This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Target User Functions
Defender TI datasets are most relevant for enabling quicker and better decision-making throughout daily operations for users operating within the capacity of one of the following functions:
 Security Operations Security Operations
|
Using data collected from various cyber defense tools to analyze events occurring within an environment to mitigate threats. |
 Incident Response Incident Response
|
Investigating, analyzing, and responding to cyber incidents within a network or enclave. |
 Threat Hunting Threat Hunting
|
Proactively searching for malware or attackers hiding within a network. |
 Cyber Threat Intelligence Analysis Cyber Threat Intelligence Analysis
|
Identifying and tracking cyber threats to an organization and working with stakeholders to reduce risk. |
 Cybersecurity Research Cybersecurity Research
|
Developing new concepts or novel approaches to identify and defend against cyber threats. |
Use Cases
Defender TI datasets support various investigative use cases, ranging from better understanding a threat identified by your security operations center targeting you to rapidly identifying Internet infrastructure stood up to impersonate your organization. The ability to enable threat investigations at scale and automate security operations lead to proactive denial of threat actor compromise and smarter, faster incident response.
Figure 1 – Identify, accelerate, and integrate Defender TI
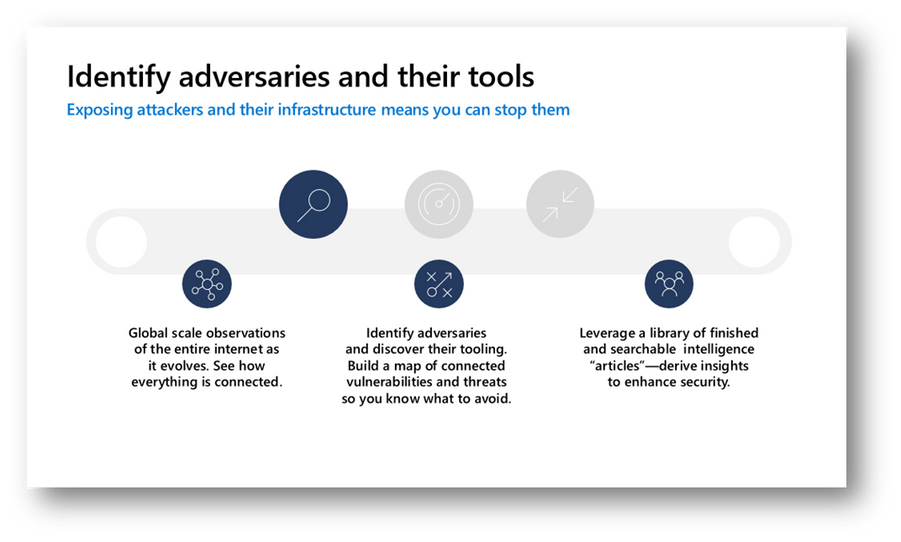
Figure 2 – Using Defender TI to identify adversaries and their tools
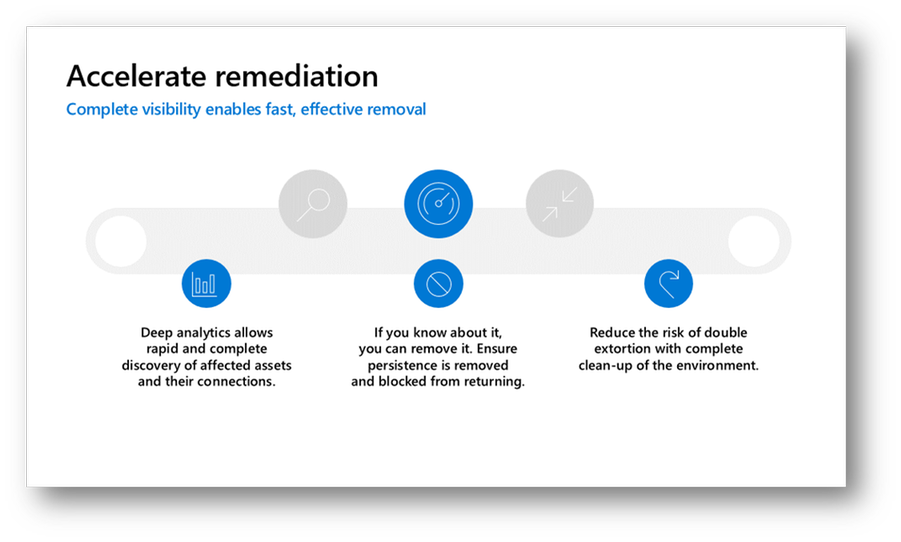
Figure 3 – Using Defender TI to accelerate remediation
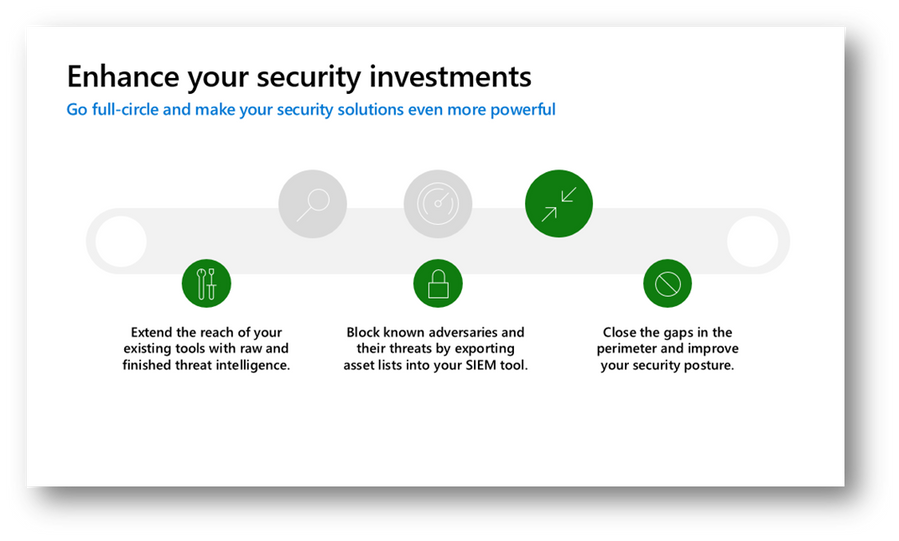
Figure 4 – Using Defender TI to enhance your security investments
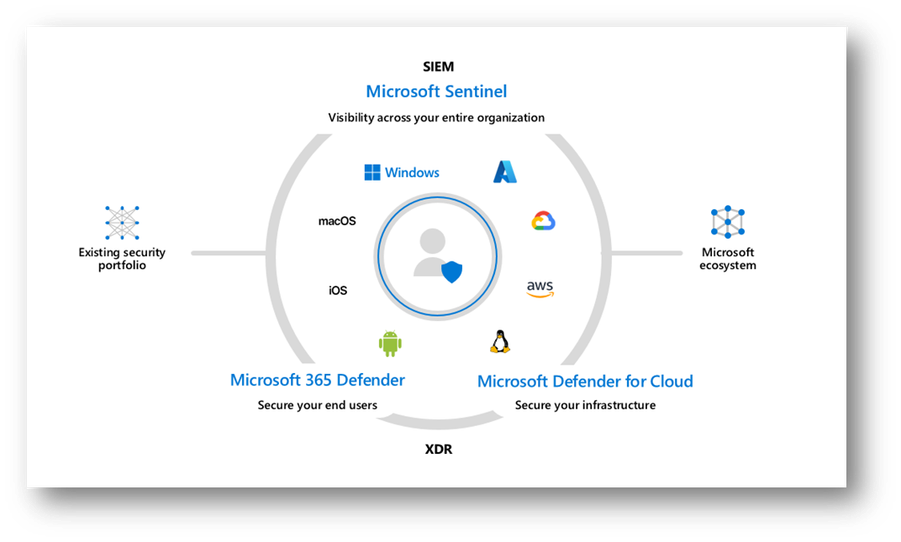
Figures 5 and 6 – How Defender TI ties into Microsoft’s SIEM & XDR ecosystem
Outlined below are some common use cases framed at a more tactical level.
Identify Existing Threat Intelligence
The ability to quickly identify existing finished intelligence that could be relevant to a current investigation is top of mind within the Defender TI portal. This library of finished intelligence exists in searchable articles, allowing analysts to derive insights and enhance security.
Data Enrichment
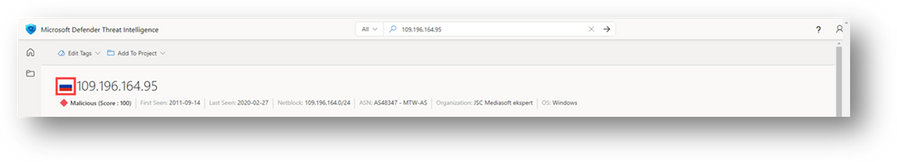
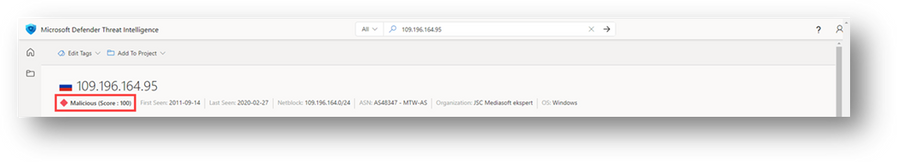
Enriching potential indicators of compromise, such as IP addresses or domain names, is a way to gather the data necessary to allow an analyst to decide quickly whether something is good or bad. An example of enrichment could be an indicator has appeared within cybersecurity reporting or is categorized as malicious by external entities. An enrichment like geolocation may serve as a critical component for investigative use cases that require knowing from what part of the world an event originated.
Figure 7 – IP address geolocation enrichment
Figure 8 – IP address reputation enrichment
Infrastructure Chaining
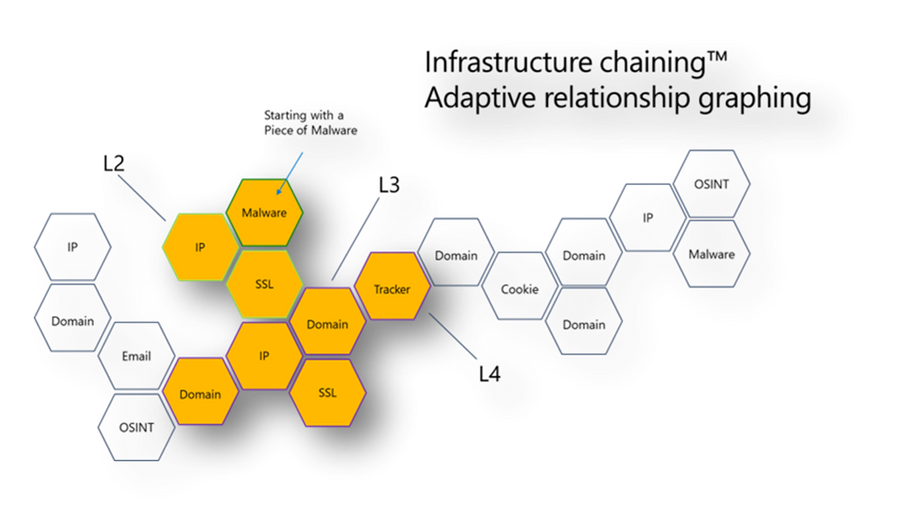
Infrastructure chaining is a method by which previously unknown relationships between indicators are brought to the surface. The illustration below shows how starting with one artifact—in this case, a malware sample—leads to identifying more entities that could serve as investigative leads for incident response or threat hunting. The Internet emits signals, which you’ll learn more about in module 2. These signals inform a process that we’ve labeled as threat infrastructure analysis. Threat infrastructure analysis is a research process that leverages the inherently interconnected nature of the Internet to identify related entities. It’s the interconnected nature of the signals. The Internet is made up the same way, connecting datasets together. For example, a domain will have an IP address, or an email will be used to register a domain. This process is important because these operators conducting attacks are humans, and they will make mistakes in evading detection. These mistakes can be used to our advantage to identify other related indicators of compromise tied to that actor. Or, you may find that specific registrar allow for malicious activity to continue to take place. In other words, these registrars may not action domain takedown requests. As a result, actors may favor registering their domains with those registrars, which can be great intel to prevent and quickly respond to attacks.
Figure 9 – Infrastructure chaining concept
For more on infrastructure chaining, check out the following video.
Monitoring Internet Infrastructure Changes
As attackers pivot to evade detection, the ability to traverse a chain of indicators from old to new may provide opportunities to proactively set up defenses within security tools. In the simple case where we can identify an IP address as under the control of a bad actor, we can presume that any domain that begins resolving to it in the future is also malicious.
Collaborating on Investigations
Since analysts are usually not working in isolation, sharing work is paramount to ensuring people are not duplicating efforts and that there is a record of actions taken for a given case. Defender TI Projects are a lightweight case-management feature that enables analysts to work together in collecting indicators of compromise related to an investigation. This could be in response to an incident or to proactively fingerprint an actor’s infrastructure that may be targeting their industry or organization.