This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
GitHub Advanced Security on Azure DevOps has industry leading capabilities: Secret Scanning Push Protection (intervene before commit history is created), Secret scanning, Dependency scanning, and CodeQL code scanning (SAST). These are natively integrated into Azure Repos and Azure Pipelines.
It helps to implement Shift Left Security, detect vulnerabilities in early stages of development, has lower rate of false positives which helps in reducing the remediation cost.
Secret Scanning Push Protection:
Exposed credentials are implicated in over 80% of security breaches.
Proactively protect against leaked secrets in your repositories. Resolve blocked pushes and, once the detected secret is removed, push changes to your working branch from the command line or web UI.
Secret scanning (FIND AND MANAGE HARD-CODED SECRETS)
Proactively identify secrets early: Find secrets (including Azure secrets) the moment they are pushed to Azure DevOps and immediately notifies developers when they are found.
Detect more than 200+ token types from more than 100+ partners: For every commit made to your repository and its full git history, it will look for secret formats from our secret scanning partners.
Code scanning (SAST) (Find and fix vulnerabilities as you code): Use CodeQL static analysis engine to detect hundreds of code security vulnerabilities such as SQL injection and authorization bypass across a wide range of languages including C#, C/C++, Python, JavaScript/TypeScript, Java, Go and more. GitHub Advanced Security for Azure DevOps enables you to run CodeQL scans directly from Azure Pipelines on code from Azure Repos and act on the results without ever having to leave your Azure DevOps environment.
CodeQL turns source code into relational data that can be queried for vulnerabilities.
CodeQL queries can be quickly customized to adapt to your specific threat topology.
CodeQL is open source, built for use by security researchers around the world.
Find and fix vulnerabilities fast Find and fix vulnerabilities before they are merged into the code base with automated scans.
Community of top security experts Your projects are powered by world-class security teams. Use queries created by the security community in your projects.
Integrated with developer workflow Integrate security results directly into the developer workflow for a frictionless experience and a faster development cycle.
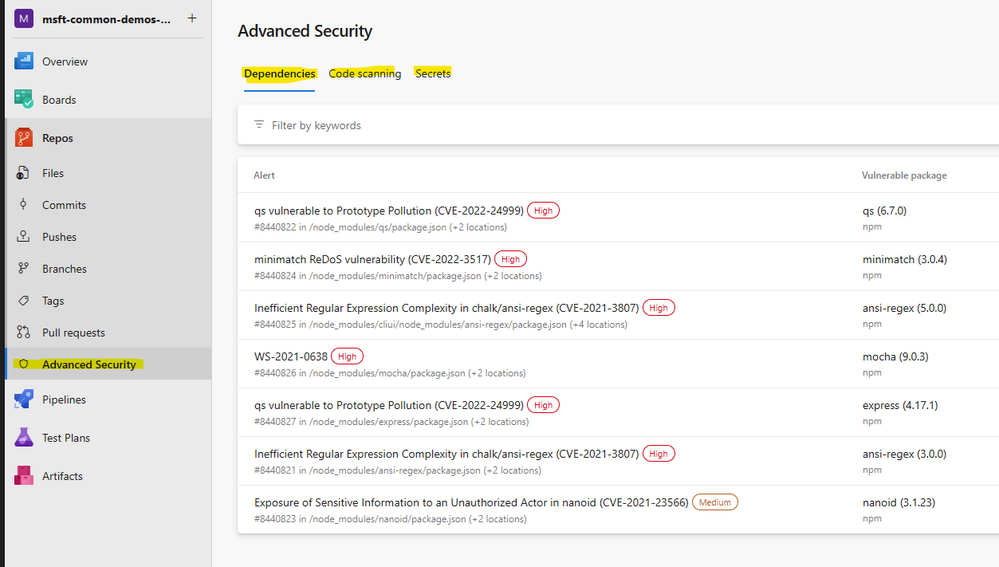
Dependency Scanning (Provide visibility into vulnerable and out-of-date dependencies) Open-source supply chain attacks such as the “Log4Shell” incident are on the rise. GitHub Advanced Security identifies the open-source packages used in your Azure Repos – both direct and transitive dependencies – and provides straightforward guidance from the GitHub Advisory Database on how to upgrade those packages to mitigate vulnerabilities.
Automated security alerts Keep your projects secure and up to date by monitoring them for vulnerable and out-of-date components. Integrated with developer workflow Dependency Scanning integrates directly into the developer workflow for a frictionless experience and faster fixes.
Rich vulnerability data GitHub tracks vulnerabilities in packages from supported package managers using data from security researchers, maintainers, and the National Vulnerability Database – all discoverable in the GitHub Advisory Database.