This blog post covers a new feature of the Azure Sentinel entity pages: four new UEBA-related insights to the insights panel.
When you encounter any entity (currently limited to users and hosts) in a search, an alert, or an investigation, you can select the entity and be taken to an entity page, a datasheet full of useful information about that entity. The types of information you will find on this page include basic facts about the entity, a timeline of notable events related to this entity, and insights into the entity’s behavior.
Entity pages consist of three parts:
- Entity info – located in the left-side panel, contains the entity’s identifying information, collected from data sources like Azure Active Directory, Azure Monitor, Azure Security Center, and Microsoft Defender.
- Activity timeline – The center panel shows a graphical and textual timeline of notable events related to the entity, such as alerts, bookmarks, and activities.
- Insights – The right-side panel presents behavioral insights on the entity. These insights help to identify anomalies and security threats quickly.
We’ve added four UEBA-related insights to the insights panel that this post will describe.
* To benefit from these insights, UEBA must be enabled and a timeframe of at least 4 days.
UEBA Insights
This insights section summarizes anomalous user activities – across geographical locations, devices, and environments; across time and frequency horizons (compared to user’s own history); compared to peers’ behavior, and compared to organization’s behavior.
Clicking on “See all anomalies” will present you with the specific anomalies associated with the user and the evidence.

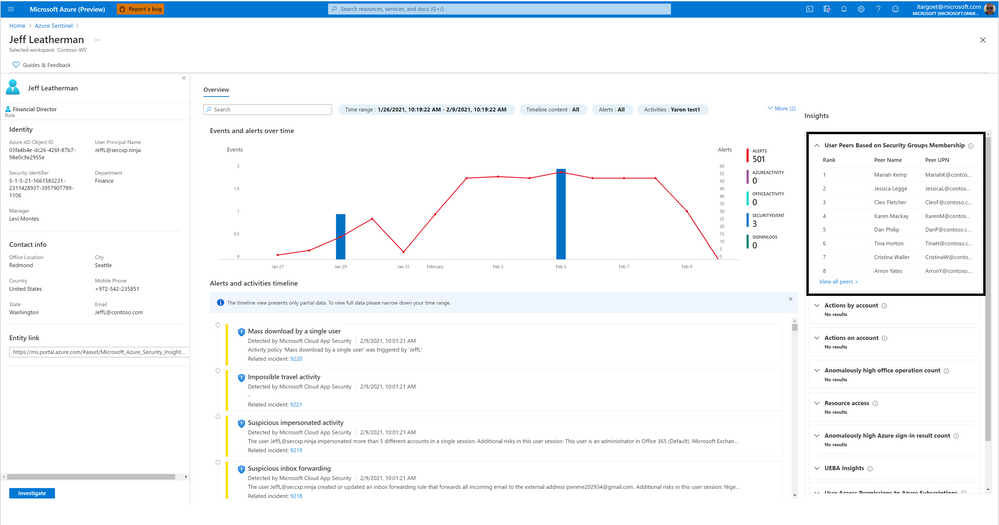
User Peers Based on Security Group Membership
This insight presents the user’s peers based on Azure AD Security Groups membership. This provides the SecOps analysts with visibility to other users who share similar permissions as the user.
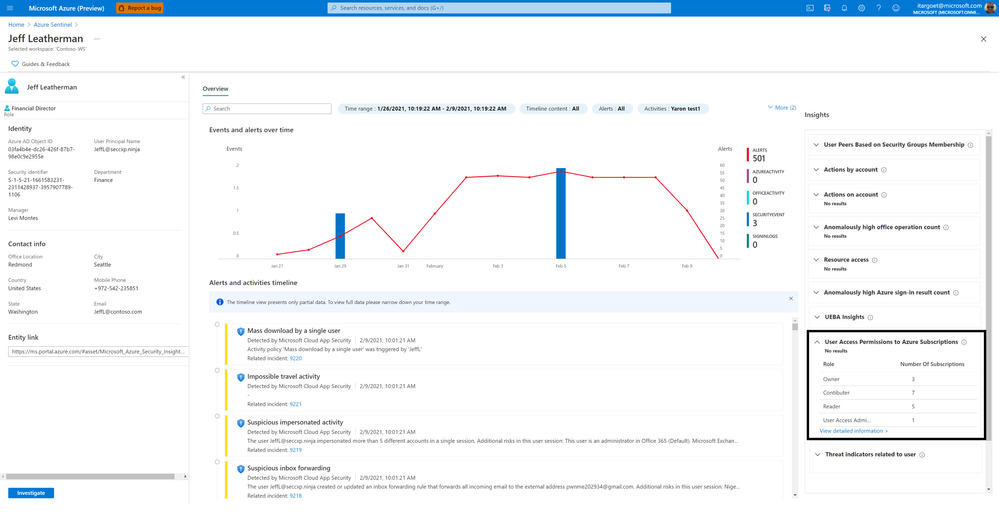
User Access Permissions to Azure Subscription
This insight shows a user’s access permissions to the Azure subscriptions that it can access directly or transitively (via Azure AD groups or service principals). Clicking on “View detailed information” will present the Azure subscriptions’ names and the access method (directly or via which group/service principal).
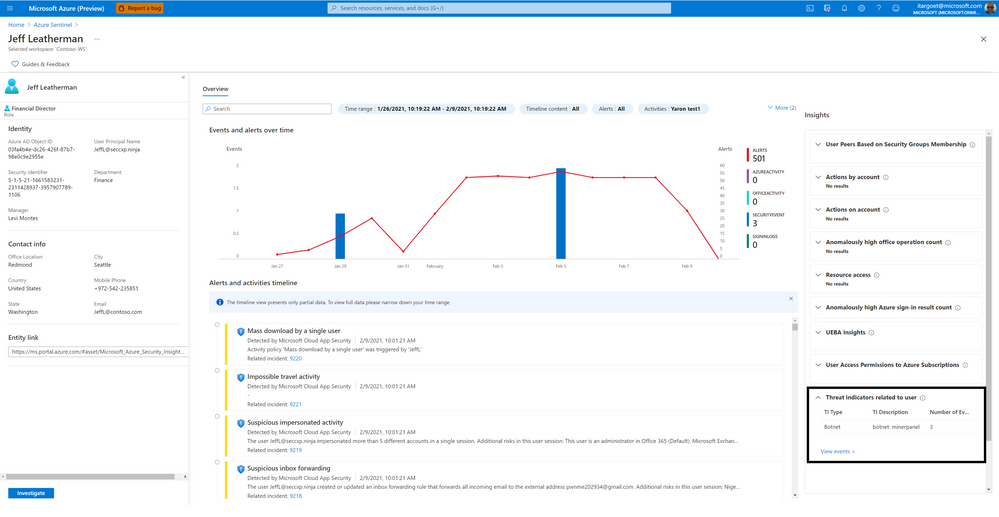
Threat Indicators Related to The User
This insight shows the collection of known threats by threat type and family and enriched by Microsoft’s threat intelligence service, relating to IP addresses represented in the user’s activities.
Going Forward
Try out the new insights provided by Sentinel UEBA and let us know your feedback using any of the channels listed in the Resources. We’re working on surfacing more interesting insights that will help you investigate entities faster. ![]()
Many thanks to Payal Rani & Rajvardhan Oak for contributing to the insights work
