This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Introduction
Microsoft Defender for Cloud is a Cloud Native Application Protection Platform (CNAPP) that offers crucial insights and protective measures through its Attack Path risk analysis feature. A frequent requirement from customers is the ability to receive notifications whenever new attack paths are detected. This article presents an automated solution utilizing Azure Logic Apps to address this need. By deploying a custom Logic App using an Azure Resource Manager (ARM) template, organizations can establish a streamlined notification system for newly reported attack paths by Microsoft Defender for Cloud. This solution guarantees that security teams receive prompt alerts, empowering them to promptly respond and safeguard their cloud resources efficiently.
The Challenge - Timely Notification of New Attack Paths
One of the key challenges faced by organizations using Microsoft Defender for Cloud Attack Path analysis is the lack of built-in notification functionality for new attack paths. Attack paths provide crucial information about potential vulnerabilities and the paths that attackers can exploit to infiltrate cloud environments. However, without timely notifications, security teams may not be aware of these new attack paths, leaving their cloud infrastructure exposed to potential threats.
Moreover, the data stored within the Azure Resource Graph, where attack path information is collected, does not include timestamps indicating when attack paths were first generated or updated. As a result, organizations lack visibility into the recency of attack path reports, further hindering their ability to prioritize and respond to potential risks effectively.
One way to overcome this challenge is to use Azure Logic Apps and custom notifications to provide security teams with real-time updates on new attack paths. By deploying the Logic App using the provided ARM template, organizations can establish a reliable and automated process for receiving notifications whenever Microsoft Defender for Cloud reports new attack paths. This empowers security teams to stay ahead of potential vulnerabilities and take proactive measures to secure their cloud environments effectively.
Next, we will delve into the details of the solution, explaining how the Logic App works and the benefits it offers in terms of timely attack path notifications.
Attack Path Notification Process
Let's walk through the process of how this solution works:
Trigger: The Logic App is set to run daily using a recurring trigger. This ensures that Attack Paths are evaluated regularly.
Query Attack Paths: The Logic App retrieves Attack Paths data by making an API request to the Azure Resource Graph. It fetches important details such as Attack Path ID, display name, description, and attack path type.
Evaluate Attack Paths: The Logic App processes each Attack Path using a loop. For each path, it performs the following steps:
- Check Existence: The Logic App checks if the Attack Path already exists in the storage account table by making an API request.
- Update or Insert Entity: If the Attack Path exists, the Logic App updates the LastUpdate timestamp. If it doesn't exist, a new entity is created with the Attack Path details, and the Notified flag is set to "False" to indicate a pending notification.
- Send Notification: After updating or inserting the entity, the Logic App sends email notification using the Office 365 connector. The notification includes important Attack Path details and a link to view the details in Defender for Cloud.
Notification Body: The Logic App constructs the email notification body using HTML formatting, making it visually appealing and informative.
Storage Account and Table: It's important to have a storage account and table in place for the Logic App to function correctly. Attack Path entities are stored in this table, enabling the Logic App to query and update them. This is necessary because the Azure Resource Graph data for Attack Paths lacks the specific date and time of their generation and update.
Recurring Frequency: It is recommended to set the Logic App's recurrence frequency to once a day. This aligns with the frequency at which Attack Paths are evaluated and reported by Defender for Cloud.
Prerequisites
For the Logic App to work and utilize its capabilities to send Attack Path notifications, there are several prerequisites that need to be in place. Here are the prerequisites you need to consider:
- Logic App System Identity: A Logic App System Identity is created when deployed, however there is a need to configure it with the necessary permissions to read all subscriptions. This will enable the Logic App to query for Attack Paths data using the Azure Resource Graph API. The required permissions should include read access to relevant subscriptions where Attack Paths is enabled (Defender for CSPM).
- Storage Account and Table: Set up a storage account in Azure that will be used to store the Attack Path entities and enable the Logic App to query and update them. Create a table within the storage account to store the Attack Path data. This table will serve as the central repository for storing information related to Attack Paths.
- MS365 Outlook Account: Ensure that you have an active Microsoft 365 (MS365) Outlook account or an account with access to the Microsoft 365 email service. This account will be used by the Logic App to send email notifications for the new Attack Paths detected.
- Logic App API Connections: Configure the necessary API connections within the Logic App to access the Storage Account Table and send emails via MS365 Outlook. You will need to provide the appropriate connection details and authenticate the Logic App with the required permissions for accessing the Storage Account and sending emails.
- Storage Account Shared Storage Key: Obtain the shared storage key for the configured storage account. This key will be used to authenticate the Logic App when accessing the Storage Account Table and perform operations such as querying and updating Attack Path entities.
Optional Step: Populating Azure Storage Account and Table with Existing Attack Paths
As part of the solution, we provide an optional PowerShell script that enables you to create an Azure Storage Account and Table, and populate it with the existing Attack Paths. This step is particularly useful if you have multiple Attack Paths already present and you prefer not to receive notifications for all of them. By populating the table, you can set the state to zero and ensure that only new Attack Paths detected from that moment onward trigger notifications.
To use the provided script, follow these instructions:
Ensure that you have the Azure PowerShell modules "Az", “Az.ResourceGraph”, “AzTable” installed.
Replace <Subscription ID> with the ID of the Azure subscription you want to work with. Replace <Storage Account Name> with the Azure Storage Account Name of your choice.
After executing the script, you will see a success message indicating that the data has been successfully populated in the specified table.
By following these steps and populating the Azure Storage Account and Table with existing Attack Paths, you can ensure that only new Attack Paths trigger notifications while excluding the ones already present in the table.
Please note that this step is optional and only necessary if you have existing Attack Paths that you want to exclude from the initial notification process.
Verifying and Configuring API Connections
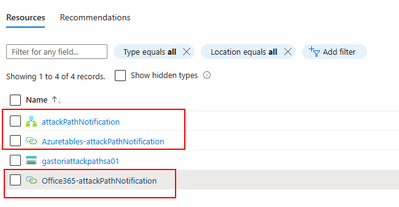
Once you have deployed the Logic App, it is essential to verify and configure the API connections used within the Logic App to ensure their proper functioning. The API connections, namely "Azuretables" and "Office365," require attention to establish successful communication with the corresponding services. Follow the steps below to verify and configure the API connections:
- Access the Azure portal and navigate to the deployed Logic App.
- Within the Logic App designer, identify the API connections utilized by the Logic App: "Azuretables" and "Office365."
- Click on each API connection to access its settings and configuration.
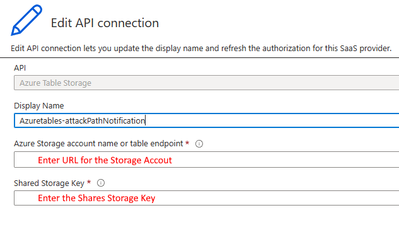
- For the "Azuretables" API connection:
a. Confirm that the connection is enabled.
b. Verify the connection details, including the storage account and table, to ensure they align with your configuration.
c. Make any necessary modifications to the connection settings as per your requirements.
- For the "Office365" API connection:
a. Enable the connection if it is not already enabled.
b. Validate the connection details, such as the M365 Outlook account and other settings.
c. Adjust the connection settings if needed to match your specific configuration.
- Save the changes made to the API connections.
- Proceed to test the API connections to ensure their proper functioning:
a. Within the Logic App designer, locate the "Test" button at the top of the screen.
b. Follow the provided prompts to supply any required inputs for the test.
c. Execute the test and carefully examine the results for any errors or issues.
- If the test runs successfully without any errors, it indicates that the API connections are properly configured and functional.
Conclusion
By diligently following these steps, you can verify and configure the API connections used within the Logic App. This process guarantees seamless communication between the Logic App and the corresponding services, enabling the accurate and timely delivery of notifications based on the Attack Path data.
Additional Resources
If you are using Attack Path and Cloud Security Explorer and want to share your feedback with the Defender for Cloud Team, please e-mail us directly from here. You can also use the resources below to learn more about these capabilities:
- Cloud security explorer and Attack path analysis (Video)
- Identify and remediate attack paths
- Microsoft Defender for Cloud Security Posture Management
- GitHub Repository - Notify-NewAttackPath
Reviewers
Yuri Diogenes, Principal PM Manager, CxE Defender for Cloud