This post has been republished via RSS; it originally appeared at: Intune Customer Success articles.
By: Michael Dineen - Sr Product Manager | Microsoft Intune
We wanted to provide a comprehensive guide for Microsoft Intune admins on the options available to block and remove specific, non-approved applications on both corporate-owned and personally owned (BYOD) iOS/iPadOS and Android devices. While the examples used in this article will be focused on the Microsoft OneDrive app, you can apply these steps to any app available in either the Apple App Store or Google Play Store.
iOS/iPadOS
This section covers corporate-owned and personally owned (BYOD) iOS/iPadOS devices.
Corporate devices (Supervised)
iOS and iPadOS devices that have been enrolled into Intune using Apple Business Manager via their Automated Device Enrollment (ADE) method are Supervised devices. To make use of specific device management APIs required for the example outlined below, the device is required to be Supervised.
Intune gives admins the ability to block access to the Apple App Store on corporate-owned supervised devices. If your organization has enabled this policy, any user of the device will be unable to access and install any unmanaged applications other than those made available by the Intune admin through the Intune Company Portal app.
If the admin blocks access to the Apple App Store, no additional configuration or action is required. If your organization has not blocked access to the Apple App Store on corporate-owned iOS/iPadOS devices, then users will be able to sign in with a personal Apple ID and download any app available in the Store. The following sections cover how Intune admins can discover, hide, and block the launch of restricted apps on corporate-owned supervised iOS/iPadOS devices.
Reporting – Discovered apps
Admins can determine which apps are installed on supervised iOS/iPadOS devices by navigating to the Discovered apps report in the Microsoft Intune admin center (Apps > Monitor > Discovered apps). This data is refreshed every seven days for supervised devices, starting from the date that the device was enrolled. For additional details on the discovery cycle, see Intune discovered apps.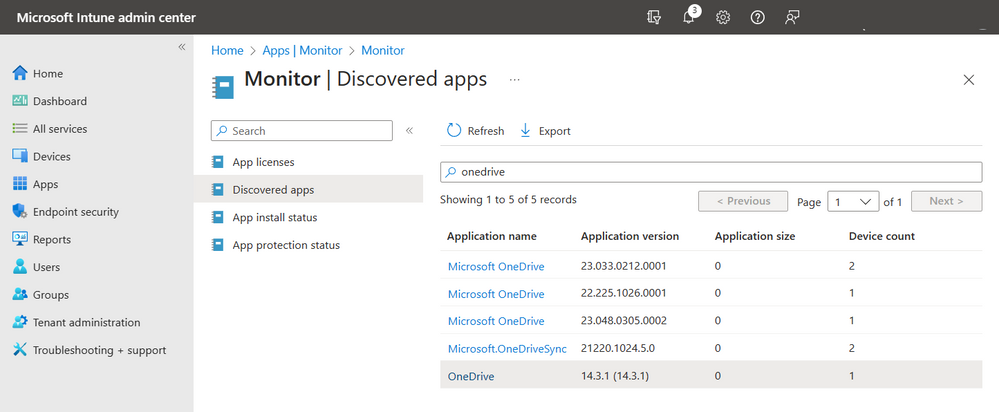
Admins can then click on a discovered app to see which devices have the app installed.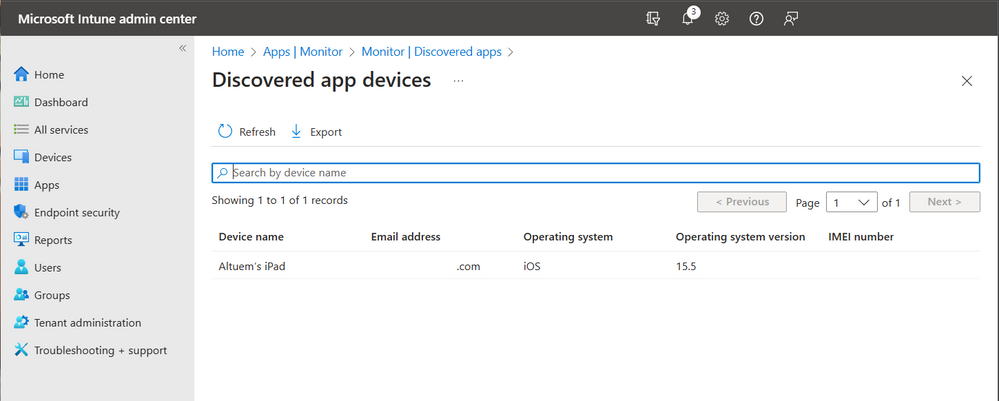
Reporting – Restricted Apps
Intune provides a report (Devices > Monitor > Devices with restricted apps) that displays devices that have installed restricted apps.
Specify restricted apps by navigating to Devices > iOS/iPadOS > Configuration Profiles > Create profile, select Templates for the Profile type and choose Device restrictions from the list. On the Configuration settings tab, expand the Restricted Apps option and change the Type of restricted apps list to Prohibited Apps. Then add the App store URL, App bundle ID, App name, and Publisher.
Note, this profile must be assigned to a user group.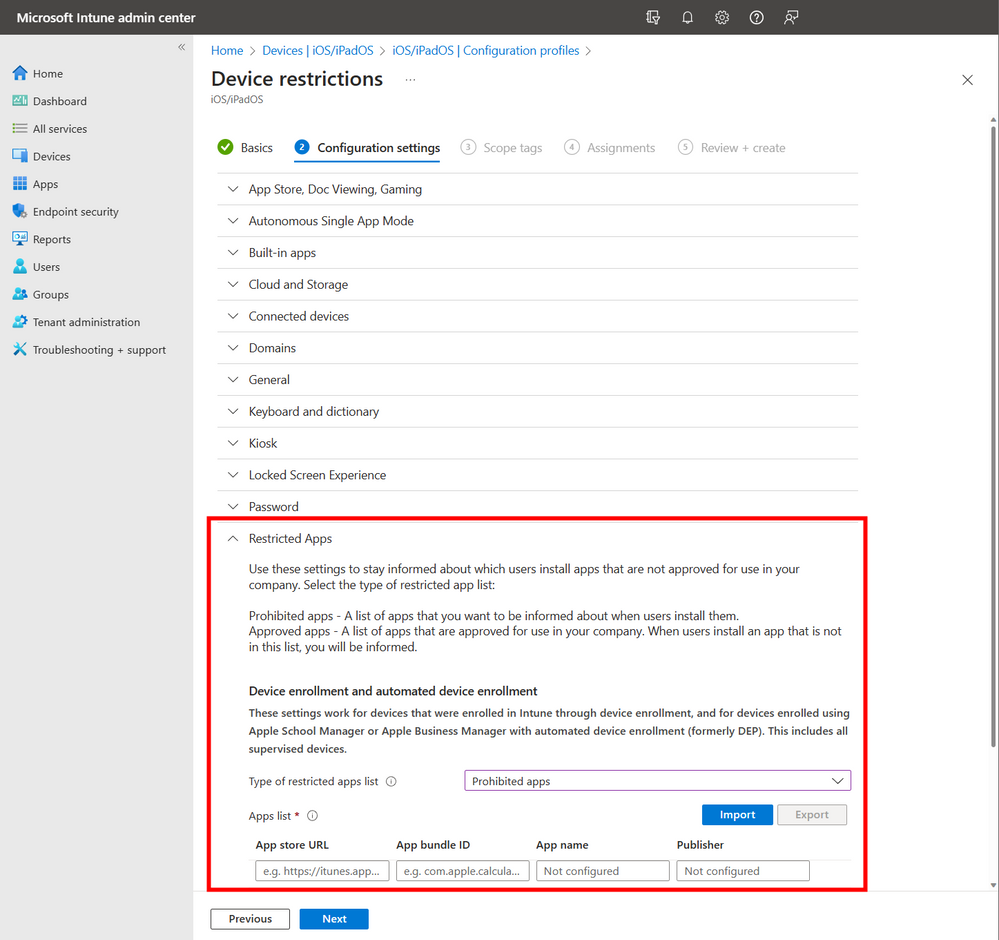
Devices with the restricted app installed will be displayed under the Devices with restricted apps report (Devices > Monitor > Devices with restricted apps).
Hide and prevent the launch of an app
Admins can both hide and prevent the launch of specific apps by using the settings catalog. To hide and prevent the launch of specific apps:
- Create a new device configuration profile and select Settings Catalog for the profile type. (Devices > iOS/iPadOS > Configuration profiles).
- On the Configuration settings tab, select Add settings and search for “Blocked App Bundle IDs.” Select the Restrictions category and then click the checkbox next to the Blocked App Bundle IDs setting. Close the Setting picker window and then enter the specific app bundle ID to be blocked.
A screenshot of the Settings picker showing the Restrictions category and the Blocked App Bundle IDs setting selection.
A screenshot of the Restrictions category Blocked App Bundle IDs option.
- Assign the policy to either a device or user group.
Uninstall apps
Apps that a user has installed on a supervised iOS or iPadOS device via the Apple App Store can be easily uninstalled via Intune.
- Navigate to Apps > iOS/iPadOS apps.
- Add the app to be uninstalled as an iOS store app by selecting + Add and choosing the iOS store app from the list.
A screenshot of the Select app type window with the iOS store app highlighted.
- Search for the app to be uninstalled and click Select. In this example, we want to uninstall Microsoft OneDrive.
A screenshot of the list of applications available when searching the App Store with the Microsoft OneDrive app highlighted.
- Accept the default settings and click Next.
- Modify the Scope tags, as needed.
- On the Assignments tab, under the Uninstall section, select + Add group or select +Add all users or + Add all devices, depending on your organization’s needs.
A screenshot of the Add App screen with the Uninstall settings highlighted.
- Click the Create button on the Review + create tab to complete the setup.
Monitor the status of the uninstall by navigating to Apps > iOS/iPadOS, selecting the app, and then selecting Device install status or User install status. The status will change to Not installed.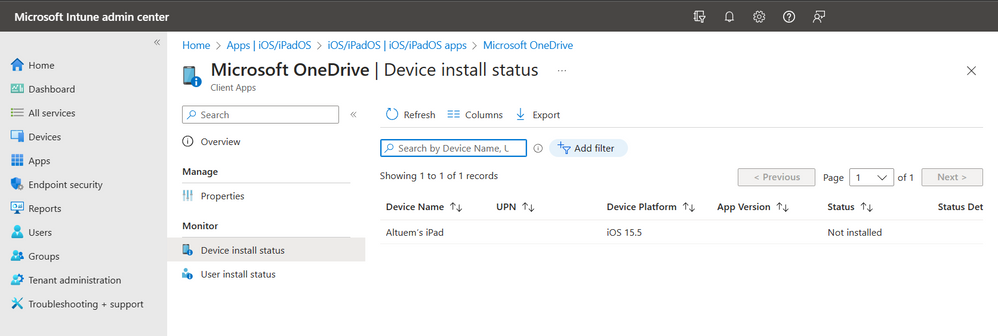
Bring Your Own Device (BYOD)
Bring your own device (BYOD) iOS and iPadOS devices are personally owned devices that have been voluntarily enrolled into Intune and can access organizational email, apps, and other data. Note that unlike supervised devices, not all administrative actions or configuration options are available to BYOD devices, such as the ability to geolocate the device or view apps installed by the user.
Identify BYOD devices that have restricted apps installed and prevent access to corporate resources
Compliance policies can be used to determine if a device can access corporate resources protected by Conditional Access (by being accessed as either compliant or non-compliant, see Grant controls in Conditional Access policy - Microsoft Entra | Microsoft Learn), based on a number of properties, such as whether a particular app is installed.
In our example, we’re assessing if a device has OneDrive installed and, if it does, the device should be marked as non-compliant.
- Create an iOS/iPadOS compliance policy, by navigating to Devices > iOS/iPadOS > Compliance policies > Create policy.
- On the Compliance settings tab, under System Security > Restricted apps, enter the name and app bundle ID of the restricted app and select Next. For this example, the App bundle ID for OneDrive is: com.microsoft.skydrive.
A screenshot of the System Security settings with Device Security highlighted.
- Under Actions for noncompliance, leave the default action Mark device noncompliant configured to Immediately and then select Next.
- Assign any Scope tags as required and select Next.
- Assign the policy to a user or device group and select Next.
- Review the policy and click Create.
Devices that have the restricted app installed will be shown in the Monitor section of the compliance policy.
- Navigate to the compliance policy and select Device status, under Monitor.
A screenshot of the Monitor Device status screen for a Prohibited App.
- Devices that have the restricted app installed will be shown in the report.
A screenshot of the Device status report for a Prohibited App.
Manage the app in Intune
Now that devices with the restricted app installed have been identified, you’ll need to add the app in Intune to be managed before you can take action and uninstall the app (also known as app takeover: Distribute Managed Apps to Apple devices – Apple Support).
To manage an app that a user has installed, perform the following steps:
- Create a group that contains all identified devices with the restricted app installed.
- Add the restricted app as an iOS Store app (if already created, edit the existing application).
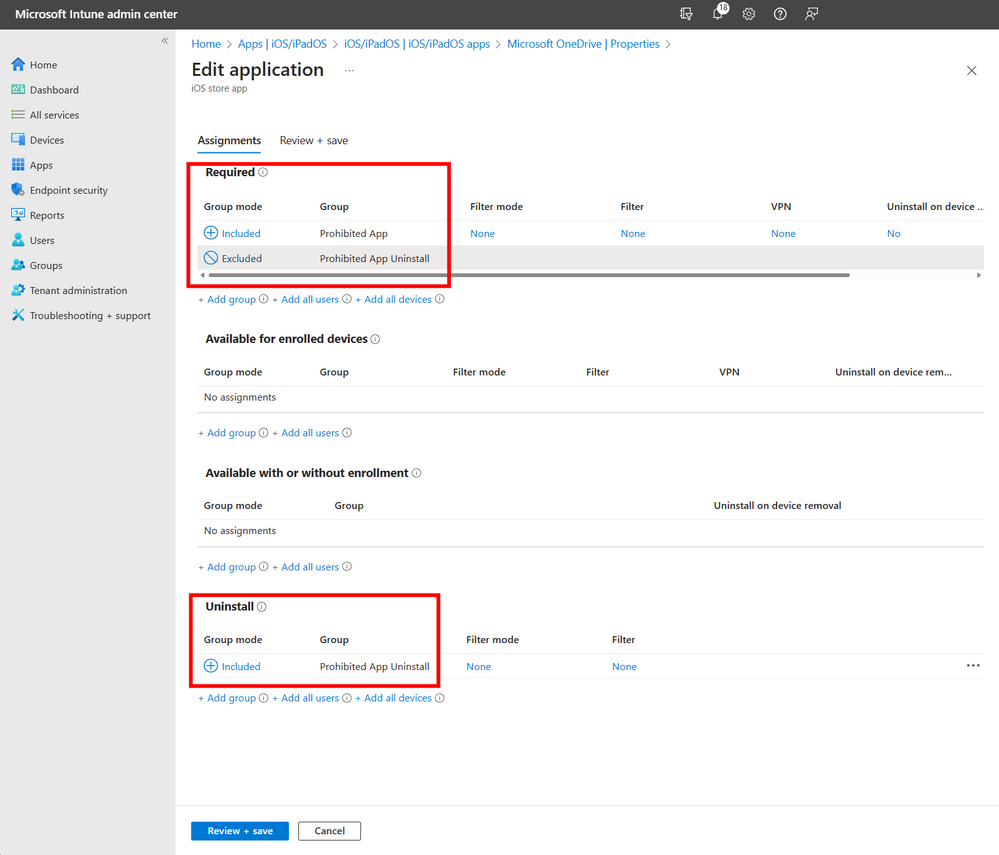
- Then, add the group containing all identified devices with the restricted app installed as Required under Assignments.
A screenshot of the Edit application screen with the Required settings highlighted.
- Click Review and save.
On the BYOD device, the user will receive the App Management Change prompt and will have the choice to allow the organization to manage the app.
If the user selects Cancel, then the app will not become managed. The compliance policy will still determine that the device is non-compliant, and the user won’t be able to access corporate resources granted by Conditional Access, where corporate resources targeted with a Conditional Access policy require the device to be compliant before granting access to the resource.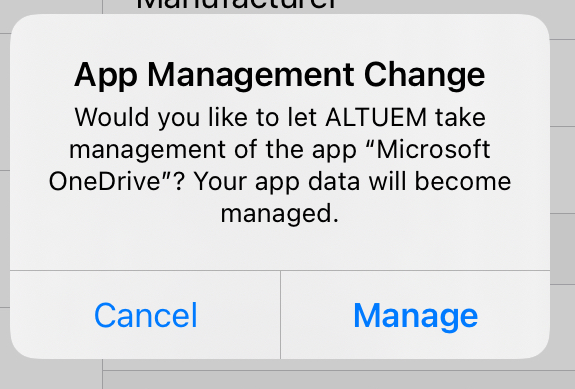
If the user selects Manage, then the app becomes managed, and the organization will have the ability to uninstall the app. The app will also be displayed under Managed Apps on the device object.
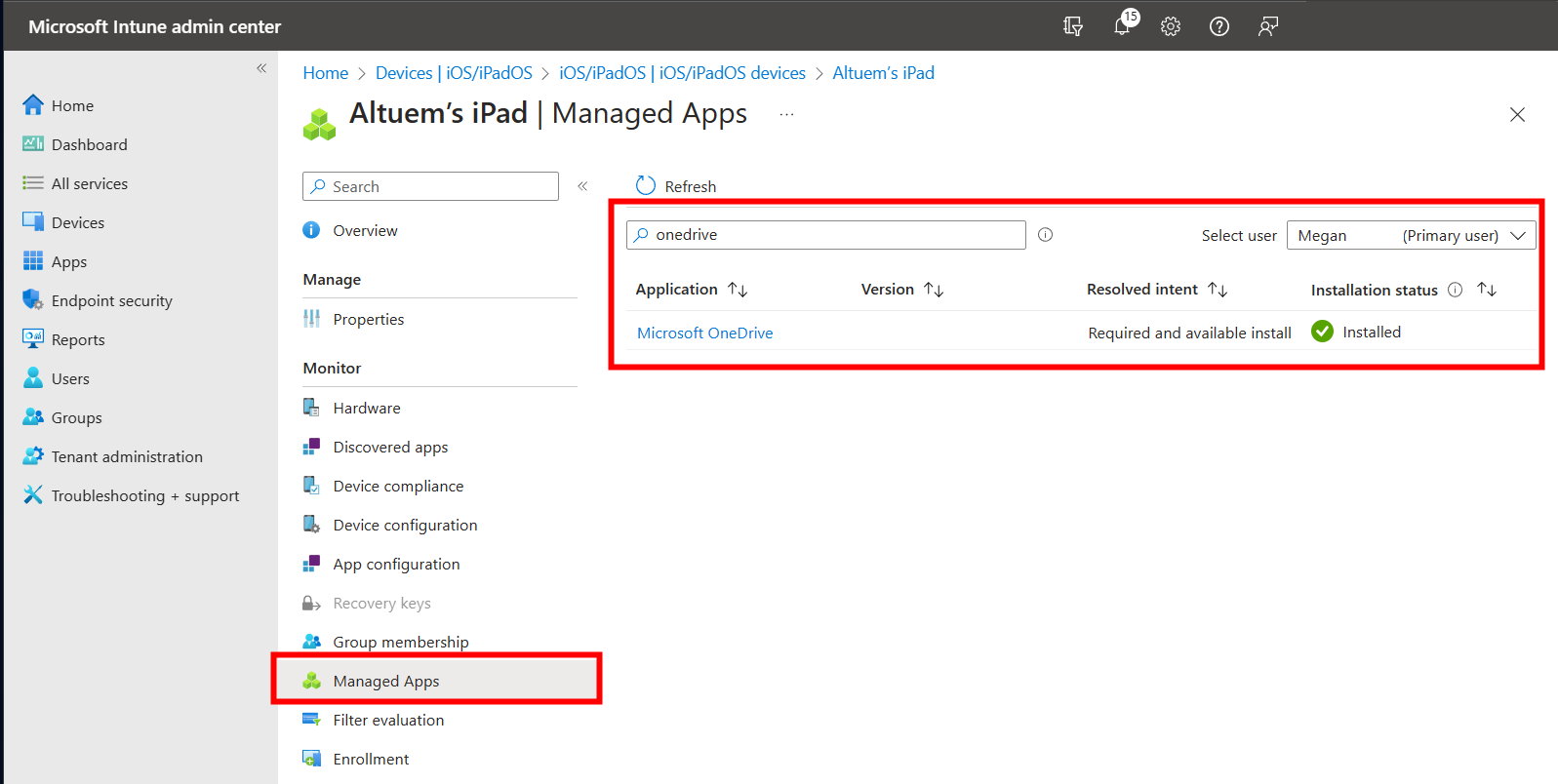
Once the app is managed, it may be uninstalled by performing the following steps:
- Create a new group that contains the device with the restricted app.
- Navigate to the prohibited app > Properties > Assignments > Edit.
- Add the new group created in step 1 under Uninstall and ensure that the group mode shows Included.
- Add the new group created in step 1 under Required and ensure that the group mode shows Excluded.
Android
This section covers how to restrict and remove apps on Android devices based on the enrollment method.
Android Enterprise corporate owned fully managed devices
Devices enrolled using Android Enterprise corporate owned fully managed will only have access to the Managed Google Play Store. This is a curated store, where users are able to install approved apps published to them by their organization.
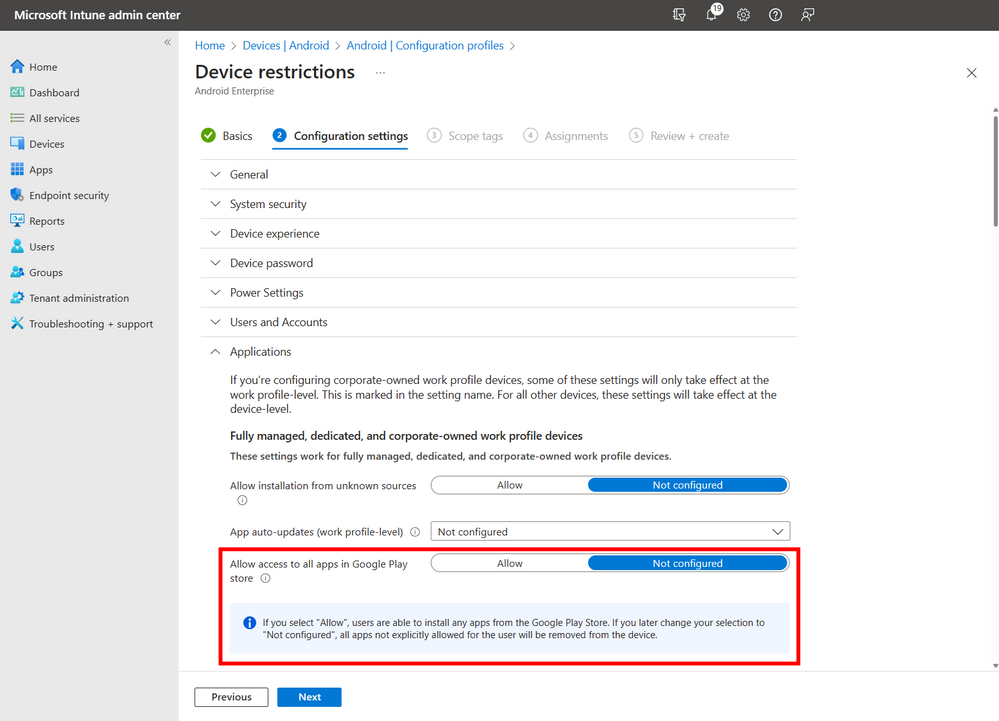
Organizations can enable access to the Google Play Store via the setting Allow access to all apps in Google Play store, available in the configuration settings of a device restriction policy. This setting is set to Not configured by default and prevents users from accessing the Google Play Store and installing restricted apps. If you configured the setting to Allow, and a restricted app has been installed, there are two options that the admin can take to remove the app.
1. Revoke access to all apps in Google Play Store
The admin can configure the setting to Allow access to all apps in Google Play Store to the default setting, Not configured. When changed from Allow to Not configured, all apps not explicitly allowed for the user will be removed from the device. The user will receive a notification indicating the app has been deleted.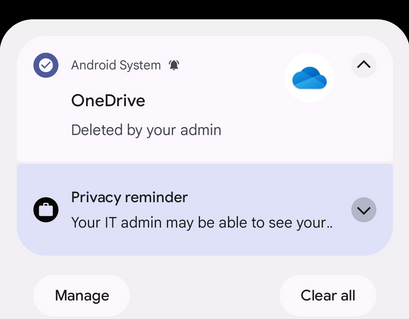
2. Uninstall the restricted app
To uninstall a restricted app, and prevent it from being installed via the Google Play Store, perform the following steps:
- Add a Managed Google Play app in the Intune admin center by navigating to Apps > Android > Add, then select Managed Google Play app from the drop-down list and click Select.
A screenshot of the Select app type window on the Android apps page in the Intune admin center.
- Enter the name of the app to be uninstalled in the Search bar, select it, and then click Approve. For this example, we’re uninstalling Microsoft OneDrive.
A screenshot of the selected Microsoft OneDrive application with the Approve button highlighted.
- A popup window will appear asking to approve the information the application has access to. Select Approve to proceed and then Approve for the new permissions.
- Verify that the app has been approved and click Sync button to continue.
A screenshot of the Approved application with the sync icon highlighted.
- Navigate to Apps > All apps and select the newly approved application. Select Properties > Edit Assignments and then add a group under the Uninstall section. In this example, we are uninstalling the app from All Users.
A screenshot of the Edit application screen with the Uninstall section highlighted and the Group, All users, included.
- Select Review and save.
- After the next sync, the app will be uninstalled and the user will receive a prompt that the app has been deleted by their admin.
A screenshot of the notification the device user sees when an application has been uninstalled by the administrator.
- If the user navigates to the Google Play Store, they will be unable to install the restricted app with a notification that says, “Your administrator has not given you access to this item.”
A screenshot of the warning notification on an Android device when the user attempts to access a restricted app.
Corporate owned device with work profile
Devices enrolled using Android Enterprise corporate-owned work profile provides the device owner with a separate work profile that allows them to install apps for personal use, over which the organization has limited control and visibility. With this enrollment method, the work profile is often referred to as the “personal profile”.
To restrict specific apps from being installed in the work profile, do the following steps:
- Create a new Device restriction profile by navigating to Devices > Android > Configuration profiles, select Create Profile and choose Android Enterprise as the platform. For the Profile type, select “Device restrictions” under Fully Managed, Dedicated, and Corporate-Owned Work Profile.
- Under Personal profile, for the setting Type of restricted apps list, select Blocked apps and then Add.
- Select the app to be restricted. Note that the app must be already added as a Managed Google Play app, see Add a Managed Google Play store app directly in the Microsoft Intune admin center. In this example, we're restricting the installation of OneDrive.
A screenshot of the Type of restricted apps list setting under Device restrictions in the device configuration profile.
- Assign the policy to a specific group, all users, or all devices.
- The user will receive a notification on their device that a “Personal app removed. Your IT admin no longer allows <AppName> in your personal profile.”
A screenshot of the notification “Personal app removed. Your IT admin no longer allows <AppName> in your personal profile,” on the user’s Android device.
- If the user navigates to the Google Play Store, they’ll be unable to install the restricted app.
A screenshot of the warning notification on an Android device when the user attempts to access a restricted app.
Android Enterprise personally owned devices with work profile
For Android Enterprise personally owned devices with a work profile, use the same settings as described earlier in the Android Enterprise corporate owned, fully managed devices section to uninstall and prevent the installation of restricted apps in the work profile.
Apps installed outside of the work profile can’t be managed.
Using Intune MAM only
Intune mobile application management (MAM), comprised of app protection policies (APP) and app configuration policies (ACP), allows organizations to manage and protect corporate data within an application, without the need to have the device enrolled into an mobile device management (MDM) solution. This applies to both iOS/iPadOS and Android devices. When used on unenrolled devices, MAM has no visibility of the device configuration or other installed unmanaged apps.
For recommended configurations to keep your organization's data secure, see Data protection framework using app protection policies - Microsoft Intune | Microsoft Learn. Additional guidance is available for Android devices in Mobile Application Management (MAM) and Android Enterprise personally-owned work profiles in Microsoft Intune | Microsoft Learn.
Conclusion
In summary, we’ve discussed a variety of different approaches Intune admins can use to discover, hide, and prevent the launch of non-approved mobile applications, including how to remove specific apps on both iOS/iPadOS and Android devices.
We also discussed the use of compliance policies to mark devices that have non-approved mobile apps installed as non-compliant. When used in combination with Azure Active Directory Conditional Access, those non-compliant devices won’t be granted access to corporate resources. This is especially relevant for enrolled iOS/iPadOS BYOD scenarios.
Regardless of the platform or enrollment method, we recommend utilizing MAM to protect corporate data across both corporate and personal devices.
If you have any questions, please let us know in the comments or reach out to us on Twitter @IntuneSuppTeam.