This post has been republished via RSS; it originally appeared at: IIS Support Blog articles.
I have come across a few instances Root Cause Analysis (RCA) was requested for issues related to a web application that were caused by factors such as:
- Changes in permission of the Application Root folder.
- Web site being deleted.
- SSL certificate binding modified.
Furthermore, there were times when using Process Monitor - Sysinternals | Microsoft Learn was not possible because the problem was intermittent, such as when files were being written to C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys at irregular intervals.
The steps below assisted me in enabling auditing to log the necessary events in each scenario. Please feel free to check other parts of this blog:
- Part 1 -
- Part 2 -
- Part 3 -
Scenario 4: Files being written to folder:
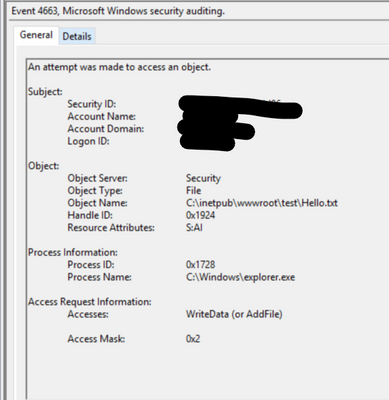
- 4663(S): An attempt was made to access an object , event can be referred to see the process and user writing file to folder or file. The event will look like below:
- Audit the access of global system objects (Windows 10) - Windows security | Microsoft Learn. Please refer below steps to enable the auditing for files being written to C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys in this example.
- Apply a basic audit policy on a file or folder (Windows 10) - Windows security | Microsoft Learn
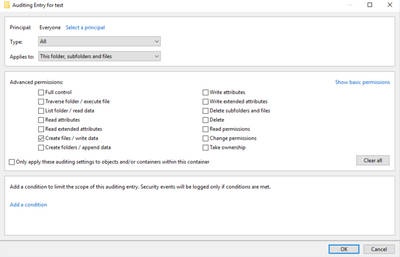
- We can enable auditing for create files/ write data, please refer below (C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys or <folder to be Audited>>> properties >> security >> advanced >> auditing >> add >> show advanced permissions):
2. Enable File System Auditing:
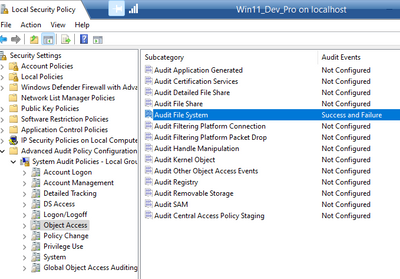
- Open Local Security Policy Editor (run >> secpol.msc)
- Advanced Audit Policy Configuration >> System Audit Policies >> Object Access >> Audit File System >> configure for success and failure.
- Reference:
Happy Troubleshooting!