This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Many of our customers face challenges installing agents on all of their devices and in some cases, not all Windows-based devices support the agent if they are using older versions of Windows.
To combat these challenges, we’re excited to share a new capability within Microsoft Defender Vulnerability Management to remotely scan Windows-based devices that do not have agents installed. Authenticated scans for Windows provide the ability to remotely target by IP\range or hostname and scan Windows services by equipping the tool with credentials to remotely access the machines. This is applicable for devices that do not have the Defender Vulnerability Management or Defender for Endpoint agent deployed so organizations like yours can get complete vulnerability assessment coverage without reliance on an agent. Defender Vulnerability Management add-on and standalone customers can take advantage of this new feature today.
Along with the release of the ability to remotely scan Windows devices, we have made updates and added new functionality to the remote scan capability (some of which are already available for network devices).
One place for managing authenticated scans
You can access authenticated scans in the Microsoft 365 Defender Portal through Settings > Device Discovery. This makes managing discovery and scanning of non-Microsoft Defender for Endpoint onboarded devices easier under the same location.
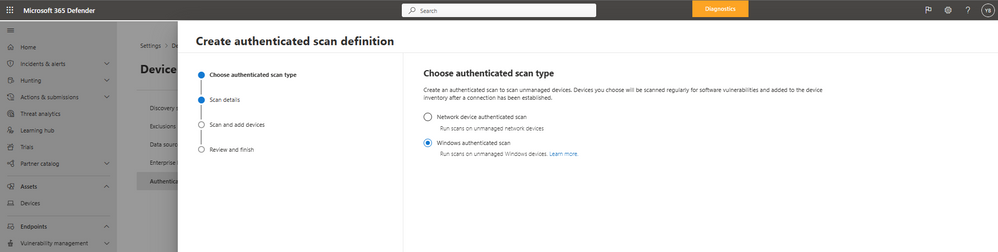
Create an authenticated scan for Windows devices
Once in the authenticated scan section, select “add new scan” to create an authenticated scan for Windows.
New fields for authenticated scans allows for customization to fully support your organization's needs
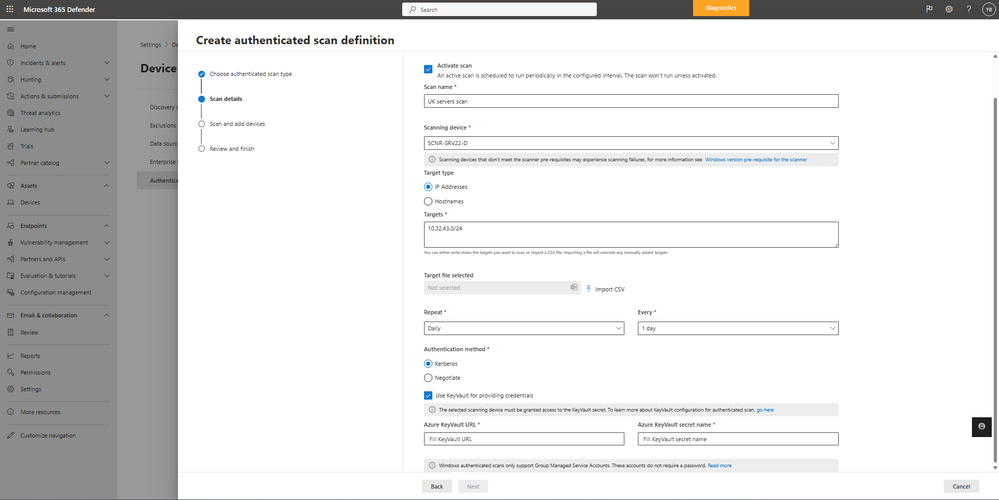
- Define scan interval – provides ability to configure an interval per authenticated scan or set it to run once.
- Windows authenticated scan gMSA support - For better security we have moved to using a Account (gMSA) instead of username\password.
- Define scan targets by hostname or upload a CSV
- Azure Key Vault support
- Scan definition API improvements
- Scan history for an ability to better understand scans
Set up your scanner device and devices to be scanned
To set up your scanner device and the devices to be scanned, you’ll need to use a gMSA account. To create a gMSA for scanning please see create a scanning account in our documentation.
The gMSA is then used by the scanning device to authenticate and remotely access the devices to be scanned. Further configurations for the gMSA account are also required on the devices to be scanned. For more information, see devices to be scanned section in our documentation.
We hope you enjoy this new feature. See below for more information about authenticated scans for Windows:
- For more information on the updates read more in our documentation on MS Learn.
- For more information on the APIs for managing scans, read our API documentation on MS Learn.
- Read more about Group Managed Service Accounts here.
__
Microsoft Defender Vulnerability Management is in public preview. Explore premium capabilities of Microsoft Defender Vulnerability Management such as this one and more by signing up for a free trial of Defender Vulnerability Management add-on and standalone here.