This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
This is the sixth in the six-part series about using BitLocker with Intune. BitLocker is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers. It provides the maximum protection when used with a Trusted Platform Module (TPM) version 1.2 or later versions. BitLocker may be configured in Intune for Windows 10 and 11 devices using one of three methods:
- An endpoint protection profile
- An endpoint security disk encryption profile
- A settings catalog profile
The endpoint protection and endpoint security disk encryption profiles use BitLocker configuration service provider (CSP) to configure encryption of PCs and devices. The settings catalog profile, however, uses a combination of BitLocker CSP and ADMX backed settings. The ADMX settings provide the BitLocker group policy settings, which can be used to manage BitLocker tasks and configurations users can perform.
In this article, we demonstrate how to configure BitLocker on Windows 10 and 11 devices via the Intune settings catalog.
To configure BitLocker with the settings catalog, in the Microsoft Intune admin center, navigate to Devices > Windows devices > Configuration profiles. Select + Create profile and choose Windows 10 and later for the Platform and Settings catalog for the Profile type, then select Create. Name the profile in the Basics tab of the Create profile pane and then, on the Configuration settings tab, select +Add settings. Type “BitLocker” in the search box to find all related settings.
Category options will appear with either the prefixes Administrative Templates or BitLocker. Administrative Templates settings are backed by ADMX, and those configured with BitLocker CSP are represented as the single category, BitLocker.
Select a category and then the subcategories you’d like to include. Note that you can select subcategories independently or all at once by using the Select all these settings option. For the purposes of this demonstration, we’ll add them all in. Once you’re done making your category selections, use the X button to close the Settings picker pane and return to the Configurations tab.
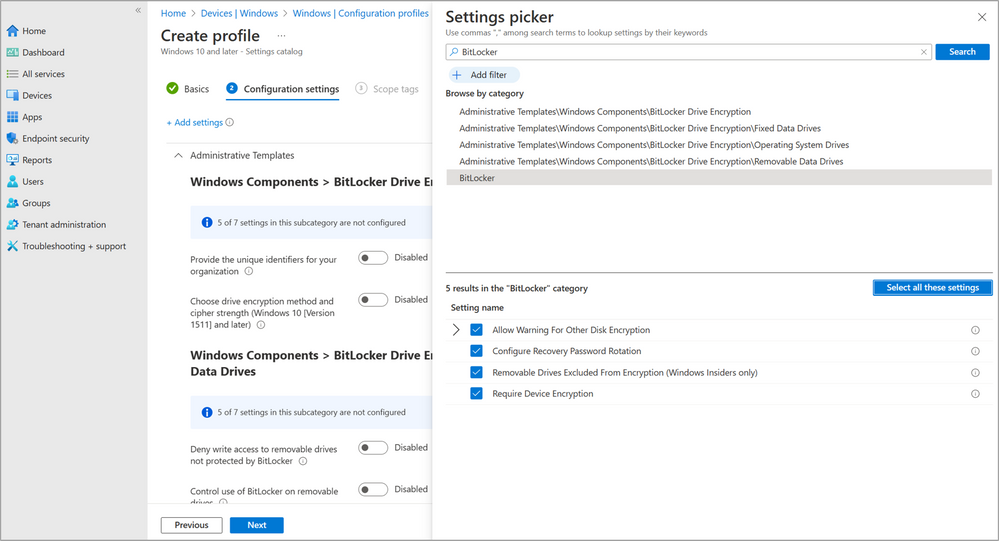
Expand the Administrative Templates category to see the setting options starting with the BitLocker Drive Encryption.
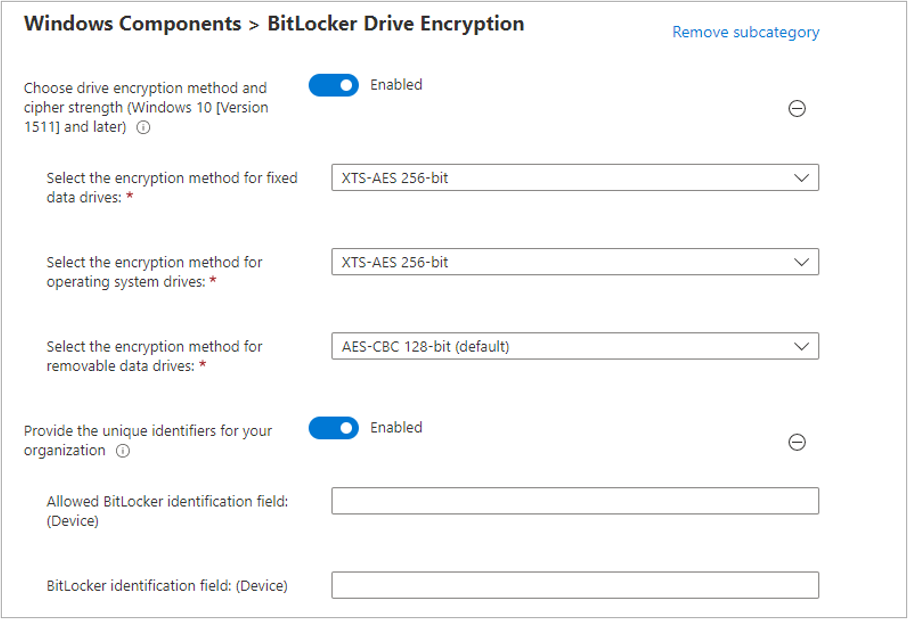
Here we can set the encryption method and cipher strength. In this instance, we’ve selected XTS-AES 256-bit for fixed data drives and operating system drives, and AES-CBC 128-bit (default) for removable data drives.
For illustrative purposes, we’ve enabled the unique identifiers but didn’t populated them. The unique identifiers are not available for configuration using BitLocker CSP, outside of the administrative templates.
Operating system drives
Once you’ve completed the BitLocker Drive Encryption configuration settings, you’ll move onto the Operating System Drives configuration options. These settings are largely the same as the endpoint security and device configuration profiles. However, there are additional settings not available in the other two policies, including:
- Allow devices compliant with InstantGo or HSTI to opt out of pre-boot PIN
- Allow enhanced PINs for startup
- Enable use of BitLocker authentication requiring preboot keyboard input on slates
- Enforce drive encryption type on operating system drives
- Select the encryption type: (Device)
A screenshot of the Operating System Drives pane and the available configuration options.
Most of these settings have been discussed in other posts in this blog series, including Configuring BitLocker encryption with Endpoint security and Using BitLocker recovery keys with Microsoft Intune. Note, configuring silent encryption (disabling user interaction when enabling BitLocker) is not compatible with configuring startup key and/or PIN. There is no option for the user to configure these settings.
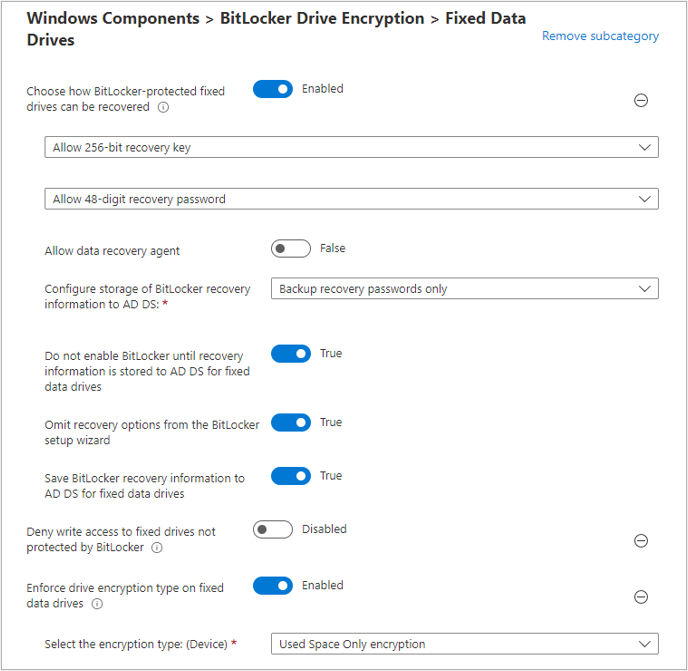
Fixed data drives
Configuring Fixed Data Drives settings are similar to those of endpoint security settings, with the exception of The Enforce drive encryption type on fixed data drives and the Select the encryption type (device). These settings allow the admin to specify whether BitLocker should encrypt used space only or the entire drive.
Removeable data drives
For removable drives, in addition to settings similar to endpoint protection policies, you’ll want to consider requirements for the Allow users to suspend and decrypt BitLocker protection on removable data drives (device) and Enforce drive encryption type on removable data drives settings as well.

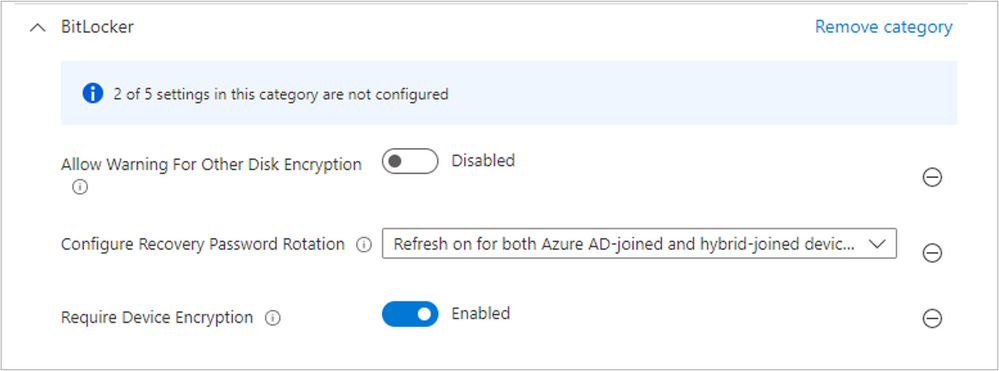
BitLocker settings
The BitLocker category enables silent encryption and recovery password rotation settings.
Silent encryption will enable BitLocker on a device without the user having to interact. The important limitation for this configuration is, since the user doesn’t have to interact, they won’t be prompted for a startup PIN.
To learn more about recovery keys and rotation, see Using BitLocker recovery keys with Microsoft Intune.
The settings catalog allows you the flexibility to choose which BitLocker settings are added to the policy. So, for example, it’s possible to add only the operating system and fixed drive categories and leave out the removable drive category.
There are also additional settings not available for configuration in the endpoint security and device configuration profiles that can be useful for scenarios where an admin wants to replicate the on-premises GPO settings via an Intune policy and has a requirement to set a startup PIN but doesn’t need to configure BitLocker via silent encryption. Additionally, being able to specify used space or full drive encryption may be advantageous for specific security requirements.
Check out the other blogs in our BitLocker series to learn more.
Let us know if you have any additional questions by replying to this post or reaching out to @IntuneSuppTeam on Twitter.
