This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
This blog has been co-authored by Microsoft and Sharan Rayakar from Progress.
As development and operations teams build and support Windows applications running on Azure Kubernetes Service(AKS), they must ensure that they reduce risk and safeguard against potential cyber-security threats. Chef Cloud Security includes Kubernetes and Container Security support that provides developers and their DevSecOps teammates the security and visibility necessary to confidently run containers on AKS. This blog covers how AKS customers can use Chef Kubernetes and Container Security to protect their environments.
Chef Container and Kubernetes Security Overview
Chef Cloud Security, a Cloud Security Posture Management (CSPM) solution, provides visibility and threat detection from build to runtime that monitors, audits, and remediates the security of your clusters, containers, and applications. Chef Cloud Security assists with the following aspects of container and Kubernetes security:
- Configuration Assessment for Images: Customers can scan Windows container images and Azure Container Registry for known misconfigurations in operating system software packages as well as non-OS packages including application and database packages. Users can create custom policies for immutable and reproducible container images with Chef.
- Container Deployment Security: Users can validate Kubernetes (AKS) configuration to ensure that pods, network policies, network interfaces, and configuration files are appropriately set as part of the CI/CD pipeline process.
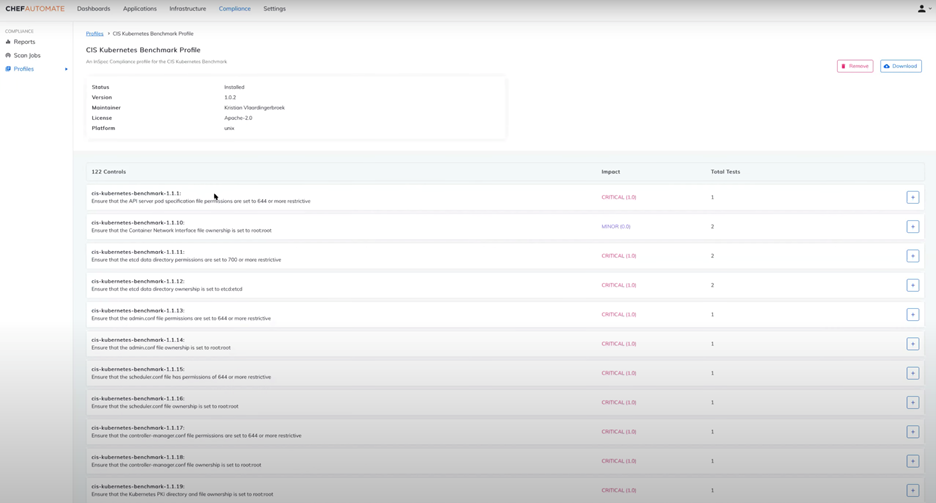
- Kubernetes Compliance - AKS can be integrated with Chef to monitor configuration compliance such as CIS Benchmarks of your cluster resources. Users can enable or disable policies to match compliance needs, and view reports detailing non-compliant resources and recommendations. Users can leverage additional benchmarks such as SOC2, PCI-DSS etc., to help further identify AKS security risks.
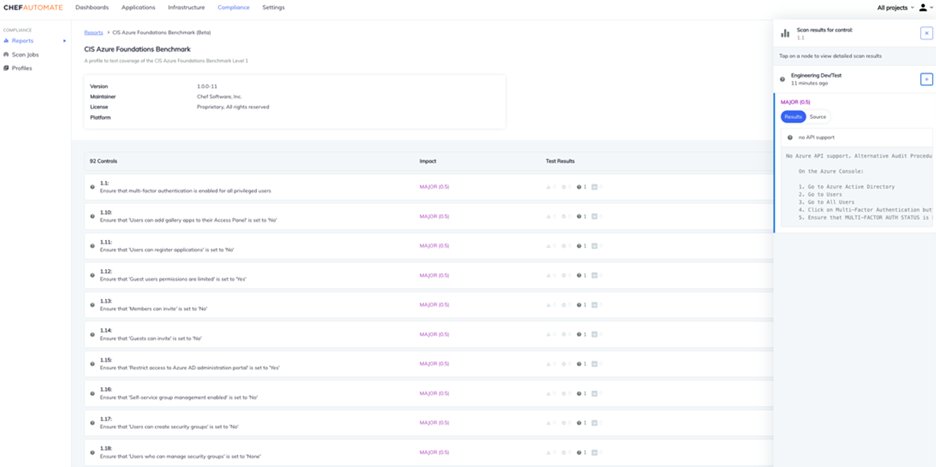
- Azure Cloud Security - Chef Cloud Security offers clients comprehensive visibility into their cloud security posture and helps limit the risk of misconfigurations in cloud-native environments by providing best practices based on CIS, STIG, and other benchmarks.
- Visibility – Through Chef Cloud Security, operations teams can maintain complete visibility over the compliance & security status for their container, Kubernetes and cloud environments. This automated security approach helps detect and correct security issues before they go into production, reducing risk, increasing speed, and improving efficiency.
Chef helps validate the security posture of your Azure Kubernetes Service and Windows containers by securing container images and their deployed environment, managing compliance and security of the deployment environment, and supporting cloud environments and services.
Chef + Windows on Azure Kubernetes Service
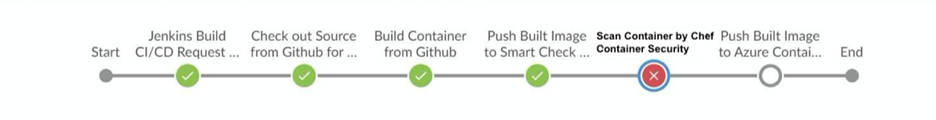
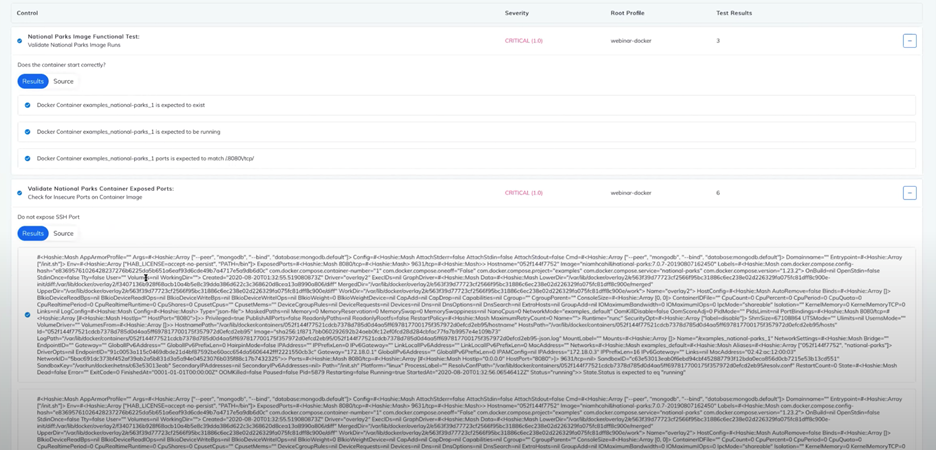
Chef ensures that Windows container images are correctly configured including OS, application and database packages, and checks the application is running correctly with the right ports, privileged mode setting, package version checks, etc. Chef enables you to integrate these checks with Azure Container Registry (ACR) as part of your CI/CD pipeline – ensuring your images are secure before they make it into your registry.
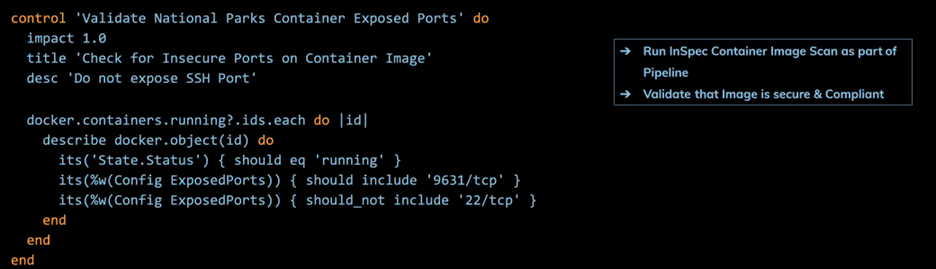
For e.g., this code snippet checks for exposed ports while running a container image.
Chef ensures the AKS deployment configuration is secure by checking the following settings: Control plane components (pods, network interfaces, configuration files), API server (arguments setting), controller manager, scheduler, logging, worker nodes (Kubelet setting, configuration files, policies, pod security policies, network policies and CNI. Chef resources can be used to write custom policies to perform checks on underlying systems such as looking for a specific pod or a specific Kubelet. This saves time required to create and perform the checks across the entire system.
Chef® Cloud Security™ makes it possible for you to scan, monitor, and remediate configuration issues in your multi-cloud accounts. It is easier than ever to maintain and enforce compliance with a standards-based audit. You can tune baselines to adapt to your organization’s requirements, and maintain visibility and control across hybrid environments. These best practices ensure appropriate AKS network policies are set to limit network traffic, identify and block malicious traffic to your web application through Azure Application Gateway settings, and provides an audit trail for the Kubernetes control plane by enabling audit logs for kube-apiserver and kube-controller-manager, etc. Chef resources can be used to write new policy rules that perform checks on the individual security settings of underlying systems and merges them with existing policies.
Chef provides packaged policy bundles in the form of Premium Content for compliance scanning and remediation based on Center for Internet Security (CIS)) certified benchmarks or Defense Information Systems Agency (DISA) Security Technical Implementation Guides (STIGs) across a range of enterprise assets – container hosting environments (Docker/K8s), container packages (operating systems, applications, databases), cloud environments (Azure and other clouds). Chef also provides cloud best practices and industry-specific compliance standards (SOC2, GDPR, PCI etc.) to make products easy to use. The list of supported policy bundles is located here: https://www.chef.io/products/chef-premium-content.
Chef is leading the evolution from “Infrastructure as Code” to “Policy as Code” which merges infrastructure, security, and compliance concerns into a single framework to enable collaboration across different teams. GigaOm has acknowledged Progress Chef as a Leader in the Policy as Code market within the DevSecOps sector.
Chef provides 500+ built-in resources that map to individual security settings - MFA setting / port setting, etc. of the underlying systems. New policies can be created using these resource settings using an as code approach.
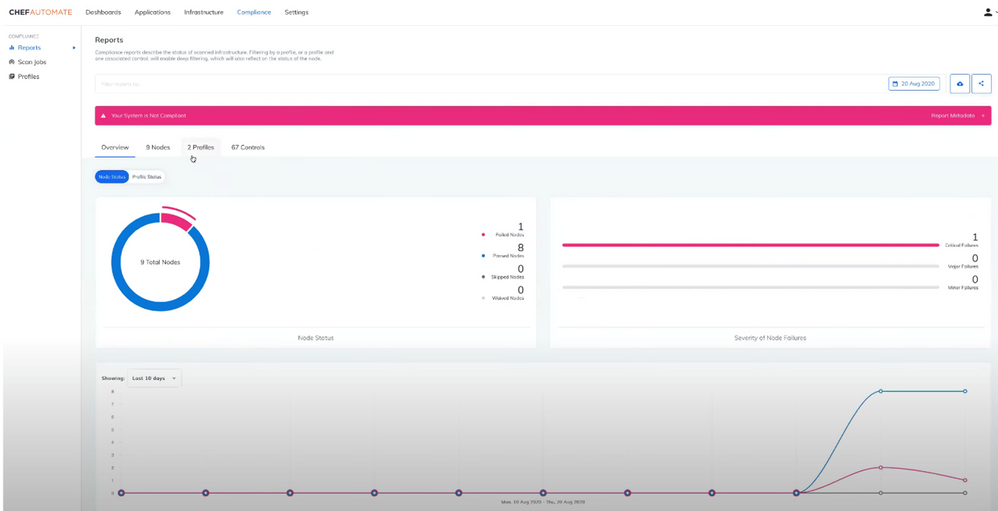
The compliance and security scan data can be visualized using Chef’s Automate dashboard with detailed and easy-to-read reports that include descriptions and results of all security controls as well as the code that was executed on the backend.
Historical trends provide insights into how the posture has changed over time and security event data can be exported into external third-party tools via APIs such as ServiceNow, Splunk, Kibana, etc.
Historical trends provide insights into how the posture has changed over time and security event data can be exported into external third-party tools via APIs such as ServiceNow, Splunk, Kibana, etc.
Conclusion
Chef’s approach towards Windows containers on AKS provides an end-to-end review of the cloud environment. It scans container images for OS and related package misconfigurations by integrating into existing CI/CD pipelines before pushing into the Azure Container registry. Functional tests are also performed ensuring the application is running correctly on the right ports, versions, etc. Chef also ensures that the Kubernetes environment is compliant and secure using packaged Chef Premium Content to start quickly and by allowing custom policy checks through Chef resources. With Chef’s Policy as Code approach, it is possible to codify all the checks within your code and CI/CD pipeline. This helps DevOps teams collaborate through code, shift security left, verify and validate deployments in real time and speeds remediation efforts. Chef Automate provides dashboards that can be used to view results and determine the security posture of your multi-cloud environments.
To learn more about how Chef secures your Windows Containers on AKS environment visit the following links: