Introducing the IP entity page
Now in preview, the IP entity page is the latest addition to Azure Sentinel’s User and Entity Behavior Analytics capabilities. Like the host and account pages, the IP page helps analysts quickly triage and investigate security incidents.
The IP page aggregates information from multiple Microsoft and 3rd party data sources. This page provides contextual information and insights like geolocation information, threat indicator data, network session data and IP-to-host mappings.
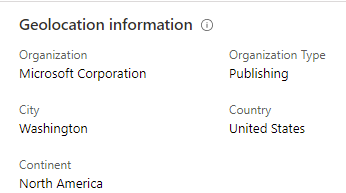
Geolocation information
Geolocation is often used to assess the security relevance of an IP address. We provide geolocation enrichment data from the Microsoft Threat Intelligence service. This service combines data from Microsoft solutions with 3rd party vendors and partners. It will soon be available via REST API for security investigation scenarios to Azure Sentinel customers.
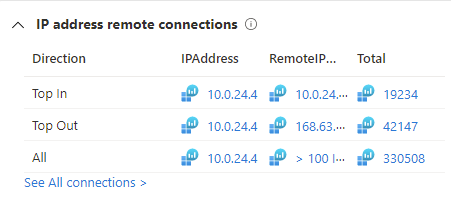
Remote connections and threat indicator data
Understanding which endpoints an IP address has been connecting to is a key task in investigating IP related security incidents. The IP page summarizes this information from Azure Monitor, Microsoft Defender for Endpoints (MDE), CommonSecurityLog and other data sources.
The IP page also makes discovering connections to malicious endpoints easy. It compares remote session endpoints to IP Indicators of Compromises (IoCs) provided by Microsoft and by any threat intelligence source for which there is an enabled data connector.
By clicking on “See all connections” you can drill into the details in Log Analytics, so that you can review the data yourself and bookmark important connections.
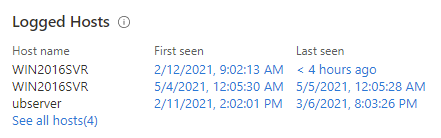
IP-to-host mappings
Like the host and account entities, you can search for individual IP addresses using the Entity Analytics search experience. We take this a step further by enabling you to search for hosts using IP-to-host mappings.
We also provide a summary of all IP-to-host mappings on each IP entity page. The first seen / last seen information enables you to infer when the IP address was assigned to which machine.
IP-to-host mappings are currently generated from Azure Monitor heartbeat data. Let us know which data sources you most prefer, so that we know what to onboard next.
IP address log activity
The IP entity page also shows when an IP address has first been recorded in an alert or in a set of specific common data sources. This “first seen” information is reported even if the first event aged out due to the Log Analytics retention period. This is quite helpful when trying to identify when a malicious external IP address was first seen in your environment.
Further Reading
- User and Entity Behavior Analytics: https://docs.microsoft.com/en-in/azure/sentinel/identify-threats-with-entity-behavior-analytics