This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
On August 2022, Microsoft Sentinel solution for SAP was made General availability (GA). Together with releasing the MS Sentinel for SAP solution, new additional OOTB content has been added. This blog covers five new Data Exfiltration rules included with the Microsoft Sentinel solution for SAP (these rules are currently in preview).
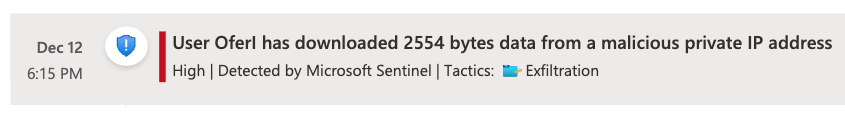
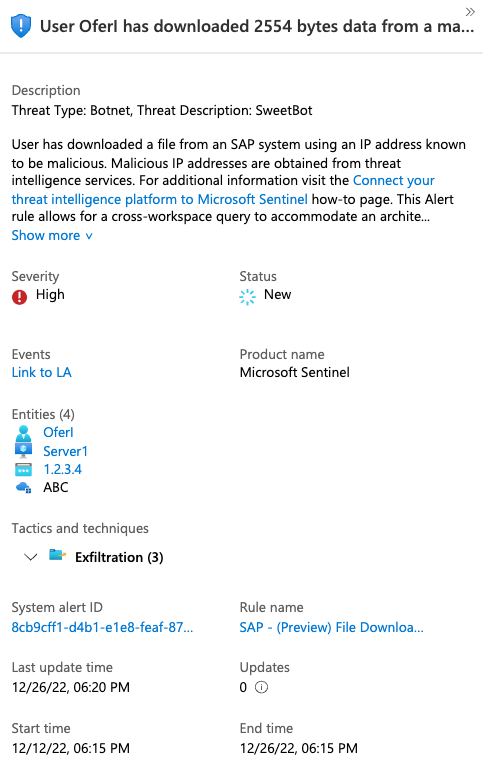
1. File Downloaded from a Malicious IP Address
This rule alerts when a user downloads a file from a SAP system using an IP address known to be malicious. Malicious IP addresses are obtained from Microsoft Sentinel Threat Intelligence. To enable this rule, the Microsoft Sentinel workspace must have both the SAP solution and onboarded threat intelligence indicator feeds. Threat intelligence platform is one option for customers to import third party threat indicators of various types into their workspace. For example, file hashes, email with suspicious attachments, and of course malicious IP addresses.
This analytics rule correlates the IP addresses from which file download activities were observed on the SAP security audit log with malicious IP address obtained by your TIP.
In addition, this alert rule allows for a cross-workspace query to accommodate an architecture where the threat intelligence data resides in a different workspace than the one which holds the SAP data.
Configuration options - determine which system roles are relevant for this alert (production is default)
2. SAP - (Preview) Sensitive data saved into a USB drive
This rule alerts when SAP data is exported via files and saved to a recently mounted USB drive, following execution of a sensitive transaction, sensitive program or direct access to a sensitive table. The alert looks for all recently mounted USB drives using the Microsoft defender for endpoint’s data type DeviceFileEvents, and then matches those against the sensitive file download target.
Configuration options
- Determine which system roles are relevant for this alert (production is default)
- Determine which transactions are considered sensitive using the 'SAP - Sensitive Transactions' watchlist
- Determine which programs are considered sensitive using the 'SAP - Sensitive Programs' watchlist
- Determine which tables are considered sensitive using the 'SAP - Sensitive Tables ' watchlist
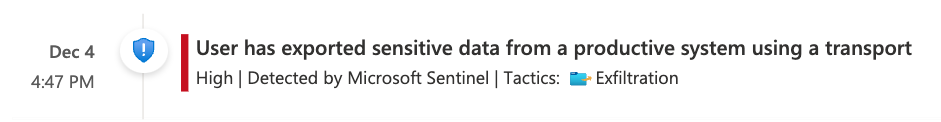
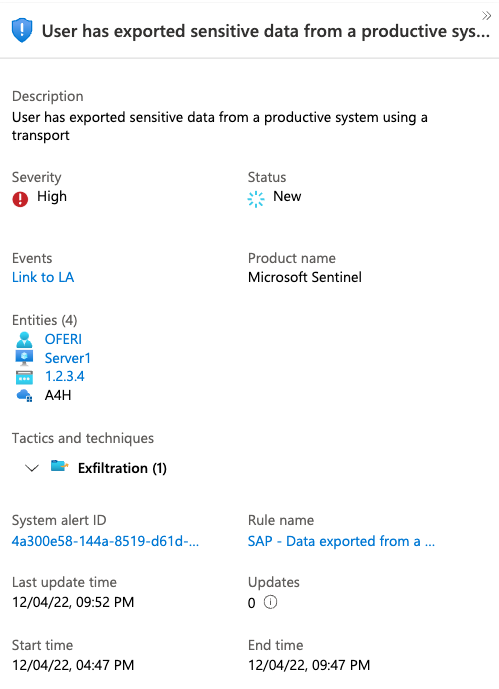
3. SAP - (Preview) Data exported from a production system using a transport-
Transports in SAP are like pull requests and are normally created in a development system. This alert rule triggers incidents with medium severity when a transport is released from a production system, bearing data taken from any table, and will create a high severity incident when the export includes data from a sensitive table. The sensitivity of a table is defined using the 'SAP - Sensitive Tables' watchlist.
For this rule to be enabled, the user must ingest the SAP CR log and add their sensitive tables to those already included in the the 'SAP - Sensitive Tables' watchlist.
Configuration options -
- Determine which system roles are relevant for this alert (production is default).
- Exclude system users which are OK to export sensitive data using the transport system by adding those users in the SAP_User_Config watchlist with a tag of "ExportSensitiveDataOK", or by specifying SAP roles or profiles.
- SAP - (Preview) Printing of potentially sensitive data
This alert identifies when a user has requested printing and /or has printed data which is potentially sensitive. Data is considered sensitive if it is obtained by using a sensitive transaction, by executing a sensitive program, or by directly accessing a sensitive table.
This analytics rule requires both the SAP security audit log and the SAP spool logs to be ingested.
Configuration options
- Determine which system roles are relevant for this alert (production is default)
- Determine which transactions are considered sensitive using the 'SAP - Sensitive Transactions' watchlist
- Determine which programs are considered sensitive using the 'SAP - Sensitive Programs' watchlist
- Determine which tables are considered sensitive using the 'SAP - Sensitive Tables ' watchlist.
- SAP - (Preview) High volume of potentially sensitive data exported
This alert identifies a high volume of data exported via files in proximity to an execution of a sensitive transaction, a sensitive program or direct access to sensitive tables. This alert checks if a user has downloaded an accumulated amount of sensitive data (8MB, configurable via a parameter) within a set sliding window of time.
Configuration options:
- Determine which system roles are relevant for this alert (production is default)
- Determine which transactions are considered sensitive using the 'SAP - Sensitive Transactions' watchlist
- Determine which programs are considered sensitive using the 'SAP - Sensitive Programs' watchlist
- Determine which tables are considered sensitive using the 'SAP - Sensitive Tables ' watchlist