This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
The latest addition to Defender for Containers, Agentless Discovery for Kubernetes, empowers security-conscious organizations with new capabilities to gain insights into the security landscape of their Kubernetes workloads.
Previously available for customers in Defender Cloud Security Posture Management (DCSPM), it is now being integrated as a core component of Defender for Containers. Agentless Discovery empowers you to gain higher visibility into the security landscape of your Kubernetes workloads, if you choose not to install additional agents.
In Defender for Containers, the following capabilities are made possible by enabling Agentless Discovery for Kubernetes:
- Kubernetes inventory capabilities with cloud security explorer - explore Kubernetes resources, such as pods, services, container images, and their internal relations, across containerized environments, allowing you to monitor and manage your assets effectively. The Cloud Security Explorer is an amazing tool for visualizing and understanding the security in rich context.
Figure 1 - example of K8S Inventory query that presents all pods in the selected scope
- Kubernetes-Specific Security Insights - provide a clear understanding of potential security risks within your environment, such as “exposed to the internet” or “Vulnerable to remote code execution”.
Figure 2 - Example of K8S security insight: all container images in the scope, which are vulnerable to remote code execution
- Enhanced Risk-Hunting with Cloud Security Explorer - enables you to evaluate both custom, as well as predefined security exposure scenarios (for example: “internet-exposed pod running a vulnerable image”).
Figure 3 – Example of a query that allows you to filter on different Kubernetes entities and see vulnerability assessment results
- Container registry vulnerability assessment – visualize the vulnerability assessment situation across your Kubernetes workloads with ease and efficiency as it is displayed
Understanding Our Agent-Based and Agentless Offerings
As a complement to the introduction of Agentless Discovery, it's important to consider its benefits in relation to the existing agent-based approach. If you're looking for a comprehensive understanding of these two options, Microsoft has provided a detailed comparison in a previous blog post titled "Comprehensive Guide on Agent-Based and Agentless Cloud Security".
In the comparison guide, you'll explore:
- Coverage: Delve into the level of visibility and control each approach offers over your containerized environment.
- Operational Overhead: Understand the differences in managing agents versus opting for an agentless solution.
- Performance: Learn how performance plays a role in the choice between the two approaches.
- Use cases: see when it is recommended to opt for one of the approaches or for both
Agentless discovery for Kubernetes vs. Defender profile (agent based approach)
|
Capability categories |
Agentless / Agent based |
|
Vulnerability assessment for running images |
Can utilize either Defender profile (agent based) or Agentless discovery for Kubernetes (or both) |
|
Run-time threat protection |
Needs both Defender profile (agent based) and Audit-log (agentless) for full value |
|
Context-graph based capabilities (Security Explorer, K8S inventory, K8S insights, risk hunting, visualization of VA across K8S workloads) |
|
Call for action:
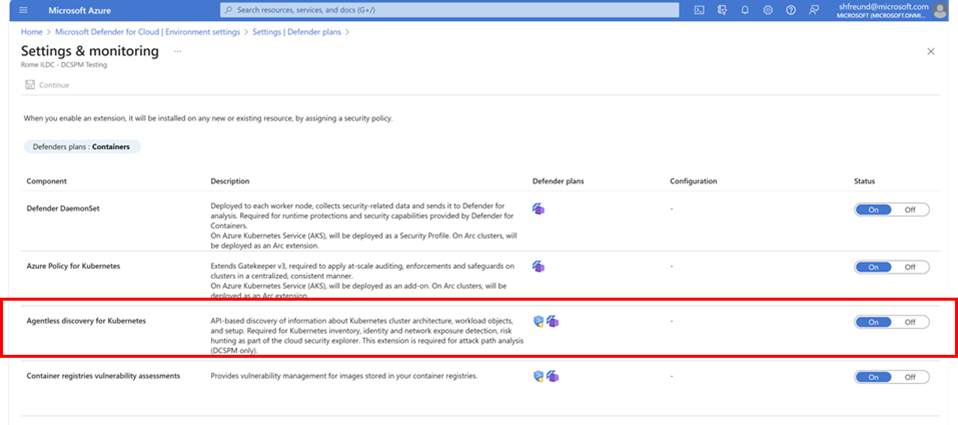
Defender for Containers customer who don’t have the “Agentless discovery for Kubernetes” extension enabled as part of Defender CSPM, are encouraged to manually enable the extension in the “Environments and settings” blade of Defender for Containers.
We encourage you to update your subscriptions to have the full set of extensions enabled, and thus benefit from the latest additions and features.
Note: enabling the latest additions will not incur new costs to active Defender for Containers customers.