This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Spear phishing campaign is a type of attack where phishing emails are tailored to specific organization, organization’s department, or even specific person. Spear phishing is a targeted attack by its definition and rely on preliminary reconnaissance, so attackers are ready to spend more time and resources to achieve their targets. In this blog post, we will discuss steps that can be taken to respond to such a malicious mailing campaign using Microsoft 365 Defender.
What makes phishing “spear”
Some of the attributes of such attacks are:
- Using local language for subject, body, and sender’s name to make it harder for users to identify email as phishing.
- Email topics correspond to the recipient’s responsibilities in the organization, e.g., sending invoices and expense reports to the finance department.
- Using real compromised mail accounts for sending phishing emails to successfully pass email domain authentication (SPF, DKIM, DMARC).
- Using large number of distributed mail addresses to avoid bulk mail detections.
- Using various methods to make it difficult for automated scanners to reach malicious content, such as encrypted ZIP-archives or using CAPTCHA on phishing websites.
- Using polymorphic malware with varying attachment names to complicate detection and blocking.
In addition to reasons listed above, misconfigured mail filtering or transport rules can also lead to the situation where malicious emails are hitting user’s inboxes and some of them can eventually be executed.
Understand the scope of attack
After receiving first user reports or endpoint alerts, we need to understand the scope of attack to provide adequate response. To better understand the scope, we need to try to answer the following questions:
- How many users are affected? Is there anything common between those users?
- Is there anything shared across already identified malicious emails, e.g. mail subject, sender address, attachment names, sender domain, sender mail server IP address?
- Are there similar emails delivered to other users within the same timeframe?
Basic hunting will need to be done at this point, starting with information we have on reported malicious email, luckily Microsoft 365 Defender provides extensive tools to do that. For those who prefer interactive UI, Threat Explorer is an ideal place to start.
Figure 1: Threat Explorer user interface
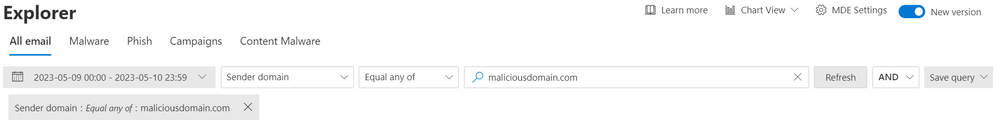
Using filter at the top, identify reported email and try to locate similar emails sent to your organization, with the same parameters, such as links, sender addresses/domains or attachments.
Figure 2: Sample mail filter query in Threat Explorer
For even more flexibility, Advanced Hunting feature can be used to search for similar emails in the environment. There are five tables in Advanced Hunting schema that contain Email-related data:
- EmailEvents – contains general information about events involving the processing of emails.
- EmailAttachmentInfo - contains information about email attachments.
- EmailUrlInfo - contains information about URLs on emails and attachments.
- EmailPostDeliveryEvents - contains information about post-delivery actions taken on email messages.
- UrlClickEvents - contains information about Safe Links clicks from email messages
For our purposes we will be interested in the first three tables and can start with simple queries such as the one below:
EmailAttachmentInfo
| where Timestamp > ago(4h)
| where FileType == "zip"
| where SenderFromAddress has_any (".br", ".ru", ".jp")
This sample query will show all emails with ZIP attachments received from the same list of TLDs as identified malicious email and associated with countries where your organization is not operating. In a similar way we can hunt for any other attributes associated with malicious emails.
Check mail delivery and mail filtering settings
Once we have some understanding of how attack looks like, we need to ensure that the reason for these emails being delivered to user inboxes is not misconfiguration in mail filtering settings.
Check custom delivery rules
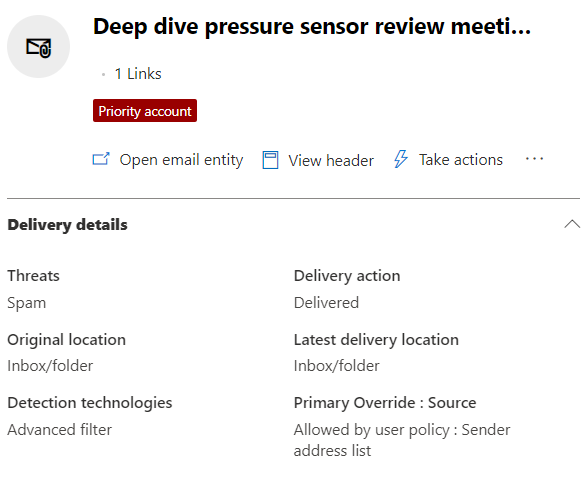
For every mail delivered to your organization, Defender for Office 365 provides delivery details, including raw message headers. Right from the previous section, whether you used Threat Explorer or Advanced Hunting, by selecting an email item and clicking Open email entity button, you can pivot to email entity page to view all the message delivery details, including any potential delivery overrides, such as safe lists or Exchange transport rules.
Figure 3: Sample email with delivery override by user's safe senders list
It might be the case that email was properly detected as suspicious but was still delivered to mailbox due to an override, like on screenshot above where sender is on user’s Safe Senders list, other delivery override types are:
- Allow entries for domains and email addresses (including spoofed senders) in the Tenant Allow/Block List.
- Mail flow rules (also known as transport rules).
- Outlook Safe Senders (the Safe Senders list that's stored in each mailbox that affects only that mailbox).
- IP Allow List (connection filtering)
- Allowed sender lists or allowed domain lists (anti-spam policies)
If a delivery override has been identified, then it should be removed accordingly. Good news is that malware or high confidence phishing are always quarantined, regardless of the safe sender list option in use.
Check phishing mail header for on-prem environment
One more reason for malicious emails to be delivered to users’ inboxes can be found in hybrid Exchange deployments, where on-premises Exchange environment is not configured to handle phishing mail header appended by Exchange Online Protection.
Check threat policies settings
If there were no specific overrides identified it is always a good idea to double check mail filtering settings in your tenant, the easiest way to do that, is to use configuration analyzer that can be found in Email & Collaboration > Policies & Rules > Threat policies > Configuration analyzer:
Figure 4: Defender for Office 365 Configuration analyzer
Configuration analyzer will quickly help to identify any existing misconfigurations compared to recommended security baselines.
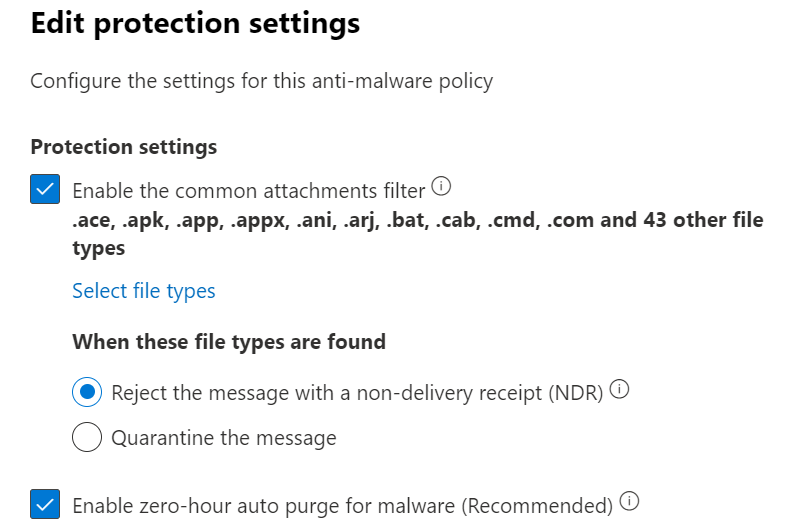
Make sure that Zero-hour auto purge is enabled
In Exchange Online mailboxes and in Microsoft Teams, zero-hour auto purge (ZAP) is a protection feature that retroactively detects and neutralizes malicious phishing, spam, or malware messages that have already been delivered to Exchange Online mailboxes or over Teams chat. Which exactly fits into the discussed scenario. This setting for email with malware can be found in Email & Collaboration > Policies & rules > Threat policies > Anti-malware. Similar setting for spam and phishing messages is located under Anti-spam policies.
Figure 5: Zero-hour auto purge configuration setting in Anti-malware policy
NOTE: Please be aware that ZAP doesn't work for on-premises Exchange mailboxes.
Performing response steps
Once we have identified malicious emails and confirmed that all the mail filtering settings are in order, but emails are still coming through to users’ inboxes (see the introduction part of this article for reasons for such behavior), it is time for manual response steps:
Report false negatives to Microsoft
In Email & Collaboration > Explorer, actions can be performed on emails, including reporting emails to Microsoft for analysis:
Figure 6: Submit file to Microsoft for analysis using Threat Explorer
Actions can be performed on emails in bulk and during the submission process, corresponding sender addresses can also be added to Blocked senders list.
Alternatively, emails, specific URLs or attached files can be manually submitted through Actions & Submissions > Submissions section of the portal. Files can also be submitted using public website.
Figure 7: Submit file to Microsoft for analysis using Actions & submissions
Timely reporting is critical, the sooner researchers will get their hands on unique samples from your environment, and start their analysis, the sooner those malicious mails will be detected and blocked automatically.
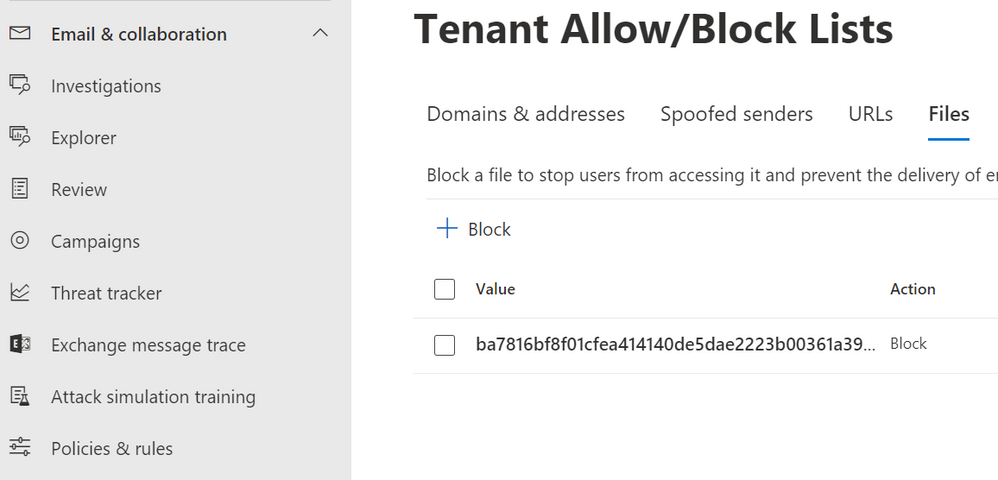
Block malicious senders/files/URLs on your Exchange Online tenant
While you have an option to block senders, files and URLs during submission process, that can also be done without submitting using Email & Collaboration > Policies & rules > Threat policies > Tenant Allow/Block List, that UI also supports bulk operations and provides more flexibility.
Figure 8: Tenant Allow/Block Lists
The best way to obtain data for block lists is Advanced Hunting query, e.g. the following query can be used to return list of hashes:
EmailAttachmentInfo
| where Timestamp > ago(8h)
| where FileType == "zip"
| where FileName contains "invoice"
| distinct SHA256, FileName
NOTE: such a simple query might be too broad and include some legitimate attachments, make sure to adjust it further to get an accurate list and avoid false positive blockings.
Block malicious files/URLs/IP addresses on endpoints
Following defense-in-depth principle, even when malicious email slips through mail filters, we still have a good chance of detecting and blocking it on endpoints using Microsoft Defender for Endpoint. As an extra step, identified malicious attachments and URLs can be added as custom indicators to ensure their blocking on endpoints.
EmailUrlInfo
| where Timestamp > ago(4h)
| where Url contains "malicious.example"
| distinct Url
Results can be exported from Advanced Hunting and later on imported on Settings > Endpoints > Indicators page (NOTE: Network Protection need to be enabled on devices to block URLs/IP addresses). The same can be done for malicious files using SHA256 hashes of attachments from EmailAttachmentInfo table.
Some other steps that can be taken in advanced in order to better prepare your organization for similar incident:
- Ensure that EDR Block Mode is enabled for machines where AV might be running in passive mode.
- Enable Attack Surface Reduction (ASR) rules to mitigate some of the risks associated with mail-based attacks on endpoints.
- Train your users to identify phishing mails with Attack simulation feature in Microsoft Defender for Office 365
Learn more
- Begin using Microsoft 365 Defender today.
- Read more about Microsoft Incident Response services.
- Use the 90-day Microsoft 365 Defender for Office 365 Plan 2 trial at the Microsoft 365 Defender portal trials hub. Learn about who can sign up and trial terms here.