This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
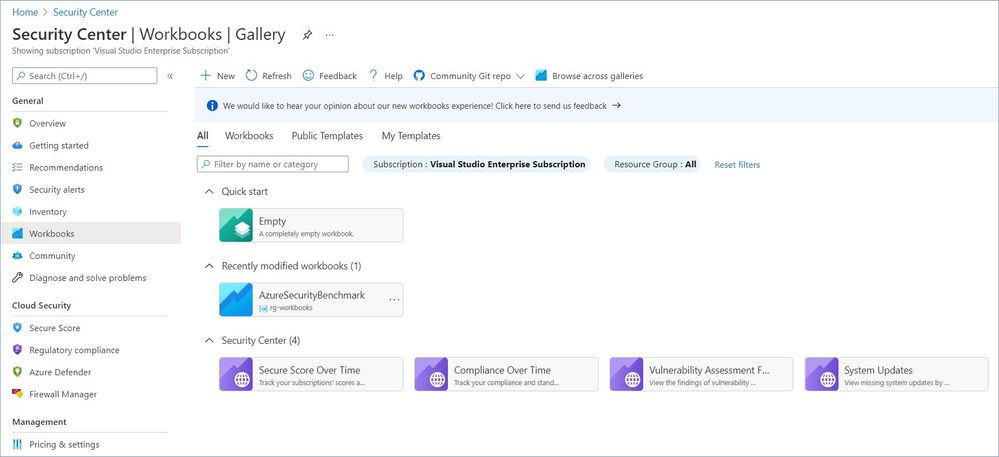
Azure Workbooks are a great way of analyzing and visualizing various data in Azure. Azure Security Center (ASC) provides several built-in workbooks to track your company’s security posture, e.g. Secure Score or regulatory compliance. You can also create your own custom workbook that fits your specific needs or deploy one created by the Security Center community from our GitHub repository. You can find more information about how to set up and use those workbooks in our documentation.
As a security professional working with ASC, you likely already have access to all its features and capabilities. Once in a while, especially when it comes to reporting, you may need to share this information with someone, like your management, who does not know how to use the ASC dashboard or does not have permissions to access it. Today we are going to discuss exactly how to handle this situation. As of this writing (September 2021) ASC provides four out-of-box workbooks that use different data sources for reporting:
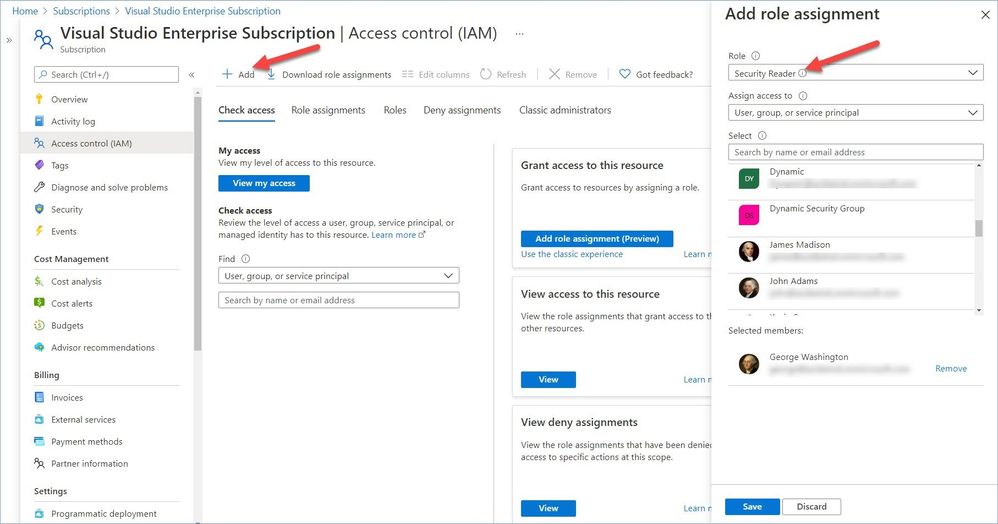
First thing you need to do is to give your target audience proper permissions to access the data used by the workbooks.
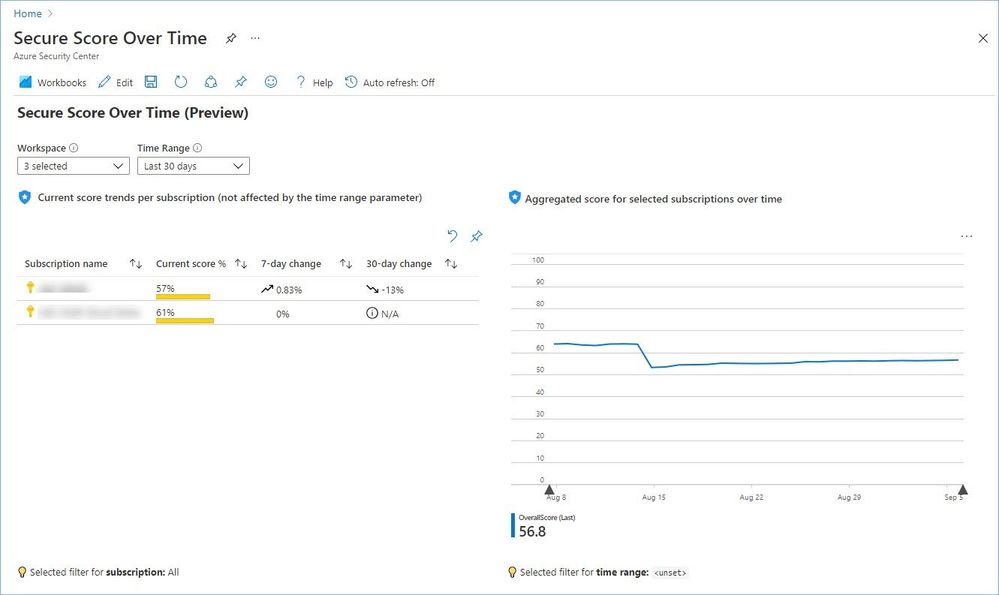
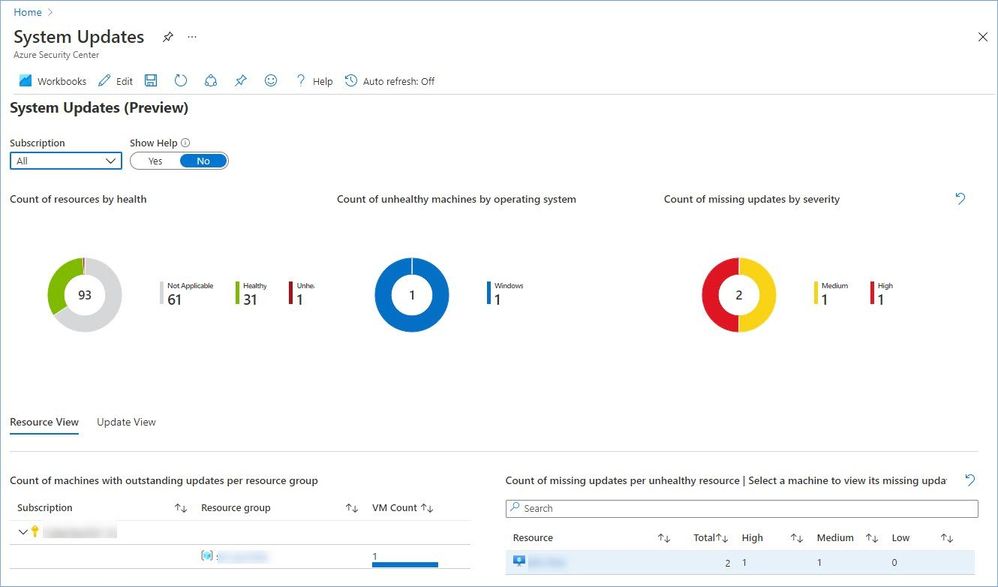
The “Secure Score Over Time” and “Compliance Over Time” workbooks rely on data previously aggregated in a Log Analytic workspace using the continuous export feature, while the “System Updates” and “Vulnerability Assessment findings” workbooks query data directly from Azure Resource Graph (ARG).
Let’s start with the first two. Keeping the principal of least privilege in mind, you need to assign the “Log Analytics Reader” role in this Log Analytics workspace to an Azure Active Directory group (recommended way) or individuals we wanted to share our workbook with.
Note: If you have multiple subscriptions exporting data to different workspaces and you want to give your recipients access to all this data, you will need to repeat this process for all those workspaces.
For the “System Updates” and “Vulnerability Assessment findings” workbooks, you need to grant the recipients permissions to query Azure Resource Graph. This can be done at the subscription or management group level (if you want similar experience across multiple subscriptions). The Security Reader role grants the holder the ability to read data used by these two workbooks.
Note: The Security Reader role assigned at the subscription level grants read access to all Log Analytics workspaces in this subscription. If you want to delegate access to all workbooks in ASC, assigning someone this role will be just enough.
Now we are ready to let our target audience know how to access the reports/workbooks.
Let’s use the “Secure Score over time” workbook as an example, but the sharing process is the same for all of them. All you need to do is to click the "Copy link" button and either “Share link via email” to let recipients know that they now have access to this report or copy/paste the link and share it using other ways, it’s up to you.
Once they get authenticated by Azure AD, they should be able to access the workbooks. Notice that the workbooks open as a separate blade not as part of the ASC dashboard.
Reference:
Create rich, interactive reports of Security Center data
Continuously export Security Center data
P.S. Subscribe to our Azure Security Center and Azure Defender Newsletter to keep up to date on helpful tips and new releases and join our Tech Community where you can be one of the first to hear the latest Azure Security Center news, announcements and get your questions answered by Azure Security experts.
Many thanks to my friends and colleagues