This post has been republished via RSS; it originally appeared at: Device Management in Microsoft articles.
As most of the world is working from home due to the current COVID-19 pandemic, ITPros are busy helping users securely access corporate resources. We have put together this blog to share how we can protect and secure an organization's resources and data while providing a better user experience and increase the productivity using Microsoft Intune (Microsoft Endpoint Manager -Intune).
Microsoft starts with a solid foundation and all users need to use a secure device to access Microsoft resources. Some of the access policy highlights.
- Device management is required for all devices accessing resources. Users with personally owned devices will have the choice to opt-in to device management or to not use their device for work.
- Hardened security configurations will be implemented across all device types to take advantage of the latest security technologies and remove legacy device threats.
- Corporate applications will be blocked from devices that are not compliant. Devices that are not managed or not compliant with security policies will be blocked by default.
As most of you aware, by using Intune, organizations can deploy security policies to secure devices. By doing this, ITPros can make sure that only authorized users and devices get access to proprietary information. In this post, I am going to share some details about how we are managing and securing our devices utilizing Conditional Access policies, Mobile Threat Defense agent (MTD) and Advanced Threat Protection (ATP).
How are Conditional Access policies applied?
Intune and Azure Active Directory work together to make sure only managed and compliant devices can get access to corporate resources like email, VPN, etc. As part of the conditional access policies enforcement, we created multiple compliance policies in Intune to evaluate the compliance status of the devices. These compliance policies check for configurations such as, device encryption, Password/PIN configuration, MTD and ATP status. Compliance status from Intune is update in AAD to enforce the Conditional Access policies created in AAD. Currently we have multiple Conditional Access policies enforced and all devices need to meet the criteria to gain access to corporate resources. In our environment we chose a two phased approach to enforce Conditional Access policies.
Phase 1: What would happen if we enabled Conditional Access policies for all users today?
We have applied conditional access policies in ‘read only’ to all users across Microsoft. This helped us to avoid protentional impact by identifying the impacted devices.
Phase 2: Enforcement of policies
Enforce the Conditional Access policies after working with impacted users from phase 1 so while accessing application evaluate the Conditional Access policies status.
As part of conditional Access enforcement All devices must be managed to access O365 resources.
- Office 365 components
- portal.office.com
- Portal.azure.com
- VPN
- Any apps relying on the above services are also impacted
The following policy is currently rolling out to all corporate users
- Device must be managed.
- Latest OS requirements.
- Device must be healthy, for example the device must be encrypted and malware free.
- Must be strongly authenticated– set up to use Multifactor Authentication) MFA) and a complex password.
Best Practices
- Before enforcing the conditional access, policies make sure to analyze the impact by applying read-only mode.
- Work with potentially blocked users (identify users from read-only mode deployment) to remediate the device to meet the requirements.
- Phaseout the policy enforcement.
- Pilot phase with small number of users to ensure that things are working as excepted.
- Key people who are involved and support.
- Volunteers from different parts of the organization need to assist in validating the user experience.
- Ensure that each phase has set criteria that must be met before you increase the user targeting and lessons learned from previous phases are documented in a “Known Issues” list.
- Obtain executive level support from the leadership team in each organization.
- Executive level communications must be sent to users explaining the “Why” prior to enforcement of users in each organization.
- Agree on enforcement strategy and rollout plan for each organization with core organization stakeholders.
- Multiple IT End User Communication should be sent to users, e.g. 2 weeks, 1 week and 1 day prior to enforcement.
- Monitor all support and communication channels for feedback from users.
- Include key stakeholders during the POC validation.
- Avoid re-enrolling the same device unless you have thoroughly removed the previous enrollment settings.
Troubleshooting Tips
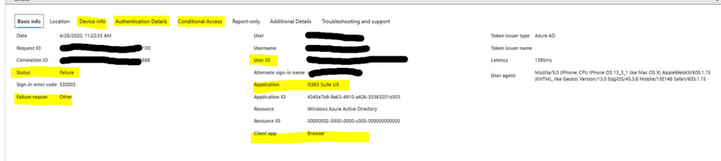
- Use AAD Sign-in logs to find all the information about user sign-in and the Failure reason.
- Device info and conditional access tab will have critical information
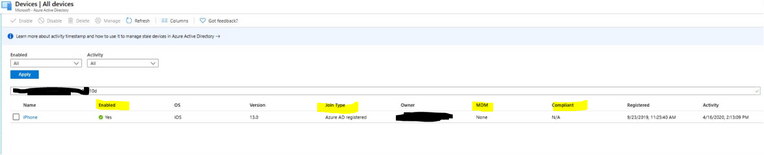
- Validate the device identity between AAD, Intune, and AAD sign-ins e.g. device ID and user details of the device should match across all three environments.
- Both, the user and the device, must be compliant with the assigned Intune compliance policies.
- When a device is first enrolled, it might take some time for compliance information to be registered for a device between Intune and AAD. Wait a few minutes and try again.
- Some Android devices will show as noncompliant for device encryption even though the device is encrypted, this is a known issue. Users need to set the custom PIN instead of using default PIN to ensure that the device is compliant.
- You can use the Intune Troubleshooting blade (On the Intune pane, choose Troubleshoot.) to identify Intune enrollment and device status details.
- AAD devices blade helps to identify AAD registration and device status details.
- You can also utilize Graph API to build custom PowerShell scripts to check the device and policies status.
Conclusion
We hope this post has given you some ideas on how to implement secure access by helping users to improve productivity.