This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Tech Community.
By Laura Arrizza – Program Manager II | Microsoft Endpoint Manager – Intune
We are pleased to announce a new experience to configure local user group membership settings for Windows devices. This comes with a built-in template in the Endpoint security node where you can add, remove, or replace users and user groups to the built-in local groups on the targeted device. This allows IT admins to granularly manage the membership of built-in groups on the Windows platform to ensure users have the correct privileges. For example, the Administrators local group has broad rights, so it is important to lock down the groups to a set of exclusively defined ones via the policy.
The new settings are derived from the Policy configuration service provider (CSP) LocalUsersAndGroups and come as a built-in template in the Account protection section of Endpoint security. Previously, these settings were only able to be configured through PowerShell script, custom OMA-URI policies, or GPO.
Let’s take a tour of the new settings…
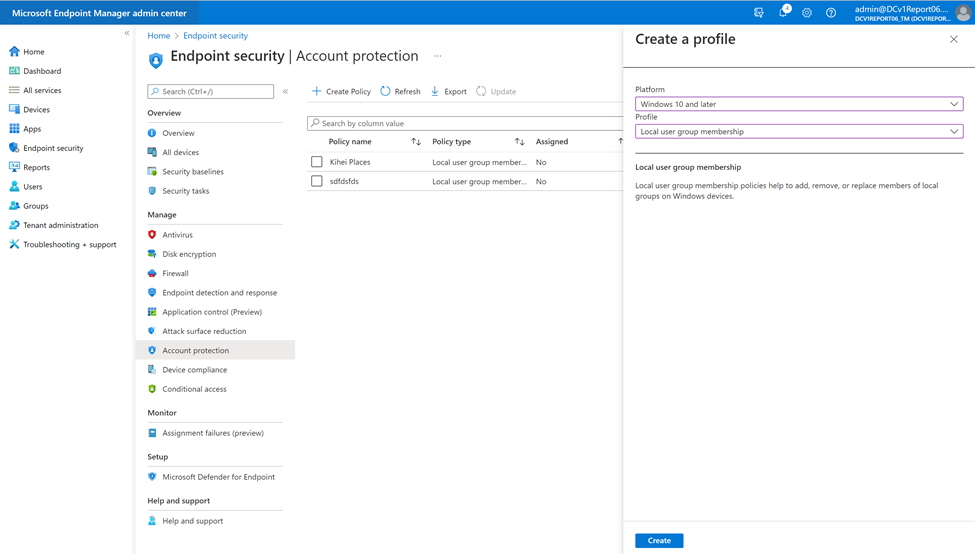
To access these new settings, sign in to the Microsoft Endpoint Manager admin center and select Endpoint security > Account protection. Select Create Policy and choose Windows 10 and later as the platform and Local user group membership as the template.
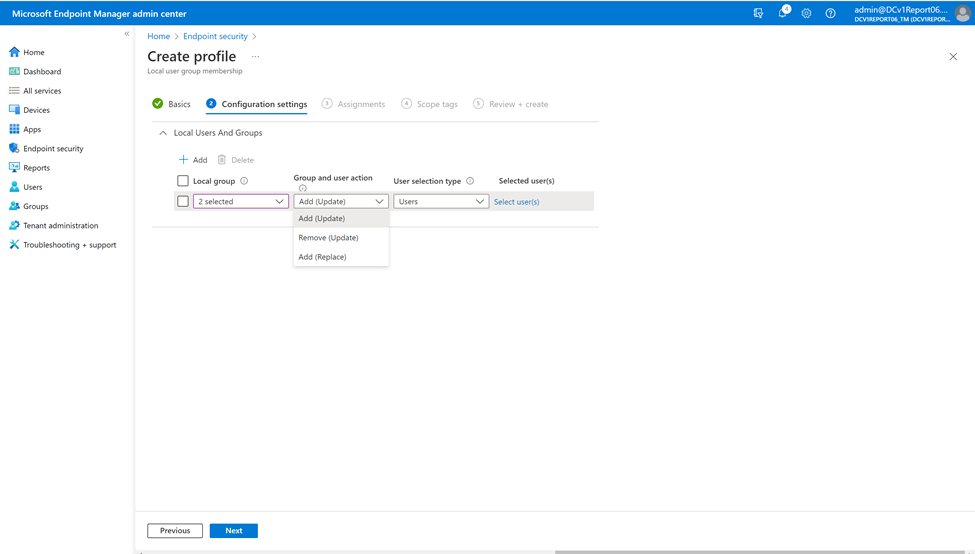
To start configuring these settings, you can create multiple rules to manage which built-in local group you wish to change, the group action to take, and the method to select the users.
Once one or more local groups have been selected, you can choose the group action to take:
- Add (Update): Adds members to specified group while keeping the current group membership intact.
- Remove (Update): Removes members of specified group while keeping the current group membership intact.
- Add (Replace): Replaces current membership of specified group with newly specified group.
Note: The same local group cannot have a rule to both Update and Replace members. If this is configured using Microsoft Graph (not recommended), the Replace action will take precedence.
For more information, the CSP documentation.
Next comes selecting the method to identify the members you want to add to or remove from the specified group. There are two options to do this:
- Select the Azure Active Directory (Azure AD) users and user groups.
- Input the manual Azure AD and/or AD users and user groups.
If choosing the second option, you can enter a list of the users and user groups as the identified members to be managed for the specified groups. This can be helpful in scenarios where you want to manage your on-prem AD users with the policy. The supported formats are the member’s username, domain\username, or SID. When referencing Azure AD groups, you must use the group’s SID. Azure AD group SIDs can be obtained using Graph API for Groups. Any entries that are not supported will be skipped and not applied to the targeted device. For more information on how to enter users in the correct format, see the CSP documentation.
Once you are satisfied with the configured rules, you can proceed to apply scope tags and targeting, and then review the policy contents before saving. As targeted devices check in to the policy, you can view the status of the devices and users to determine whether they are in success or error. This policy will use the new reporting experience that settings catalog policies do. In the Per-setting status report, the group of rules will be reported back as one setting. If there is an error in one of many rules, the successful rules will still be applied and skip the one with the error. Rules are sent down to the device in the order of configuration. For more information about reporting, see Intune reports and Use the settings catalog to configure settings on Windows and macOS devices.
We recommend you apply one local user group membership policy to a given device to avoid conflicts.
Read more about the new policy settings in the Manage local groups on Windows devices Endpoint security documentation.
If you have any questions or feedback on the new template, reply to this post or reach out to @IntuneSuppTeam on Twitter.