This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Alerts, the hero or the devil?
Alerts in Microsoft Defender for Cloud are notifications generated when potential security threats and anomalous activities are detected within your cloud environment. These alerts provide crucial information and insights, enabling SecOps teams to effectively identify, prioritize, and respond to potential malicious activity. Learn more about Defender for Cloud alerts here: https://learn.microsoft.com/en-us/azure/defender-for-cloud/alerts-reference
Too many alerts, however, can overwhelm security teams with a high volume of notifications, leading to alert fatigue. SecOps teams may struggle to prioritize and address genuine threats effectively. Additionally, due to the limited resources available to SecOps teams, alert fatigue may take time away from true threat investigations, potentially leaving critical cyber threats unaddressed.
This is why prioritization matters. In this blog, we will talk about the mechanisms of security alerts and incidents and explain incident templatization with recent research on crypto mining as an example.
What are Incidents in Defender for Cloud?
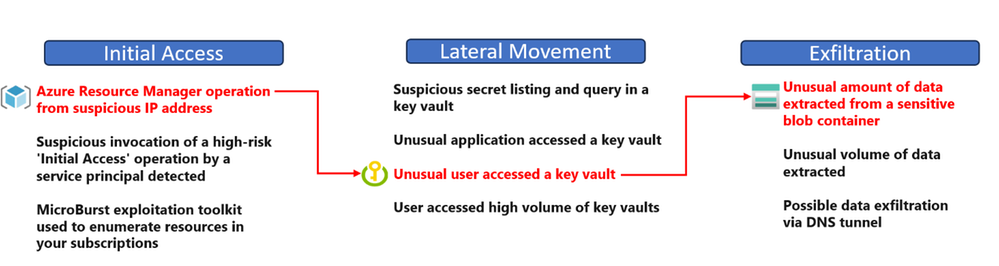
In Microsoft Defender for Cloud, are correlated collections of related alerts that are likely to be parts of the same attack. This approach allows for reducing the number of low-fidelity alerts and consolidating them into a single informative incident. Unlike individual alerts, incidents enable security teams to gain vital information and prioritize their response efforts quickly. In addition, security teams can more efficiently manage their workflow, allocate resources, and ultimately enhance their ability to detect and respond to security threats in real time. This correlation enables security teams to understand which alerts are connected in the different phases of an attack, as shown in the example below:
Microsoft Defender for Cloud's protects multiple layers of your cloud environment, including compute, data, and service. The more protection plans customers enable, the more complete the view of potential incidents that might occur. By correlating alerts across these plans and converting them into incidents, SecOps teams can more efficiently detect suspicious activities, analyze their significance, and respond accordingly by leveraging all the available information.
How does alert correlation work?
Every alert in the Microsoft Defender for Cloud platform contains entities such as “User”, “IP address”, and “Resource ID”. Microsoft Defender for Cloud correlates on the alerts entities and triggers an incident on correlation of alerts that share an attack story, here are few examples of attack stories:
Suspicious IP activity:
This incident indicates that suspicious activity has been detected originating from a potential malicious IP address. Multiple alerts have been triggered from the same IP address, which increases the fidelity of malicious activity in your environment. Suspicious activity originating from a suspicious IP address may indicate that an attacker has gained unauthorized access to your environment and is attempting to compromise it.
Suspicious User activity:
This incident indicates a series of suspicious activities involving a user account within your Cloud environment. Multiple alerts have been triggered by this user, which increases the fidelity of malicious activity in your environment. While this activity may be legitimate, a threat actor might utilize such operations to compromise resources in your environment. This may indicate that the account is compromised and is being used with malicious intent.
Suspicious Kubernetes cluster Activity:
This incident indicates that suspicious activity has been detected on your Kubernetes cluster following suspicious user activity. Multiple alerts have been triggered on the same cluster, which increases the fidelity of malicious activity in your environment. The suspicious activity on your Kubernetes cluster may indicate that a threat actor has gained unauthorized access to your environment and is attempting to compromise it.
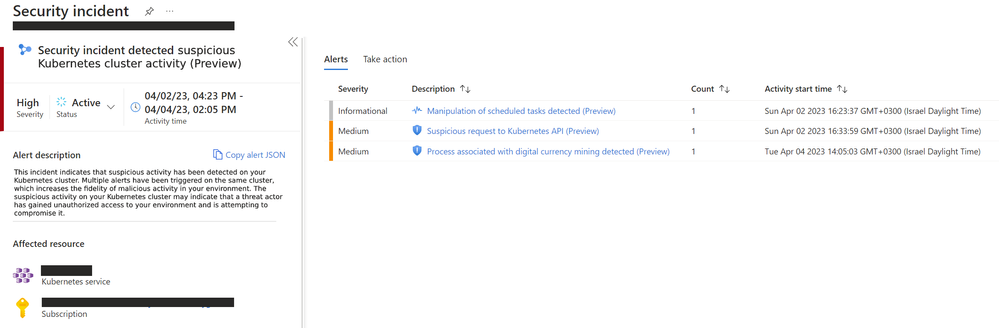
Here is an example of a triggered Suspicious Kubernetes cluster activity:
In this example, a manipulation of scheduled tasks, followed by a suspicious request to the Kubernetes API and a process associated with digital currency mining, all triggered on the same Kubernetes cluster. This may indicate that the Kubernetes cluster is compromised and is being used with malicious intent.
How are incidents born? – case study with SAS token
To provide the best quality incidents, MDC Researchers continuously work to find meaningful correlations of alerts and create new incidents that tell specific attack stories. As part of our research, we conduct threat hunting, investigate alerts, and leverage feedback from customers. As a result, we build new incidents that are based on real attacks. One such example of an attack is exfiltration activity involving SAS. SAS is a token-based authentication mechanism that grants limited access to Azure Storage resources. It provides a secure way to share resources without exposing the account key or requiring the user to authenticate with the storage account. To learn more about SAS, please visit the documentation here: Grant limited access to data with shared access signatures (SAS) - Azure Storage | Microsoft Learn.
There are multiple ways for threat actors to abuse SAS on Storage account, here is one example of such an attack:
- Before the attack, a threat actor discovers the victim's SAS by locating it on compromised VM, scanning public repositories for SAS, or intercepting it on unencrypted network channels like HTTP.
- Upon acquiring a SAS, the attacker attempts to use it for external access to a storage account and verify its validity.
- If the SAS has sufficient permissions, the threat actor explores the storage account for sensitive or important blobs and files.
- Once the threat actor finds blobs containing sensitive information, they initiate the exfiltration process to steal valuable data.
Microsoft Defender for Cloud provides a comprehensive list of alerts addressing various aspects of this scenario. By correlating relevant alerts, suspicious SAS activity incident is triggered with the following description:
“This incident indicates that suspicious activity has been detected following the potential misuse of a SAS token. Multiple alerts have been triggered on the same resource, which increases the fidelity of malicious activity in your environment. The usage of a SAS token can indicate that a threat actor has gained unauthorized access to your storage account and is attempting to access or exfiltrate sensitive data.”
In summary, a considerable leap forward in the realm of cloud security. This enhancement not only offers advanced threat detection capabilities to tackle emerging risks, but also provides additional context for customers in safeguarding their valuable assets in the cloud. For a comprehensive list of the new incidents covered, please refer to the documentation.