This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
Introduction
This article is a continuation of Azure Defender PoC Series which provides you guidelines on how to perform a proof of concept for a specific Azure Defender plan. For a more holistic approach where you need to validate Azure Security Center and Azure Defender, please read How to Effectively Perform an Azure Security Center PoC article.
There can be many security vulnerabilities in databases that are sometimes taken advantage of by malicious actors. According to the Github 2020 report, a vulnerability typically goes undetected for 218 weeks (just over four years) before being disclosed and fixed. Injection attacks, such as those on SQL and NoSQL, are among the most popular types of cyberattacks for web applications (as per OWASP Top 10).
SQL Injection attacks, brute-force attacks, SQL shell OS attacks leading to crypto-mining and ransomware, , can be detected and remediated by the Azure Defender for SQL plan.
Azure Defender for SQL has two main capabilities that together will protect your SQL environments from cyberattacks. These capabilities are:
- Vulnerability Assessment, which is a service that helps you identify and remediate vulnerabilities in your database environments to improve your security posture
- Advanced Threat Protection, which detects suspicious activities related to your databases and alerts you with details and recommended actions.
Planning
So, what actually gets protected through Azure Defender for SQL?
There are two Azure Defender plans that are comprised as part of Azure Defender for SQL:
- Azure Defender for Azure SQL database servers protects:
- Azure Defender for SQL servers on machines extends the protections for your to fully support hybrid environments and protects SQL servers hosted in Azure, other cloud environments, and even on-premises machines. It does this by protecting:
There is also a third plan called Azure Defender for open-source relational databases that brings threat protection for:
Preparation
You will need to first enable Azure Defender for SQL, and for this you need to have the role of Security Admin. For more information about roles and privileges, visit this article.
You can enable the three plans for Azure Defender for SQL (for Azure SQL database servers, SQL servers on machines, and open-source relational databases) by following the instructions here.
If you are conducting this PoC in partnership with the SOC Team, make sure they are familiar with the alerts that may appear once you enable this plan. Review all alerts available at our Alerts Reference Guide.
From the readiness perspective, make sure to review the following resources to better understand Azure Defender for SQL:
- Azure Defender for SQL Documentation
- Azure Defender for SQL and the Vulnerability Assessment | Azure Security Center in the Field #1
- Azure Security Center webinar: Azure Defender for SQL Anywhere
Special Note for Defender for SQL servers on machines
Azure Defender for SQL servers on machines requires a Log Analytics agent installed and it should report to a workspace with enabled Azure Defender for SQL.
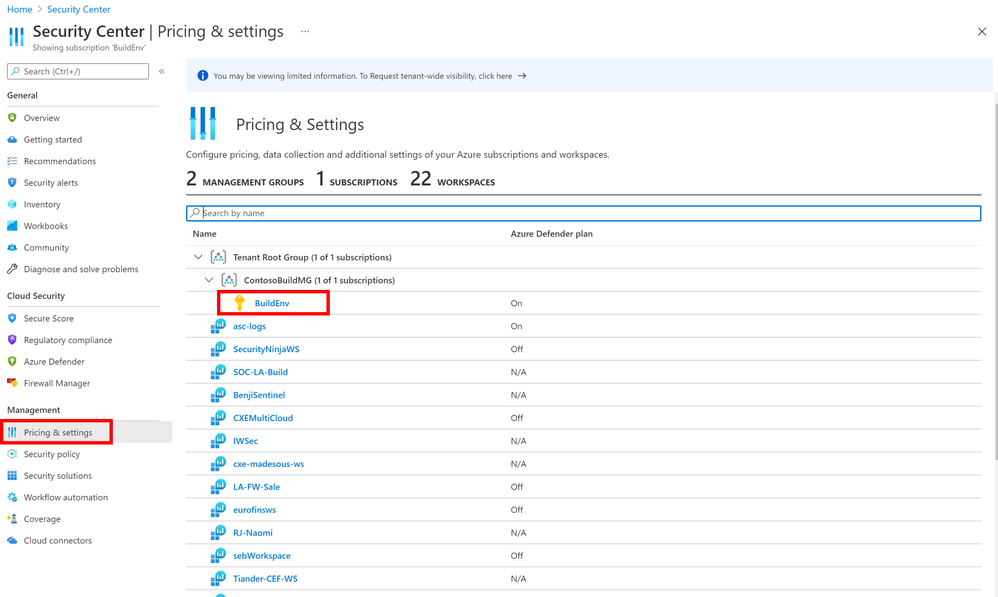
Azure Security Center default workspaces are controlled through the subscription settings in Pricing & Settings.
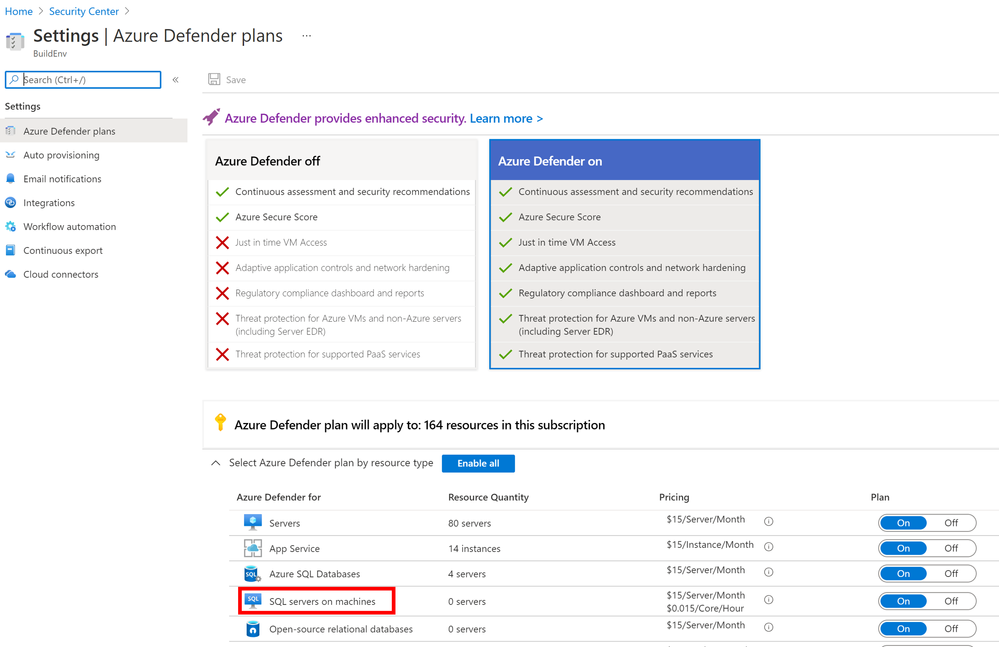
Then ensure to turn SQL server on machines to be On.
However, for customer-created workspaces, you need to enable Defender for SQL servers on machines on the particular workspace. Instead of going into the subscription, select the workspace that is associated with Azure Defender for SQL servers on machines.
Then ensure that SQL servers on machines is turned On from here.
Implementation and Validation
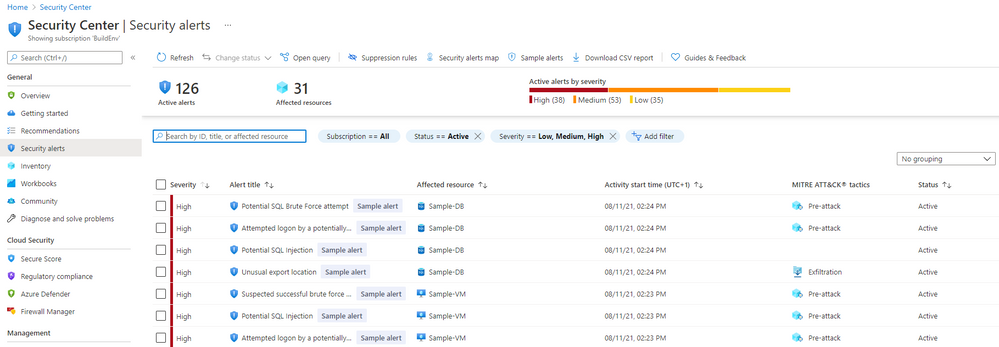
You can use the sample alert feature to validate . To create these sample alerts, you will need to have the role Security Admin or Subscription Contributor.
To create sample alerts for Defender for SQL, go to Azure Security Center in the Security alerts section, click Sample alerts.
Select your subscription, choose Azure SQL Database and SQL Server on machines on the Azure Defender plans, and click Create sample alerts.
Prevention
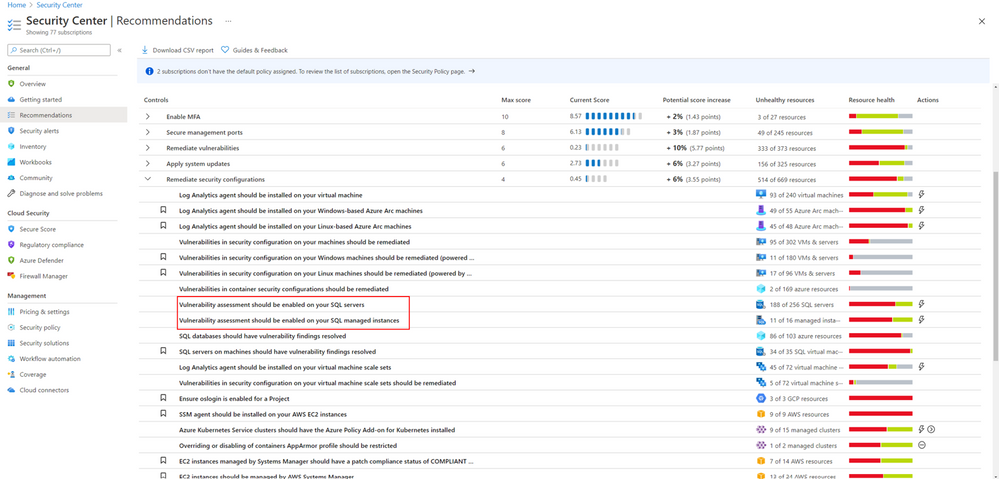
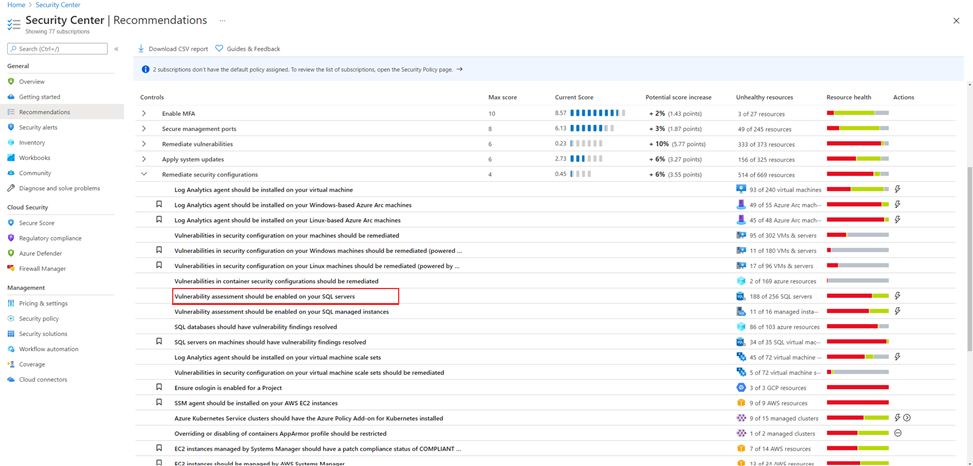
Azure Defender for SQL allows you to remediate SQL vulnerabilities and prevent SQL incidents and alerts using SQL vulnerability assessment. To configure it on your Azure SQL databases and Azure SQL Managed Instance, go to the Recommendations page in Azure Security Center, and select one of the following recommendations under the control Remediate security configurations:
- For Azure SQL databases, select the recommendation Vulnerability assessment should be enabled on your SQL servers.
- For Azure SQL Manage Instances, select the recommendation Vulnerability assessment should be enabled on your SQL managed instances.
When Azure Defender for SQL is enabled on your SQL Server on machines, SQL vulnerability assessment does not require initial configuration, as it’s installed automatically.
In this article, we will demo SQL vulnerability assessment for Azure SQL database. Select the recommendation Vulnerability assessment should be enabled on your SQL servers.
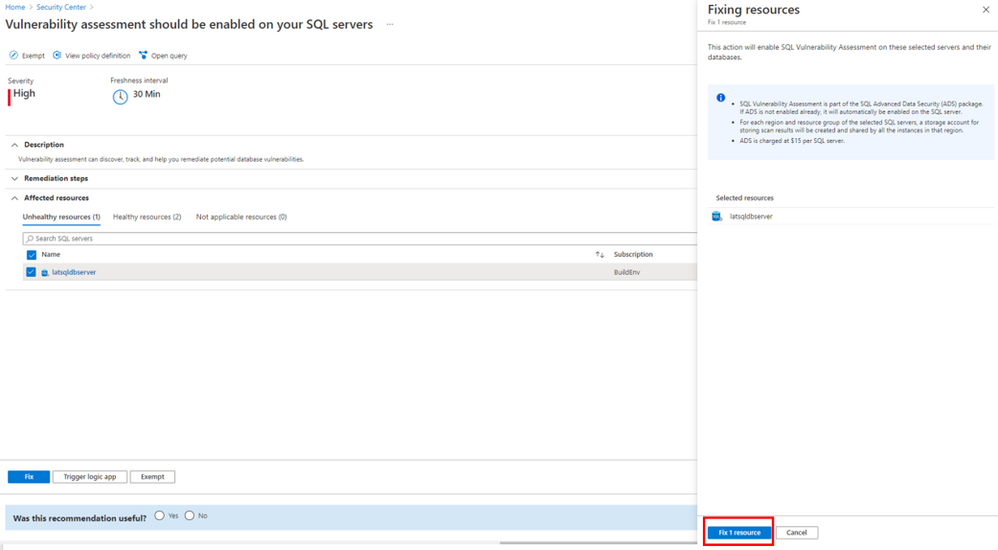
From here, select the unhealthy resource that you’d like to configure vulnerability assessment on, and click Fix.
In the pane that appears, click Fix 1 resource.
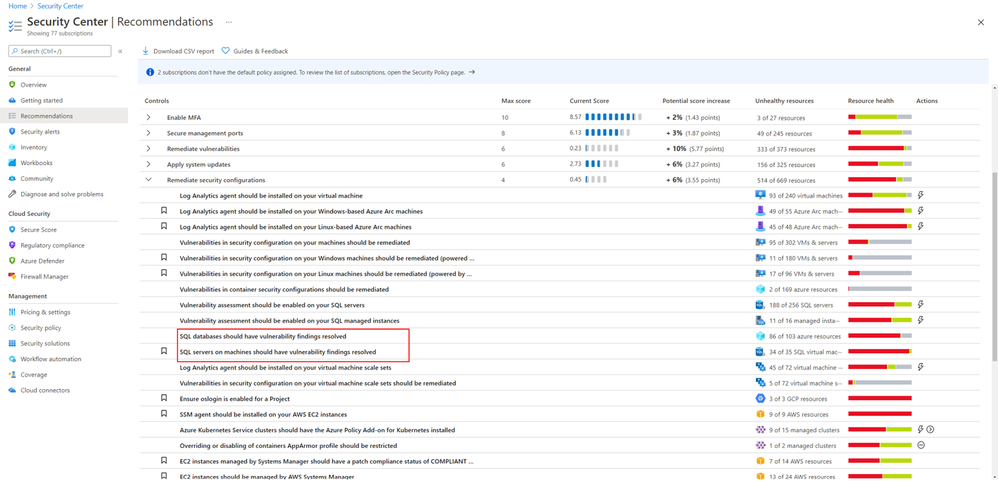
To remediate vulnerability findings from your SQL databases and SQL Server on machines, go to the Recommendations page in Azure Security Center. Under the control Remediate security configurations, select one of the following recommendations:
- For Azure SQL databases and Azure SQL Manage Instances, select the recommendation SQL databases should have vulnerability findings resolved.
- For SQL Server on machine, select the recommendation SQL servers on machines should have vulnerability findings resolved.
In this article, we will demo SQL databases should have vulnerability findings resolved.
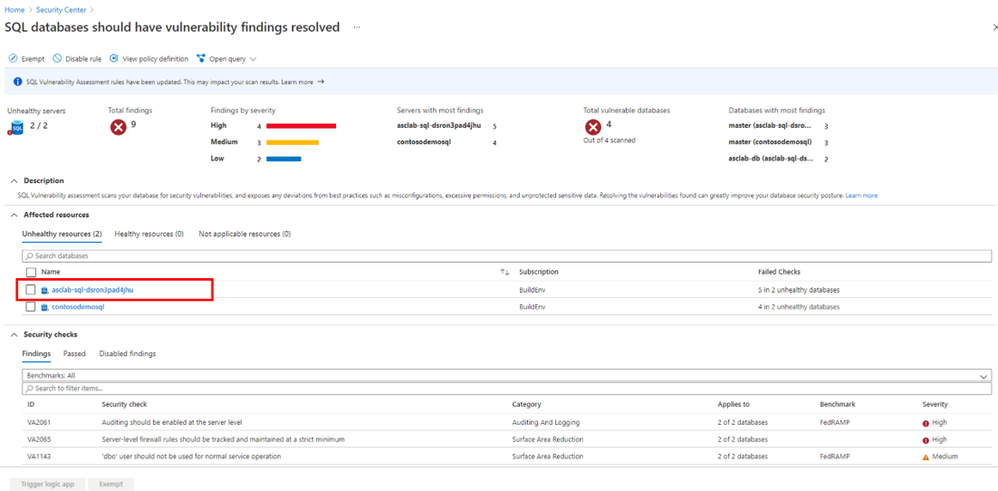
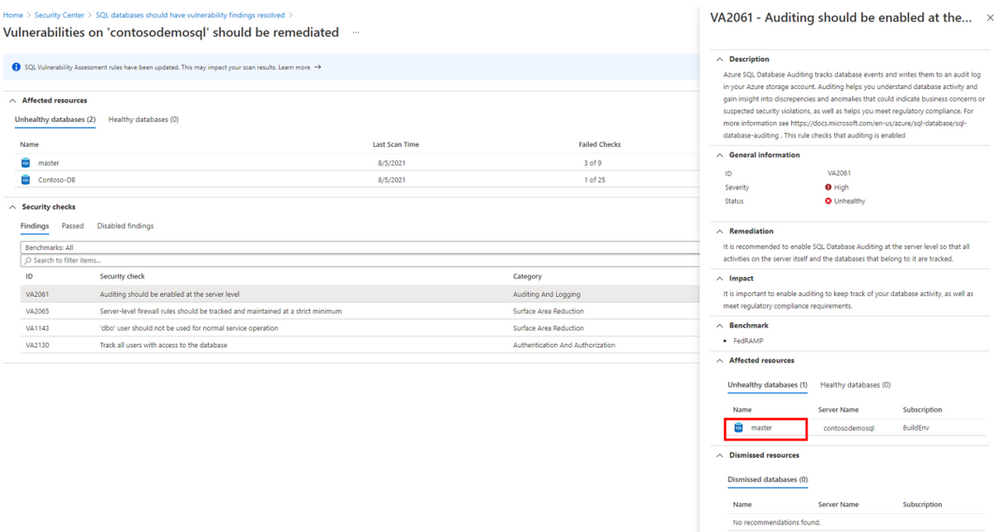
From here, select any of the unhealthy resources.
Then select the finding you wish to remediate. In this example, we’ll be selecting Auditing should be enabled at the server level.
Then select the database.
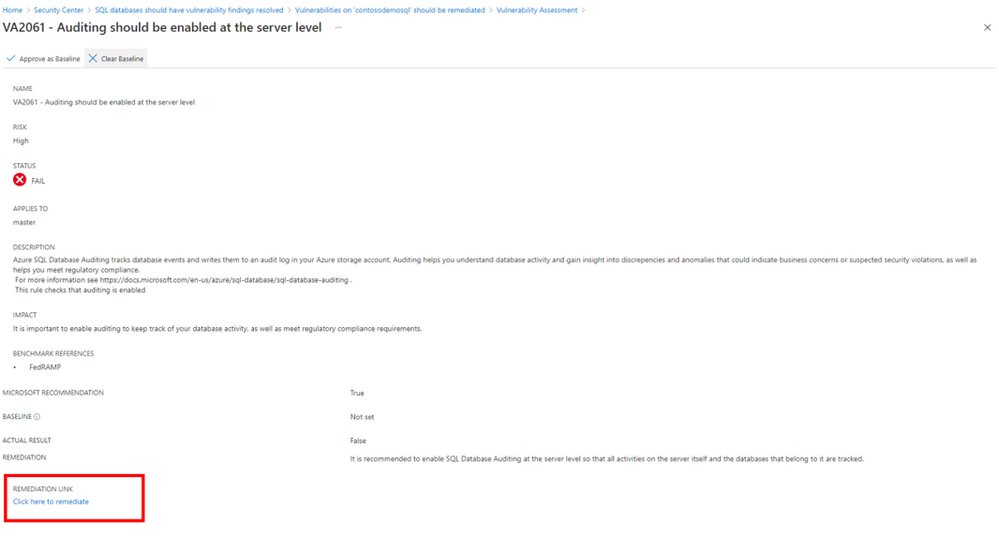
Once again, click the finding you wish to remediate, which in our case is Auditing should be enabled at the server level.
Select Click here to remediate.
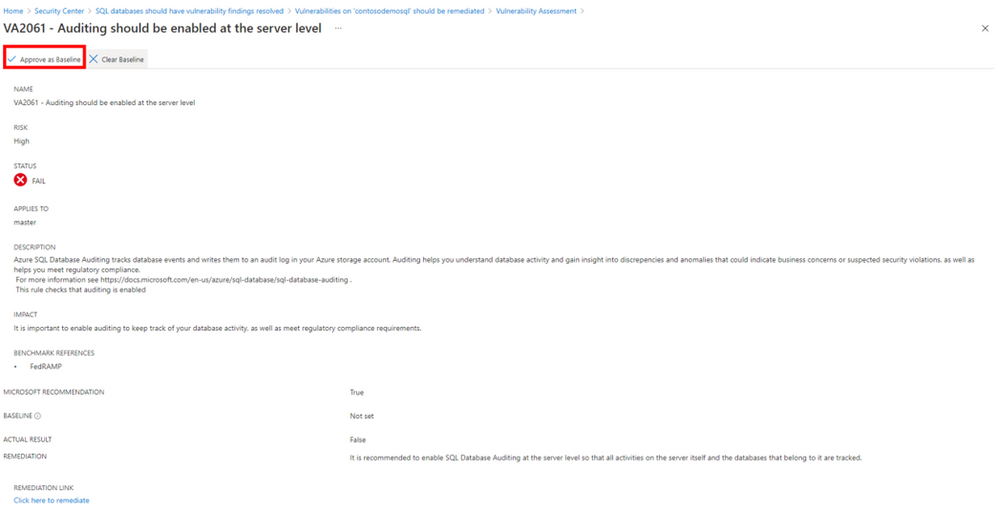
Alternatively, you may decide that this finding does not pose a security risk for your environment. In this case, you should create an acceptable baseline, which is essentially a customisation that tells the Vulnerability Assessment what is expected in your environment.
To do this, select Approve as Baseline, and follow the subsequent instructions.
Vulnerability Assessment recurring scans in your environment, and in upcoming scans after this, any results that match the baseline you established are considered as passes. Only reports on deviations from this baseline will appear as findings in the Vulnerability Assessment dashboard. This allows you to focus your attention only on the relevant issues.
Continue remediating and/or setting baselines across all the findings and databases to improve your SQL security posture.
Automations
Instead of following the manual process above to remediate recommendations on SQL databases, you can also use the automated ways to remediate recommendations related to SQL like, Vulnerability assessment should be enabled on your SQL servers, SQL managed instances, Enable transparent data encryption on SQL databases, Advanced Data Security for SQL Servers and many more like these in our Azure Security Center Github repository which gives you access to numerous such sample security playbooks that will help you automate in remediating a recommendation.
You can also utilize workflow automation feature in Azure Security Center which can trigger Logic Apps on Security alerts, recommendations, and changes to regulatory compliance. For example, when Azure Security Center detects a brute force attack, you may want this to be automatically taken care off, you can use this playbook as a starting point.
To understand how to remediate security alerts using Azure Defender, make sure you check out this chapter from SC-200 certification exam learning guide. You can also create an automatic response to a specific security alert using an ARM template, read more about it in our documentation.
Latest Updates
Azure Defender for SQL is now available on the SQL Virtual Machine blade. - Microsoft Tech Community
Conclusion
By the end of this PoC you should be able to determine the value proposition of Azure Defender for SQL and the importance to have this level of threat detection to your workloads.
Stay tuned for more Azure Defender PoC Series!
Reviewers
Special Thanks to Yuri Diogenes, Safeena Begum, David Trigano and Michael Makhlevich for reviewing this article.