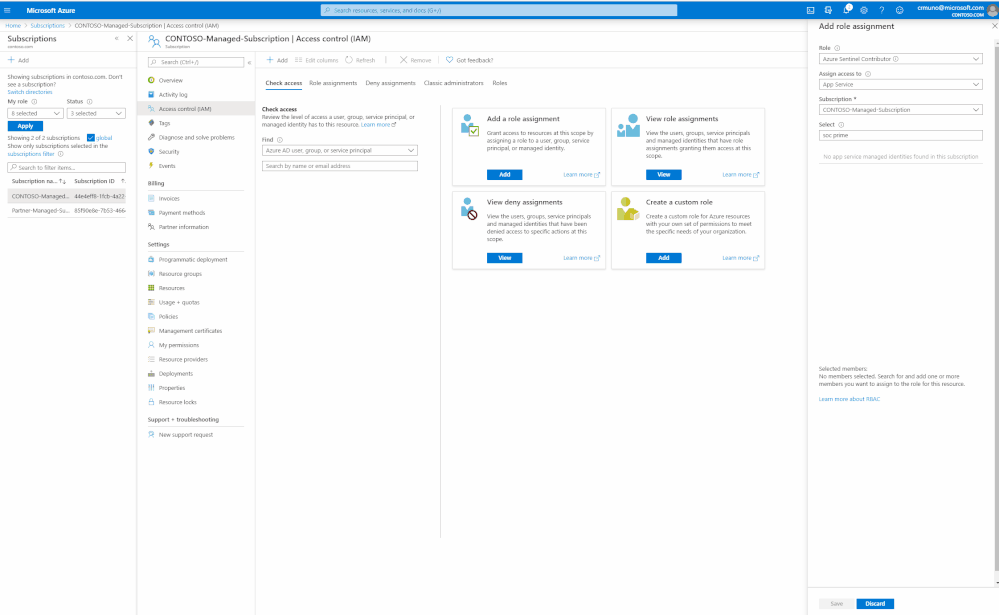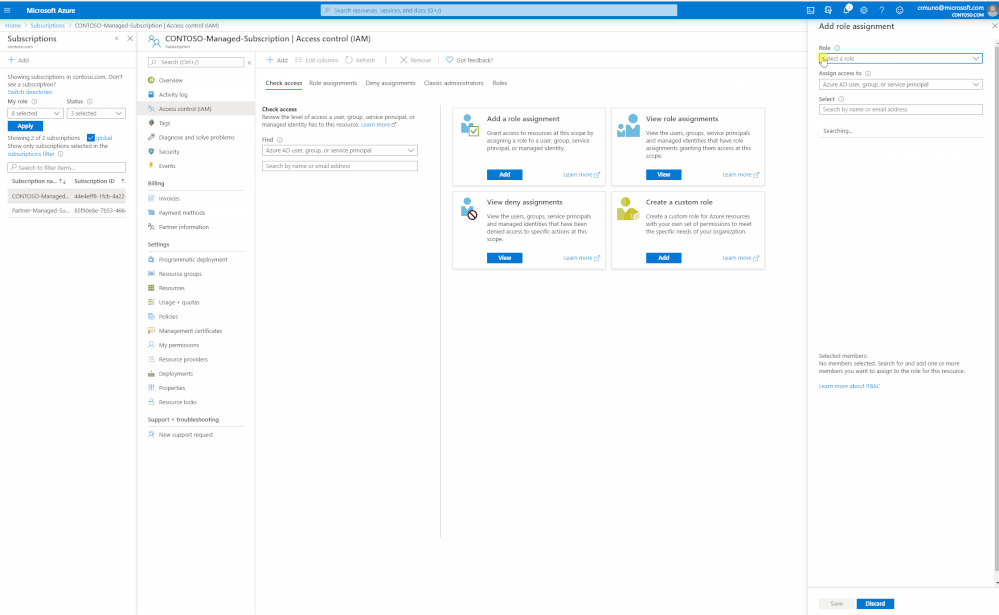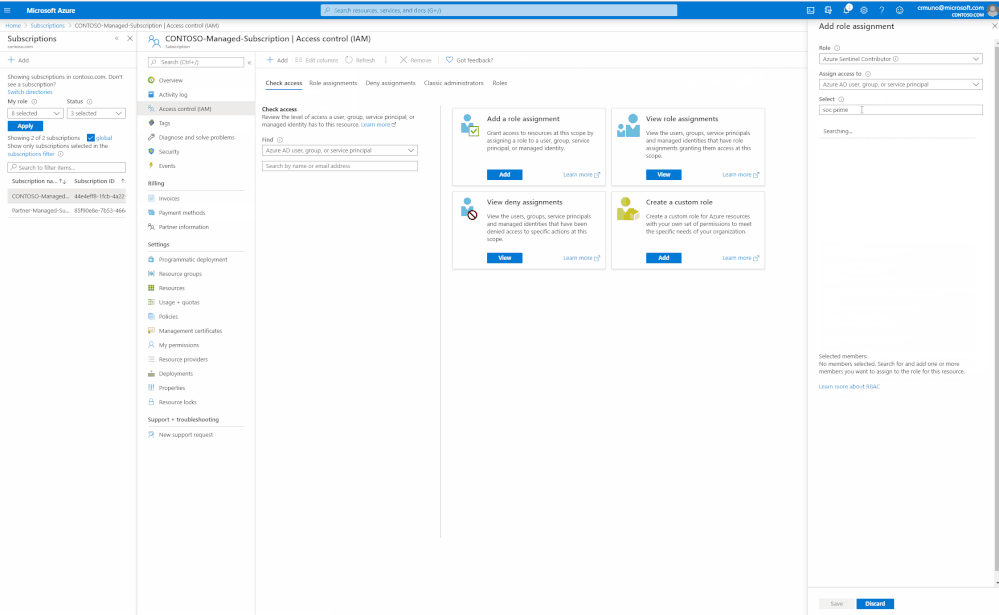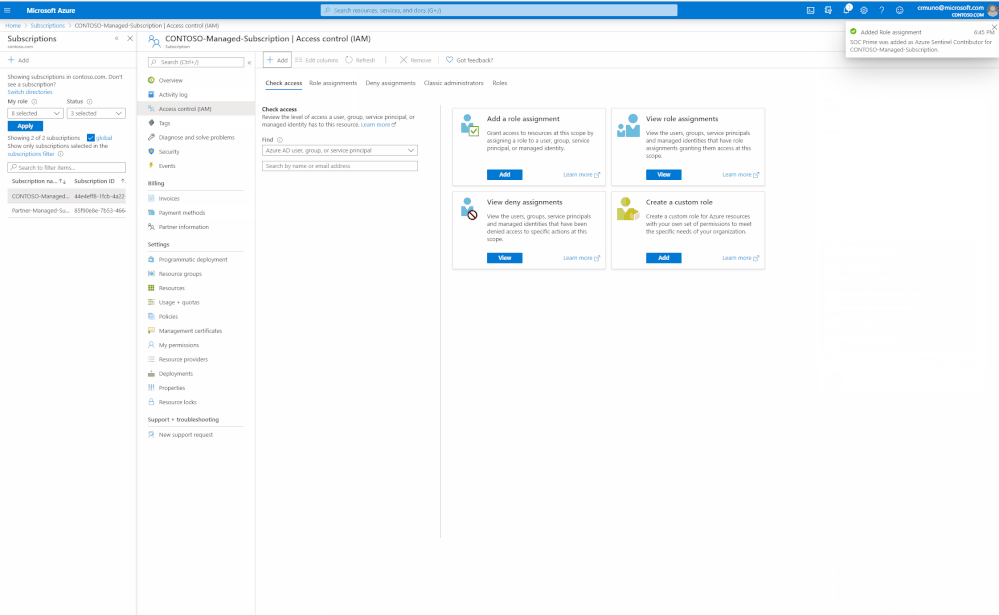
- In the Access Control (IAM) section, select ‘Add’
- Click on ‘Add Role Assignments’
- Select the ‘Azure Sentinel Contributor’ role and start inputting the name of the application in the ‘Select’ field
Single Click Deployment from TDM to Azure Sentinel
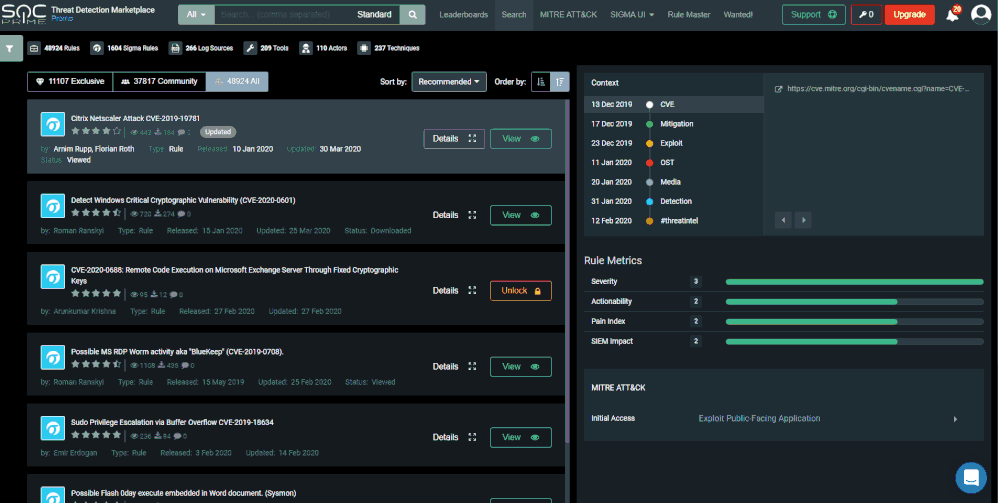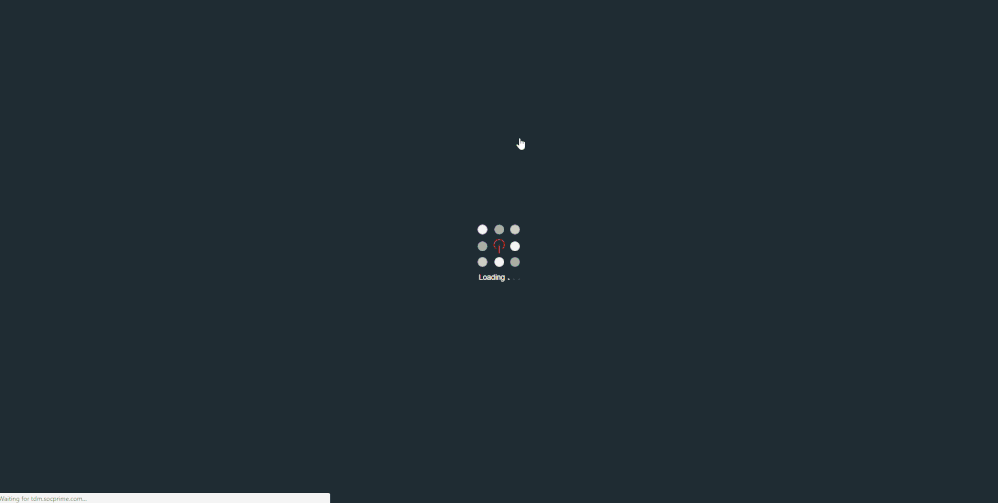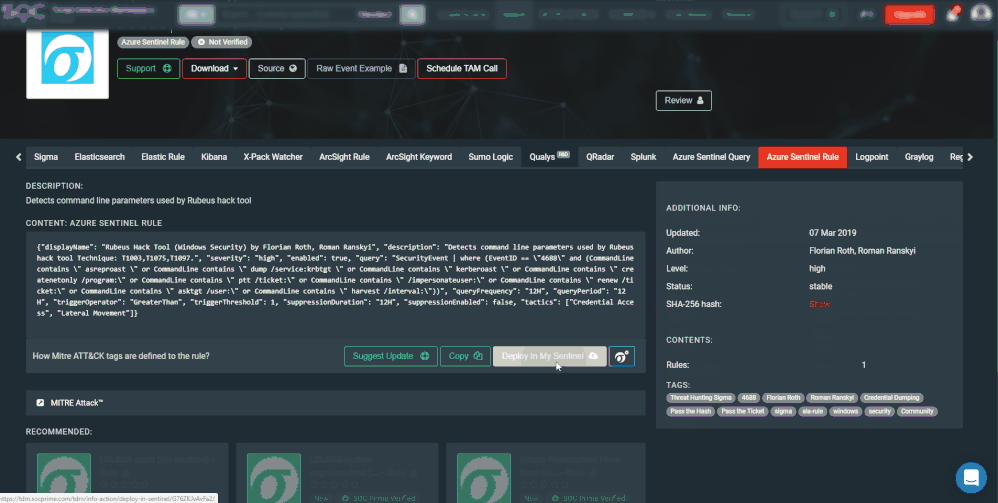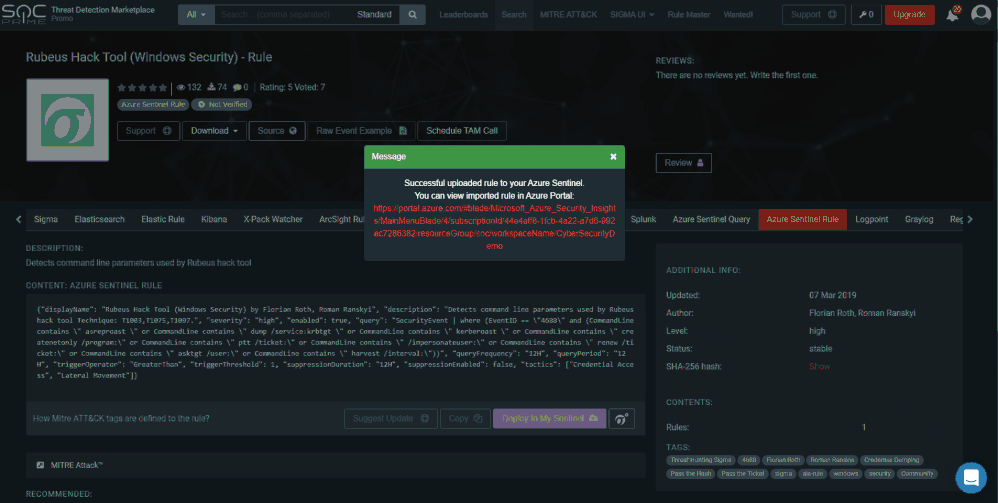
Now that you configured the auto-deployment, filter the rules in TDM for Azure Sentinel rules. You can also search for a specific rule or filter by MITRE technique. When you select a rule, it will navigate you to another pane providing additional details, and for Sentinel rules allow you to "Deploy in my Sentinel".
Make sure to pay attention to the data sources used by the rule. If the data source is Sysmon, refer to the Sysmon section below on instructions on how to enable Sysmon based detections.
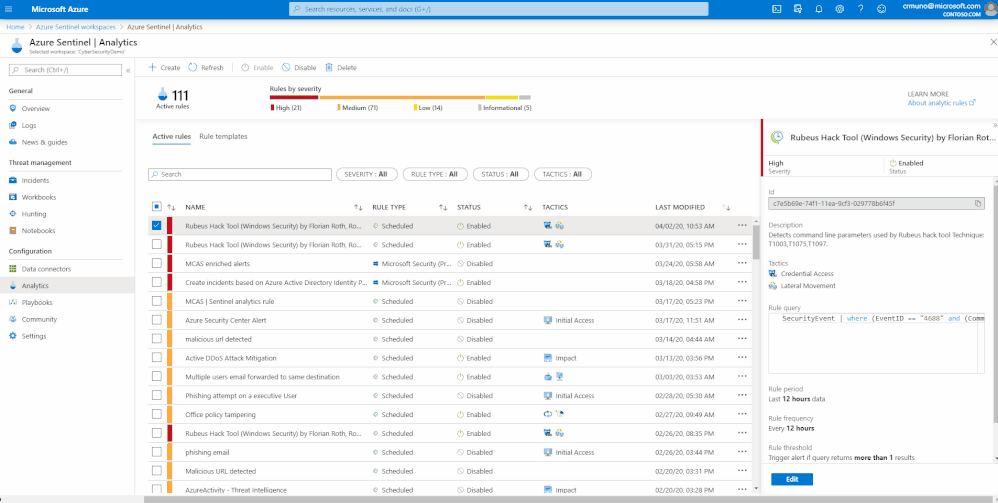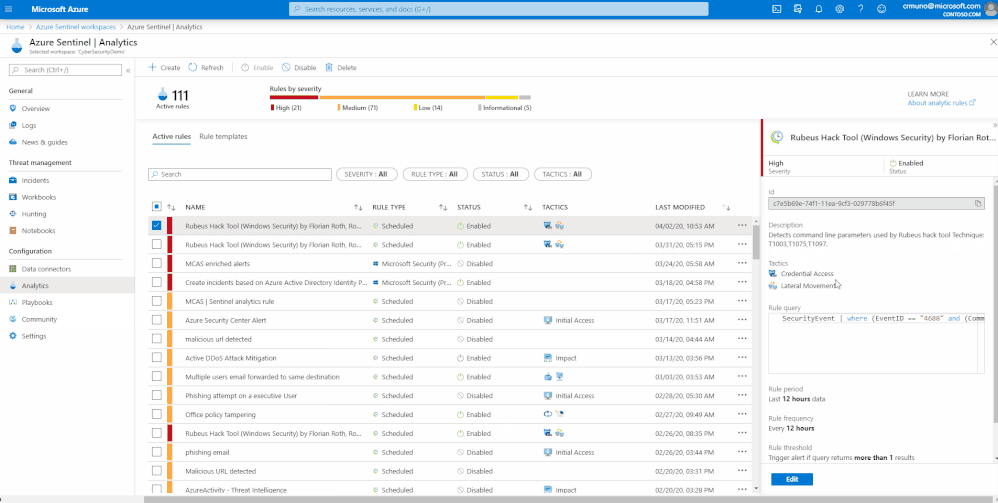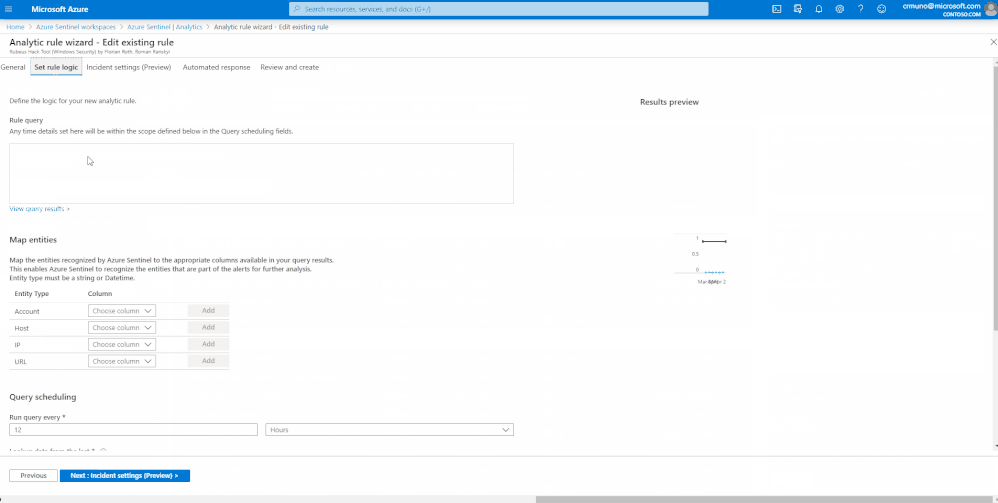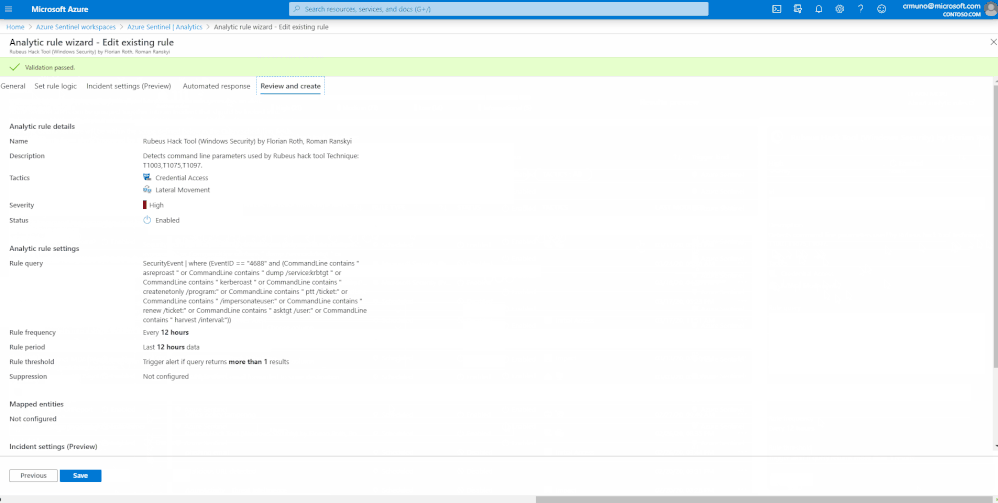
In the example below, I selected a rule that detects command line parameters used by Rubeus hack tool. By clicking on the "Deploy in my Azure Sentinel" button, it will deploy the rule to your Azure Sentinel instance. ![]()
Putting it all together – View & Edit in Azure Sentinel
After you receive the success message from SOC Prime, the rule is deployed in your Azure Sentinel instance. The rule will be available under ‘Active Templates’ tab within the ‘Analytics’ pane of Azure Sentinel.
In Azure Sentinel, you have the ability to view/edit the rule and thoroughly understand the use case and MITRE ATT&CK tactics or technique it correlates to. Moreover, you can utilize the rule wizard to modify additional rule parameters, group alerts into incidents to reduce the alert fatigue and lastly, automate the response to the alert. For more information on creating and automating playbooks, see Respond to threats.
Onboarding Sysmon Events to Azure Sentinel
A copious amount of rules in the SOC Prime Threat Detection marketplace require Sysmon data to be able to detect the use case. Sysmon is a de-facto standard to extend Microsoft Windows audit which allows to detect anomalies, suspicious events on Windows hosts, gather SHA-256 hashes from every running executable, and much more.
Follow the following steps to onboard Sysmon events into Azure Sentinel:
- Install Sysmon on the machines you want to monitor; to do so follow the official documentation
- Install the Log Analytics agent on the machines you want to monitor; this is not needed if you already installed it for another Sentinel data source such as Security Events.
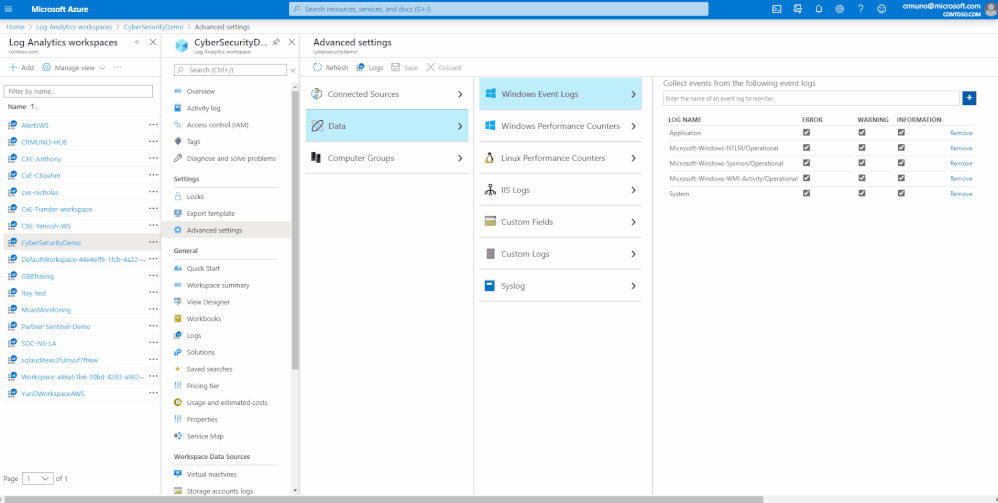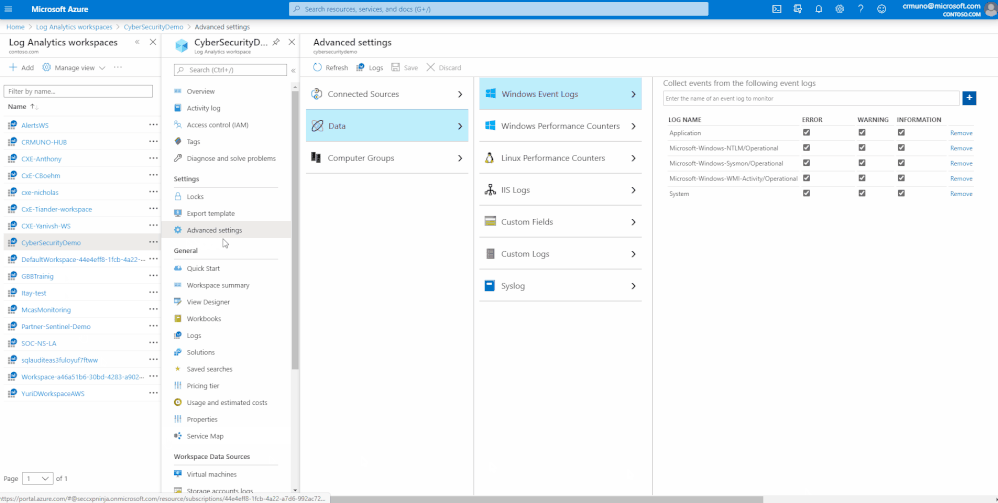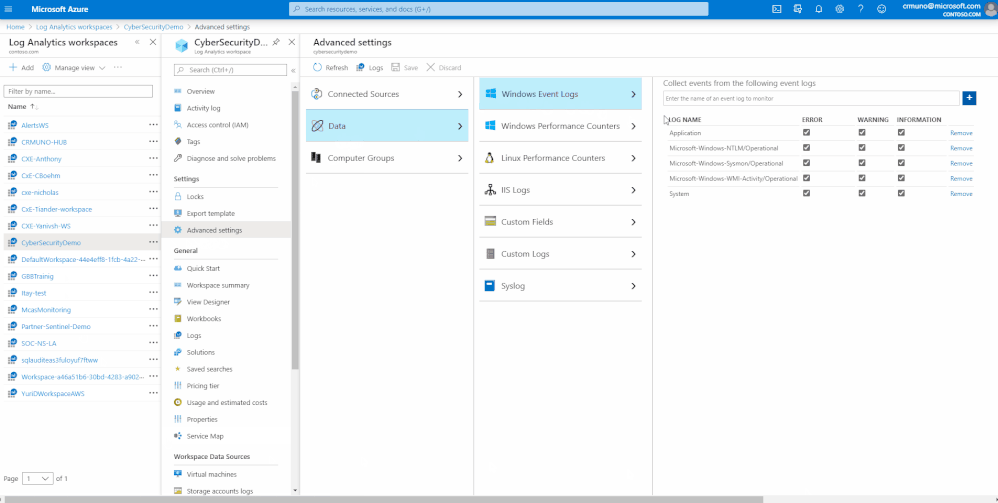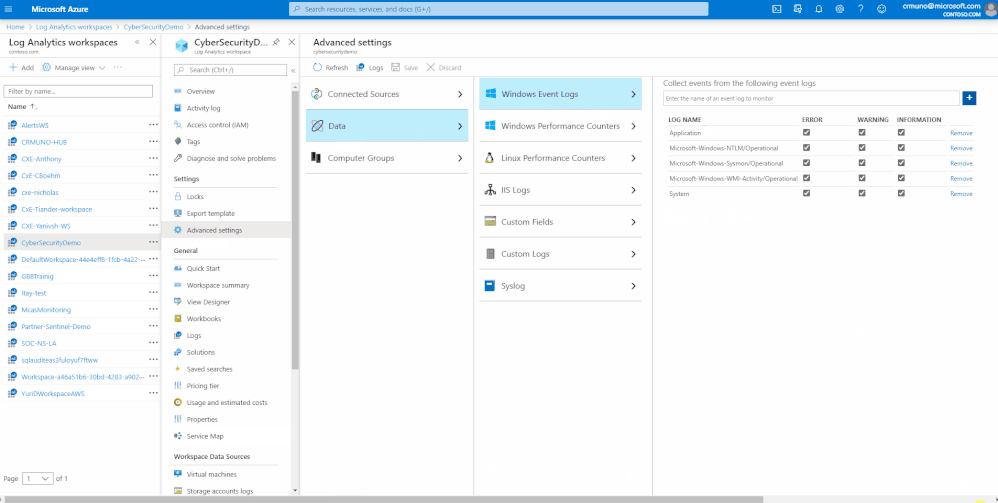
- Now we are ready to activate the windows event logs as data sources. To do so, navigate to ‘Advanced Settings’ pane of your workspace, click on Data and activate the following event logs:
- Microsoft-Windows-Sysmon/Operational
- Microsoft-Windows-WMI-Activity/Operational
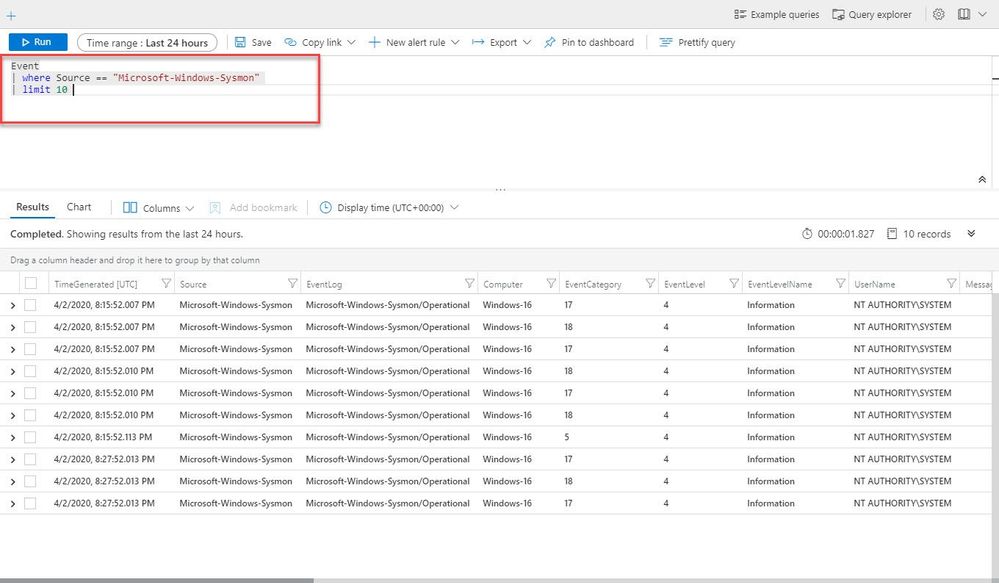
4. By now the data should be flowing into your Azure Sentinel instance. You can check this by navigating to 'Logs' and using the following KQL query:
Event | where Source == "Microsoft-Windows-Sysmon" | limit 20
5. Deploy the Sysmon parser:
- Paste the relevant query for your Sysmon version from GitHub to the logs screen in Azure Sentinel: 9.10, 10.42
- Click on Save button, use "SysmonEvent" as the name and select "Function" in the "Save as" drop down. Any category will work. Note that function usually takes 10-15 minutes to activate.
Summary
Supercharge your cloud SIEM today!