This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Overview
IoT and OT devices are increasingly becoming a major attack vector for organizations of all sizes. While the impact of these attacks can paralyze entire industries and countries, defending against these attacks has traditionally involved disparate tools that often suffered from poor integration and disconnect from the overall security program. And while IT and OT environments have historically been disconnected, securing them effectively requires a unified approach.
Today, we are excited to announce the public preview of our Defender for IoT solution for Microsoft Sentinel. With this solution, Microsoft Sentinel delivers the first in the industry native SOC experience for IT and OT environments. Available within a click of a button, the native OT security capabilities of Defender for IoT allow organizations to discover security issues in OT before they attract any threat actors and detect threat activity that uses operational technologies to enter an environment, move laterally, or cause physical damage and disruption to the operations. The integration equips security teams with expanded visibility and control across all their OT assets, starting from asset discovery, to vulnerability management, to incident response.
Within the same workflows, analysts can now track and update their entire inventory of OT devices, monitor these devices for potential security issues and vulnerabilities, and respond to incidents – not just within the context of OT, but with the benefit of visibility across the entire security program. All OT-related alerts, compromised assets, network connections and events and PCAP access are now part of the analyst workflows, providing customers with a complete control across all devices and assets.
In this blog, we'll we cover the main capabilities of Defender for IoT solution for Microsoft Sentinel, including:
- Integrate IoT/OT Security context and processes with Sentinel in 2 clicks.
- Streamline the IoT/OT SOC investigation experience with dedicated built-in features.
- Automate response for IoT/OT threats with out-of-the-books SOAR Playbooks.
- Enable the OT SOC by providing SOC analysts OT domain monitoring capabilities.
Capabilities
1. Integrate IoT/OT Security context and processes with Sentinel in 2 clicks
The SOC teams usually spend a large amount of time integrating their IT, IoT, and OT SOC and build processes around them.
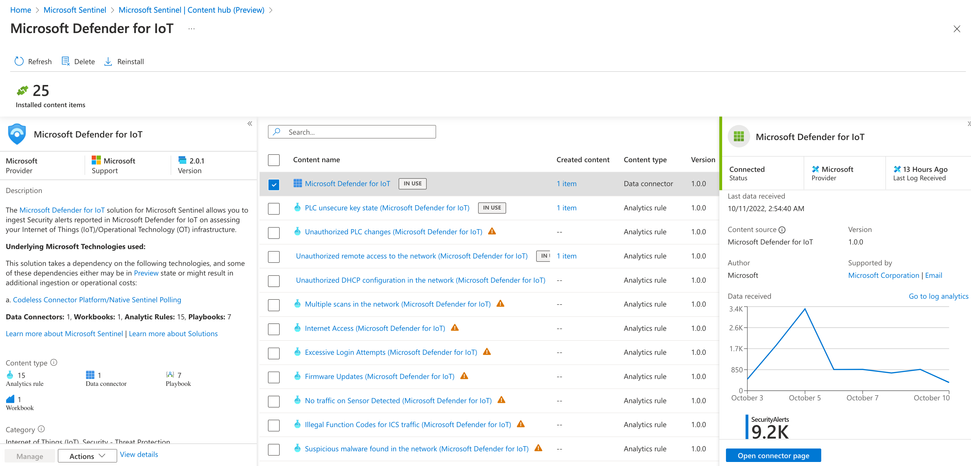
SOC teams can now easily integrate IoT/OT alerts, context and processes into Sentinel with the new Defender for IoT and Sentinel joint solution with just two clicks by deploying the Defender for IoT solution package from the Sentinel content hub and enabling the data connector to begin streaming. Not only are OT/IoT threat detections streamed to Sentinel, but also context information, such as asset data, owner information, vulnerabilities, crown jewels, business impact, geolocation, and many others.
As part of the Defender for IoT solution package, out-of-the-box items include a Data connector, analytic rules that assist in defining what constitutes an incident within the SOC, SOAR playbooks for automating IoT/OT incident response, and a workbook dashboard to visualize and measure the OT environment.
2. Streamline the IoT/OT SOC investigation experience with dedicated built-in features
The integration between Defender for IoT and Sentinel enable SOC teams to detect, investigate and respond to OT and IoT threats efficiently and effectively by utilizing the built-in features available as part of the solution, including:
- One single pane of glass for IT/OT incidents with the ability to filter easily ‘Defender for IoT’ incidents and search incidents by their physical location
- View enhanced OT/IoT incident data to identify the incident business impact and triage quickly
- Click a deep link to navigate to the expert system (Defender for IoT) to view PCAPs, change alert policies, view the backplane scheme of a device that can be part of the investigation of a more complex incident, and more, without switching contexts.
- Incident mapping to ICS MITRE ATT&CK tactics and techniques
- Summary of the IoT/OT assets (entities)
- Built-in mapping to physical locations (coming up soon) - monitor the detected threats and understand their impact on the business in the context of the incident geo location (site, zone, sensor)
- Investigate further incident with IoT device entities
By selecting an IoT device entity from the Entities list to open its IoT device entity page.
The IoT device entity page provides comprehensive contextual device information, populated automatically from Defender for IoT, including:- Device business impact by mapping to device physical location (site, zone, sensor)
- Basic device details such as Type, Vendor, Model, Operating System, Firmware version
- Device importance, to identify sensitive devices on the network that might be impacted (a.k.a. “crown jewels”)
- Device owner contact information to enable SOC contact quickly identify the relevant OT Engineer for further investigation
- Navigate easily to the device page on the expert system (Defender for IoT) for more deep investigation
- A timeline showing all alerts and activities related to the device on the selected timeframe
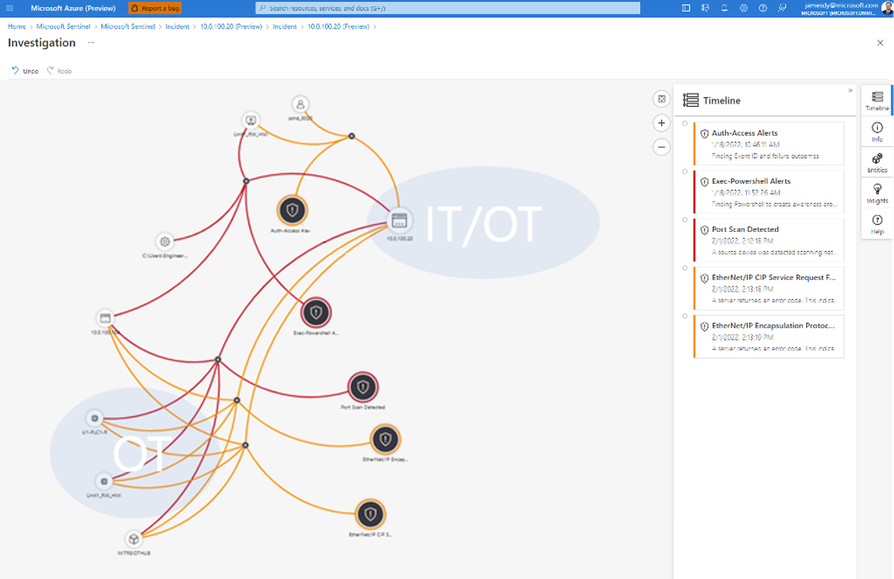
- Investigate OT incidents using Sentinel investigation graph
The investigation graph helps you understand the scope of a potential OT security threat and identify the root cause by correlating relevant data with each entity involved - Collaborate more effectively between the SOC and the OT Engineers
The status of alerts in Defender for IoT are automatically updated following the SOC tracking the incident - using the playbook Update alert statuses in Defender for IoT
3. Automate response for IoT/OT threats with out-of-the-box SOAR playbooks
With years of experience, Microsoft Defender for IoT includes out-of-the-box playbooks that are specifically tailored for IoT/OT threats. These playbooks provide the following functionalities:
- Automatically close incidents - This playbook automatically closes incidents created from such alerts during a specified maintenance period.
- Send email notifications by production line - Sends mail to notify specific stakeholders about alerts and events that occur in your environment.
- Create a new ServiceNow ticket - Opens a ticket in ServiceNow each time a new Engineering Workstation is detected.
- Automate workflows for incidents with active CVEs - Adds active CVEs into the incident comments of affected devices. An automated triage is performed if the CVE is critical, and an email notification is sent to the device owner, as defined on the site level in Defender for IoT.
- Triage incidents involving highly important devices - Updates the incident severity according to the importance level of the devices involved.
- Send email to the IoT/OT device owner - Sends an email with the incident details to the device owner.
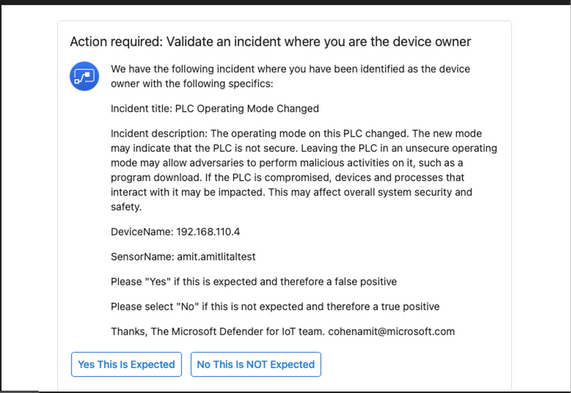
Let's take the 'Send email to the IoT/OT device owner' playbook as an example:
This playbook sends an email with the incident details to the device owner as defined on the in Defender for IoT, so that they can start investigating, even responding directly from the automated email.
The response options include: “Yes, this is expected” (false positive), which closes the incident automatically and notifies the SOC analyst, or “No, this is not expected” (true positive), which changes the incident's status to Active and assigns it to the relevant OT Engineer.
4. Enable the OT SOC by providing SOC analysts OT domain monitoring capabilities
In addition to providing purpose-built tools to allow SOC analysts to handle and investigate OT security incidents, the solution also provides the SOC analysts enhanced visibility and analysis capabilities with the Sentinel tools they are used to:
- Visibility to the full device inventory
By leveraging the solution workbook that breaks up all OT devices by different criteria and statistics: Active devices, devices by Site/Zone/Sensor, sortable list of all devices by number of alerts, CVEs, recommendations, etc. - Visibility to vulnerabilities in OT domain assets
By leveraging the same workbook, this time breaking up all detected CVEs by severity, site and vendors as well as providing context sensitive lists analyzing specific CVEs, their critically and their risk potential across all OT devices. - Correlate detected OT incidents to MITRE ATT&CK Matrix for ICS
SOC analysts can identify the tactics and techniques the organization is most targeted by, predict post-compromise adversary behavior and take precautionary - Optimize SOC workflows and reduce alert fatigue
By utilizing out of the box analytics rules built based on years of experience in the OT cyber domain. The SOC engineer can decide directly from Sentinel which threats use cases detected by Defender for IOT should be monitored by the SOC by enabling specific rules and customizing them for their needs. - Detect advanced threats spanning both IT and OT environments
By analyzing logs and alerts flowing from the two domains. In many cases an OT cyber-attack will start from the IT domain (for example, taking control of a machine in the IT domain to penetrate the OT domain). As the same Sentinel workspace collects activities and alerts from both domains, the SOC engineers can easily create analytics rules that fuse and cross correlate both domains.
Planned Enhancements
Here are some of the other exciting capabilities we’re developing:
- Extension of Sentinel investigation graph with additional OT network context
You can dive deeper and investigate any OT entity displayed in the graph by selecting it and choosing between different extension options. In addition to the already supported options, we are introducing a new extension enabling you to view associated OT network connections. - MITRE ATT&CK® for ICS Matrix coverage.
We introduce a native MITRE matrix mapping that that provides visibility for the organization protections coverage
- Out-of-the-box fused IT/OT Incidents
In Sentinel, we introduce a set of out-of-the-box analytic rules that detect incidents that cross-correlate both IT and OT based on real-life use cases. - IoT Device Entity Page improvements
More exciting content will be added to the IoT entity page, including: Insights & recommendations, vulnerabilities and more to enhance the security posture.
And more to come..
Learn More
- Solution package: Defender for IoT solution package in Microsoft Sentinel
- Ignite on-demand session: Defending against OT/ICS threats with an OT-Enabled SOC
- OT Incidents investigation tutorial Investigate Microsoft Defender for IoT incidents with Microsoft Sentinel
- IOT entity page: IoT Entity Page blog
- Solution webinar: IT/OT Threat Monitoring solution with Defender for IoT and Sentinel Webinar
- Release notes: Microsoft Defender for IoT Release Notes | Microsoft Docs