This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Overview
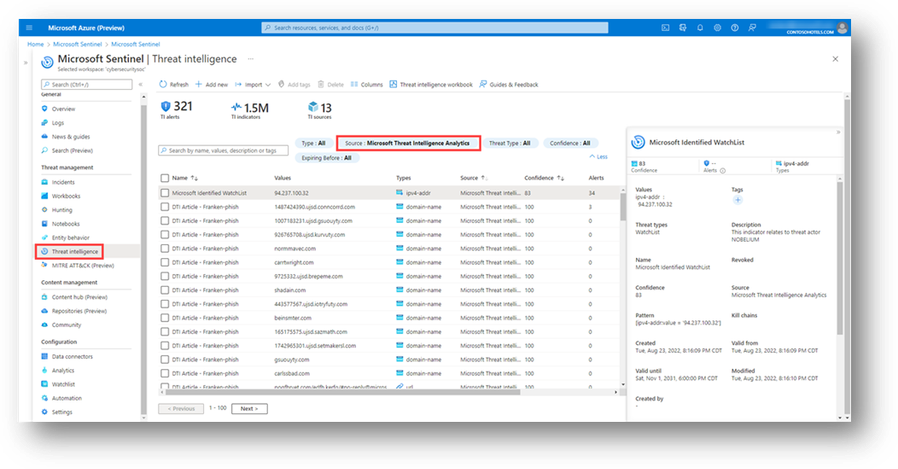
Microsoft Sentinel users can use Microsoft Defender Threat Intelligence (Defender TI) 's threat intelligence indicators to generate detections within Microsoft Sentinel. Microsoft Sentinel users with appropriate permissions can enable the "TI map" Analytic rule templates, which will allow the correlation of Defender TI's threat intelligence phishing and malware feed indicators along with its' article indicators against the user's Log Analytics workspace every hour. Suppose there is a correlation between the Defender TI indicators and the user's logs. In that case, an incident will generate, and the indicator that triggered the incident will write to Sentinel's Threat intelligence table. Therefore, the user can then view the indicator in their Microsoft Sentinel Threat intelligence blade and the associated incident in the Incidents blade. Users will need to filter by the Microsoft Threat Intelligence Analytics source to identify Defender TI phishing, malware, and article indicators that have generated incidents.
Figure 1 – Threat Intelligence indicators, filtered by Microsoft Threat Intelligence Analytics source
How to locate the "TI map*" Analytic Rule templates
Microsoft Sentinel users with appropriate permissions can access the "TI map" rule templates by accessing the Analytics blade, navigating to Rule Templates, and searching "TI map" in the search bar. Here, they can view the TI map rule templates available to enable or disable (if already in use). For more information on how to enable Analytic rule templates, see Microsoft Sentinel's built-in threat detection rules. For more information on Microsoft Sentinel's threat intelligence analytic rules, see New Threat Intelligence features in Microsoft Sentinel - Microsoft Tech Community and Work with threat indicators in Microsoft Sentinel | Microsoft Learn.