This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
The Rise of the Registry
As the use of container technology continues to grow, it has become increasingly important to understand the risks and potential vulnerabilities that come along with it. One of the key components of any container ecosystem is the container registry, which is responsible for storing and distributing container images. One popular registry provider is Microsoft Azure, which offers the Azure Container Registry Images.
Securing container images is essential to ensure data protection, reduce the risk of data breaches, and improve regulatory compliance. By understanding potential vulnerabilities, businesses can create a robust security strategy to protect their containerized applications, thereby safeguarding their sensitive data, reputation, and customer trust.
What is the Azure Container Registry?
Azure Container Registry provides a secure and scalable way to store and manage container images within the Azure ecosystem. The registry allows users to upload and store container images, as well as manage access control and automate image builds. This is especially useful for developers who need to quickly and easily deploy applications within the Azure platform.
Additionally, the registry provides tools for managing images at scale, ensuring that the large number of images required for container applications can be easily managed and organized. This allows for easier collaboration among team members and helps to improve overall efficiency in the development process.
Importance of Uncovering Image Vulnerabilities
With any technology that involves the sharing and distribution of code, it is important to be aware of potential vulnerabilities. These vulnerabilities can be introduced at any stage of the development process, from the initial creation of the container image to the deployment of the application.
Because of the potential for vulnerabilities, it is crucial to have security measures in place to detect and prevent attacks. This includes regular vulnerability scanning and monitoring of all container images, as well as implementing measures to prevent unauthorized access to the registry. Failure to do so can leave organizations vulnerable to a range of cyber threats, including data breaches and malware attacks.
Azure Container Registry Images are an essential component of any container ecosystem. However, it is essential to be aware of potential vulnerabilities and to take the necessary steps to secure the registry and container images. By doing so, organizations can ensure that their applications are secure and protected from cyber-attacks.
Why Remediate?
One of the most critical aspects of ensuring secure containerization is understanding potential vulnerabilities. Common types of container vulnerabilities include exposure of sensitive data, injection attacks, and denial-of-service attacks. These vulnerabilities can arise if the container images are not correctly configured or if security patches are not up to date. For example, if a misconfigured container exposes sensitive data, such as login credentials or credit card numbers, it could lead to severe data breaches and financial losses for businesses.
If container images are not appropriately secured, there can be serious consequences. Hackers can exploit these vulnerabilities to gain unauthorized access to the container and compromise the integrity and confidentiality of the data. This unauthorized access could potentially result in data breaches, system downtime, and financial losses. It is, therefore, essential that container images be securely configured, and critical patches and updates be implemented timely, to avoid any negative consequences.
There are several benefits to securing container images. Firstly, secure container images provide better data protection, ensuring the confidentiality, integrity, and availability of data throughout its lifecycle. Secondly, secure containerization can help reduce the risk of data breaches, system downtime, and financial losses, which can adversely affect businesses' reputation and customer confidence. Finally, by ensuring secure containerization, businesses can improve regulatory compliance and meet industry standards and best practices.
Leveraging Microsoft Defender for Cloud Security Posture Management (DCSPM) to Prioritize Vulnerability Remediation
How You Can Easily Enable Container Registry Image Scanning
DCSPM provides an automated and agentless mechanism to identify vulnerabilities your container image repositories. The scans are done when image is pushed or imported to the registry and the images are continuously scanned every 7 days when they have been pulled in last 30 days or are actively running.
To leverage the scanning functionality:
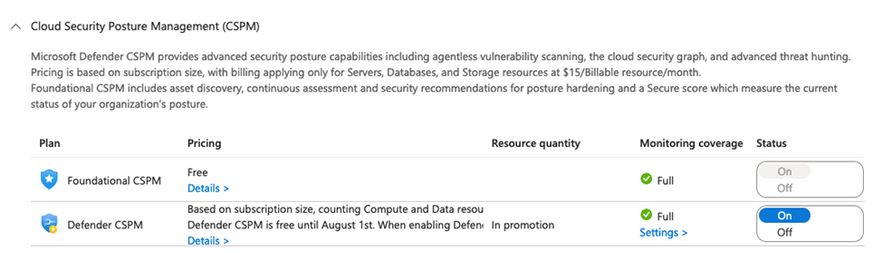
- First, enable DCSPM on relevant subscription such as those where you have production workloads and data. https://learn.microsoft.com/en-us/azure/defender-for-cloud/get-started.
Fig 1. Enabling DCSPM for relevant subscriptions
2. Next, enable the scanning feature under DCSPM Settings.
Fig 2. Enabling agentless container registry scans
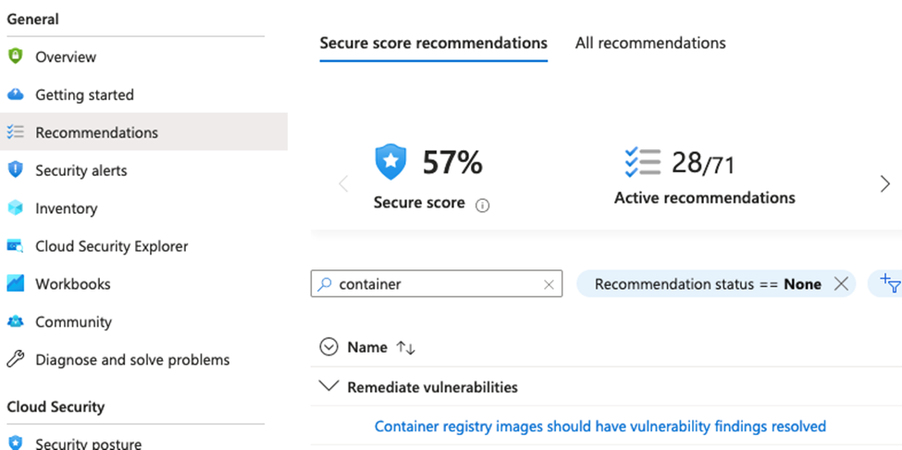
- Within few hours, the scan results will be available under the Recommendations blade.
Fig 3. Container registry image scanning results
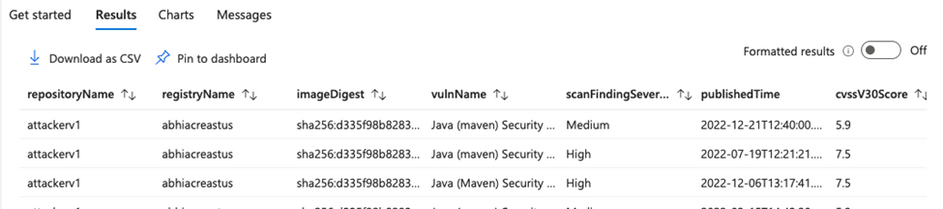
- You can see the detailed results by selecting the recommendation shown in Fig 3, above.
Fig 4. Detailed results of container image scan
3. You can now run the alerting and remediation workflows using Logic Apps or by setting up Remediation Governance https://learn.microsoft.com/en-us/azure/defender-for-cloud/governance-rules
Extend Functionality for Custom Reporting
DCSPM stores the scan results in Azure Resource Graph (ARG) so you can create custom reports by querying ARG (see query below). Doing so will allow you to create custom reports that you can share with other teams or leverage for remediation tracking cadence.
Once run, the query will result in a report such as this:
Fig 5. Custom vulnerability assessment report
Leveraging the Out-Of-Box Vulnerability Management Dashboard
Defender for Cloud also provides a capable dashboard that you can use for management level reporting. This dashboard provides a holistic view of vulnerabilities across your Virtual Machines, Containers Images, and Databases.
Unlike the traditional vulnerability Management solutions, the key advantage here is that you will always have the most up to date assessment of your posture. This is all achievable with minimal operational effort from your side.
Fig 6. Vulnerability Management dashboard
Summary
DCSPM provides a great mechanism that can serve your Container Registry Image scanning requirements. The feature is included in the cost of DCSPM and requires minimal operational overhead from your side. You can also extend the reporting capabilities further by using Azure Resource Graph (ARG), which is a free resource.