This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
When it comes to protecting servers in hybrid and multicloud environments, Microsoft Defender for Servers as part of Microsoft Defender for Cloud is the solution you might be looking for. However, with all the features, dependencies, and complexity, it might become challenging to always make the right decision when planning, integrating, and deploying Defender for Servers across your environment. With this blog, we are focusing on deployment and integration of Microsoft Defender for Endpoint with Microsoft Defender for Servers on Linux machines.
Microsoft Defender for Servers is available in two different plans, both of which include integration and automated deployment of Microsoft Defender for Endpoint for both, Windows and Linux machines.
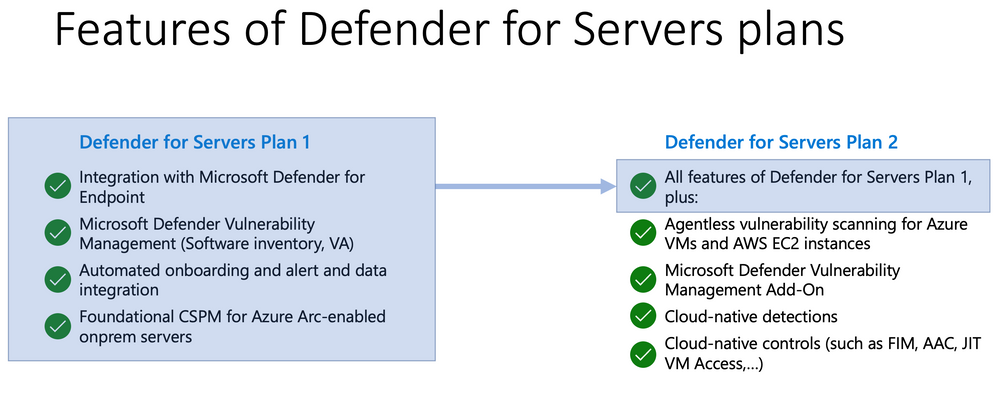
To learn more, see this table about supported features for VMs and servers in Defender for Cloud. Also, to learn more about Defender for Servers plan features, see this documentation.
How to enable Defender for Endpoint integration for Linux machines
Microsoft Defender for Endpoint for Linux integration has been introduced to Defender for Servers back in summer 2021. At this time, Defender for Endpoint integration for Windows servers has been part of the product for quite a while already, and when introducing Linux support, we added an opt-in method for existing customers to decide at which point in time they would like to enable integration and deployment for their Linux machines. Since then, Defender for Endpoint integration will be enabled for Windows and Linux by default on any new subscription when Defender for Servers is enabled for the first time. However, in case the following three dependencies are true, Defender for Endpoint for Linux integration is not automatically enabled:
- Your subscription was created earlier than August 2021
- In August 2021, your subscription was configured to have Defender for Endpoint integration enabled
- In August 2021, your subscription had Defender for Servers enabled
In this scenario, you will see the opt-in capability in your subscription’s Integrations blade within Defender for Cloud:
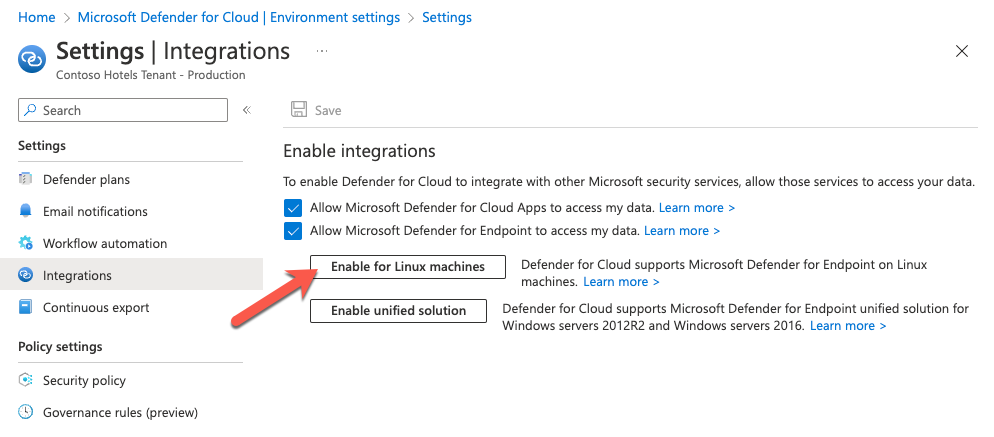
In the figure above, you see there is a second button to enable Defender for Endpoint’s unified solution for Windows Server 2012 R2 and 2016 machines. To learn more about this option, please see this article.
We know that in large environments, it might be challenging to find all the subscriptions that don’t have enabled Linux integration with Defender for Endpoint, yet. This is why we are offering several at-scale capabilities to enable the integration in your environment.
Enabling Defender for Endpoint integration for Linux on multiple subscriptions
In Defender for Cloud’s Overview blade, we are introducing a new Insights campaign that gives you visibility into subscriptions that do not have Defender for Endpoint integration enabled for Linux machines.
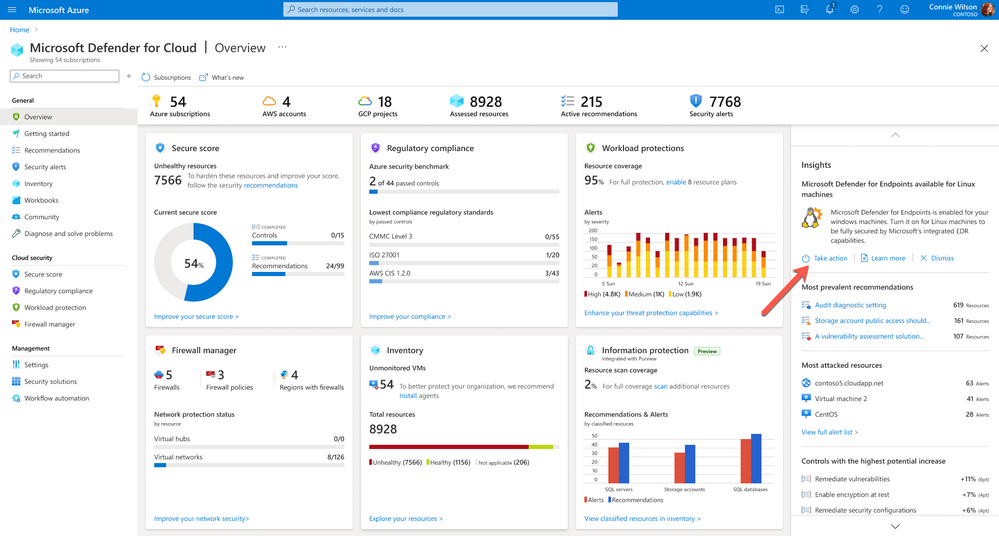
You can use this new campaign to directly enable integration for Linux machines from this Overview blade by clicking the Take Action link.
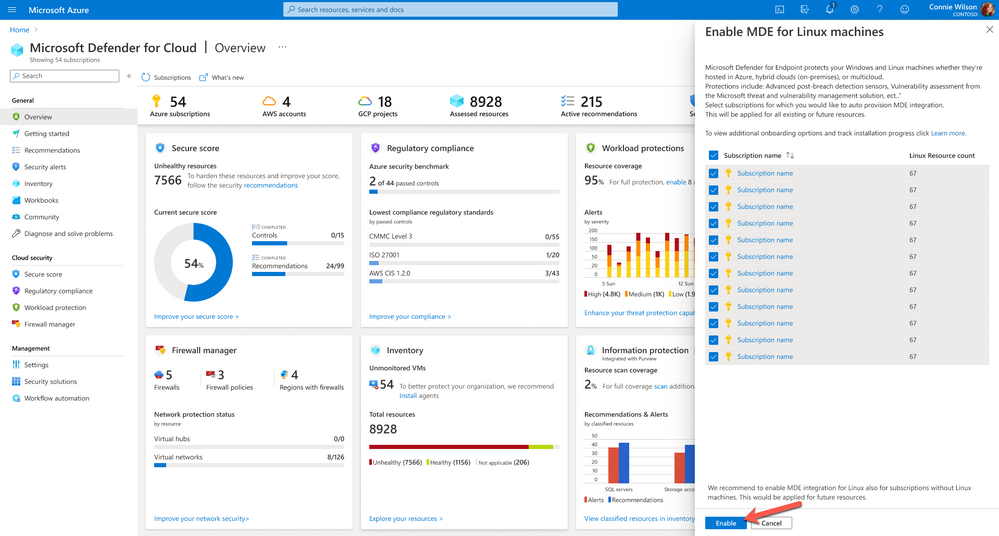
It will then show you all subscriptions that don’t have integration for Linux machines enabled, including the amount of affected Linux machines in each subscription. You can then select some or all of them and enable the integration at scale. Once done, you can track the deployment progress by clicking the Track Deployment link.
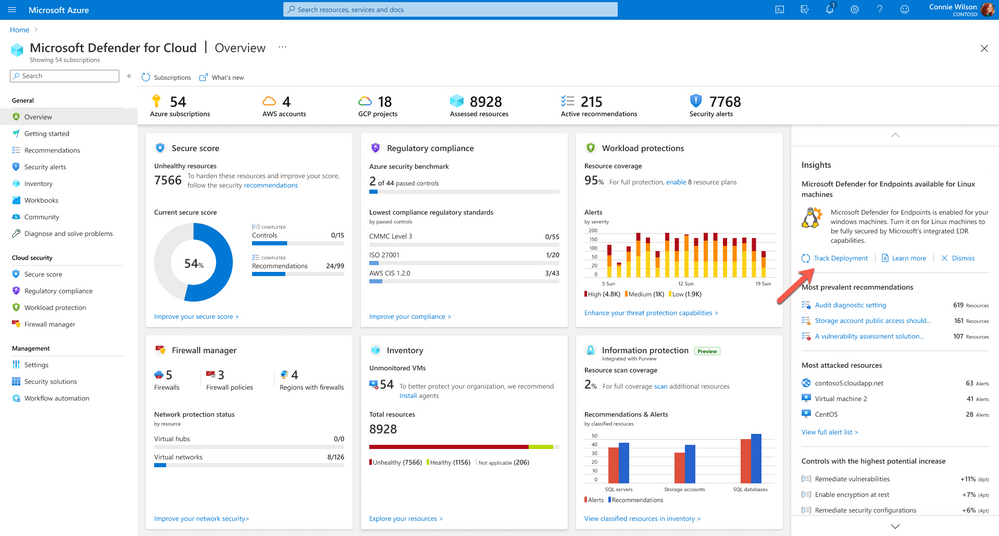
This link will redirect you to a custom workbook that we have published on Github and which you can deploy to your environment.
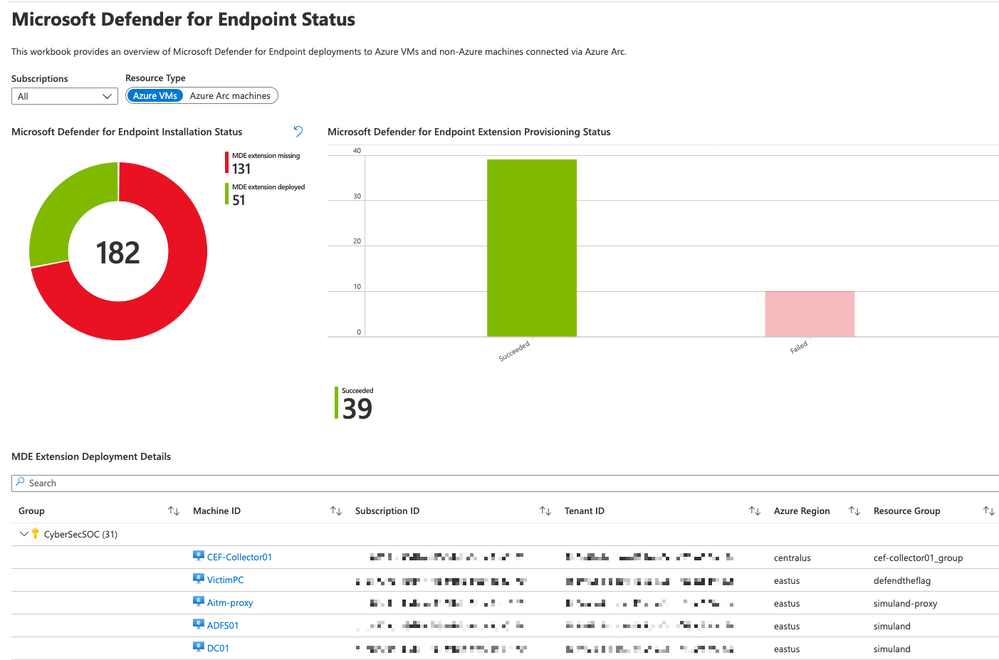
The workbook will show you the current deployment status of Defender for Endpoint extensions to your Azure VMs and Azure Arc machines, and if the installation and onboarding was successful, or if it failed.
Enable integration via PowerShell
A second option we are providing is a PowerShell script that will enable integration for Linux machines on all of your subscriptions. The script will check if Defender for Endpoint integration is enabled at all, and if not, enable it for both, Windows and Linux machines. In case it already is enabled for Windows, Linux integration will be enabled in addition.
We have also published the PowerShell script in the Defender for Cloud Github repository.
Enable integration via REST API
When enabling Defender for Endpoint integration for Linux machines using the Defender for Cloud UI, clicking the button, or using the insights campaign will leverage a REST API call against your subscription(s). You can also use this API call in your own automations, ARM templates, or Azure Policy definitions.
To enable Defender for Endpoint integration for Linux machines on a subscription, use the following API call against the microsoft.security/settings REST API provider:
| Parameter | Value |
| REST Method | PUT |
| API URI | |
| API Version |
2022-05-01 |
| JSON Body |
Conclusion
While Defender for Endpoint integration is automatically enabled on new subscriptions, or when enabling Defender for Servers for the first time, you might have subscriptions in your environment that still don’t have the latest integration features enabled. For these subscriptions, you will now get the visibility in Defender for Cloud’s Overview dashboard and can use a variety of automation capabilities to enable Defender for Endpoint integration for Linux machines at scale.
Acknowledgements
Specials thanks to Gal Fenigshtein for the strong collaboration on this topic and for reviewing this blog.
