This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Detect and prevent data security incidents with Microsoft Purview. Combine data classification with proactive and adaptive data loss prevention policies aligned to the assessed insider risk level for a multi-layered approach.
Trusted insiders working for your organization contribute to 25% of data breaches. Many of these breaches remain undetected or are discovered long after the damage is done. We deconstruct what occurred at a prominent company with an account inspired by a true story of corporate espionage and how Microsoft Purview is designed to detect and prevent this type of data security incident.
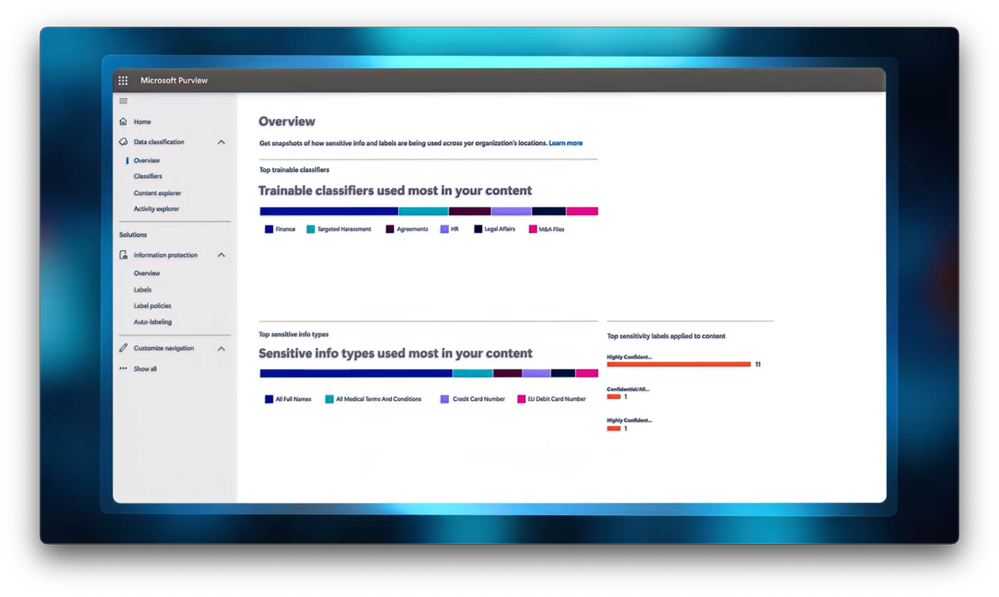
Know your sensitive data.
Get a 360 degree view across your data estate — ready to use in Microsoft Purview.
Secure data with adaptive policies, dependent on a user’s risk level.
Check out data security strategies with Microsoft Purview.
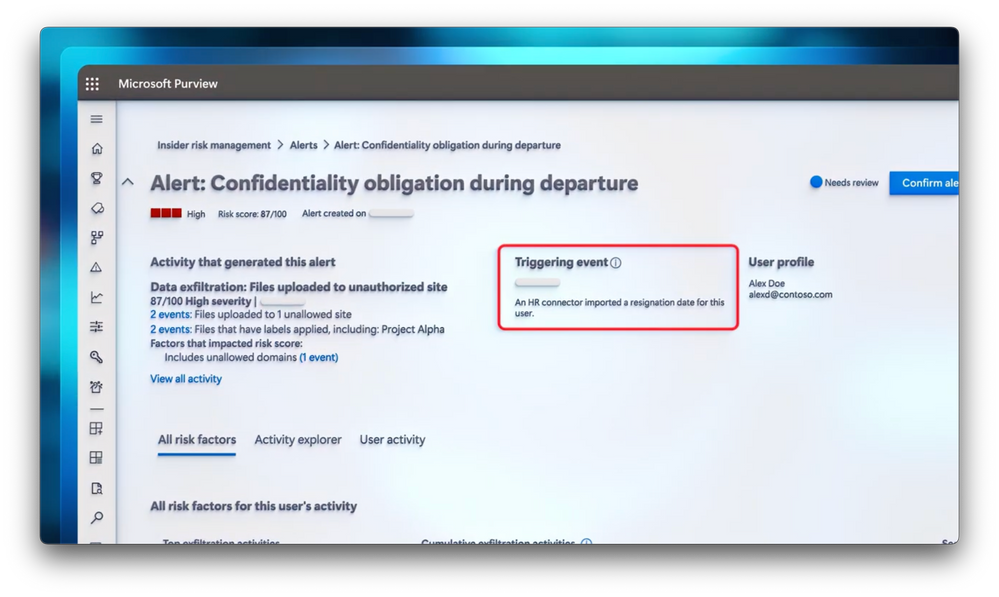
Recognize potential risks.
Take action before risks escalate. Check out Insider Risk Management with Microsoft Purview.
Watch our video.
QUICK LINKS:
00:00 — Detect and prevent data security incidents
00:29 — Watch a real crime case
02:06 — Data security strategies
02:55 — Secure data with policies
04:10 — Insider Risk Management
04:40 — Wrap up
Link References:
Check out our comprehensive series at https://aka.ms/DataSecurityMechanics
Unfamiliar with Microsoft Mechanics?
As Microsoft’s official video series for IT, you can watch and share valuable content and demos of current and upcoming tech from the people who build it at Microsoft.
- Subscribe to our YouTube: https://www.youtube.com/c/MicrosoftMechanicsSeries
- Talk with other IT Pros, join us on the Microsoft Tech Community: https://techcommunity.microsoft.com/t5/microsoft-mechanics-blog/bg-p/MicrosoftMechanicsBlog
- Watch or listen from anywhere, subscribe to our podcast: https://microsoftmechanics.libsyn.com/podcast
Keep getting this insider knowledge, join us on social:
- Follow us on Twitter: https://twitter.com/MSFTMechanics
- Share knowledge on LinkedIn: https://www.linkedin.com/company/microsoft-mechanics/
- Enjoy us on Instagram: https://www.instagram.com/msftmechanics/
- Loosen up with us on TikTok: https://www.tiktok.com/@msftmechanics
Video Transcript:
-Did you know that 25% of data breaches are caused by trusted insiders working for your organization? Many of these breaches remain undetected or are discovered long after the damage is done.
-Today, we’ll deconstruct what occurred at a prominent company focused on packaged goods with an account inspired by a true story of corporate espionage and how Microsoft Purview is designed to detect and prevent this type of data security incident. Alex, whose real name were concealing, is an accomplished principle researcher. They’re on point for selecting a vendor who can meet the requirements of a new packaging regulation, but this soon takes on a different direction. Over two years, Alex collects confidential sensitive data and deliberately holds it for their own exclusive access on their corporate device. They also exploit their position to create a custom non-disclosure agreement requiring partners to entrust their valuable intellectual property solely to them.
-Unbeknownst to their employer, Alex is also orchestrating a secret collaboration with a foreign government program that seeks to acquire trade secrets from citizens working abroad, but it’s not their data related actions that draw attention. Rather, it’s Alex’s abrasive communication with colleagues and partners that subsequently leads to their termination. Undeterred and on their way out, while initially blocked, they defy existing data loss prevention policies. They take the data with them by uploading sensitive information to a personal cloud storage account that wasn’t blocked by policy. Alex next joins a related company to continue their espionage, even though their pursuit of data exceeds their job scope.
-Again, it’s their interpersonal clashes, not their data exfiltration activities that lead to their termination, and it doesn’t end there. Alex moves to yet another company to continue their data exfiltration activities. It’s only after a detailed government-led investigation that Alex is apprehended for stealing tens of millions of dollars in corporate data over a span of five years. So let’s delve into the data security strategies that can prevent this type of insider event. Microsoft Purview provides a multi-layered approach to data security. First, and notably, there was limited visibility into the data Alex was accumulating across different roles. Knowing your company’s data is foundational to protecting it, and Microsoft Purview provides a 360 degree view across your data estate.
-Built in, ready to use machine learning based classifiers are pre-trained extensively on large samples of industry relevant data, including, in this case, intellectual property and NDA information for the automated detection, labeling and classification of sensitive data across your data estate without any upfront manual effort required. Classified information can be watermarked and governed by policy with data loss prevention policies blocking specific actions, such as limiting the locations to where data can be uploaded to only the company’s managed SharePoint and OneDrive, which blocks all other destinations by default. You can also apply encryption and scope access to prevent unauthorized access to the data. Importantly, these protections can also be adaptive with different policies applied dependent on the user’s risk level. Now remember, Alex Doe was a highly privileged individual working with sensitive data.
-With Adaptive Protection in Microsoft Purview, their actions would’ve dynamically raised their risk level after their policy violation and attempting to exfiltrate data via their personal hard drive, therefore, automating more proactive and elevated protections. In parallel, Alex’s abrasive communication with others would provide another indicator of potential insider risk that could lead to a security incident. In collaboration apps, like Microsoft Teams or Outlook, communication compliance in Microsoft Purview can automatically flag violations in communications, and the built-in machine learning models, such as inappropriate texts, can surface the telltale signs of wrongdoing.
-Additionally, insider risk management, with its privacy led approach, enabled by dozens of built-in indicators and machine learning models can sequence anomalous activities to establish possible malicious intent. Importantly, swiftness and response matters. Automated alerts instantly notify security teams and involve human resources and legal teams about potential risks to facilitate rapid intervention before risks escalate to ensure the right level of investigation.
-In fact, this multi-layered approach to data security in Microsoft Purview incorporates a fusion of data classification, along with proactive and adaptive data loss prevention policies all aligned to the assessed insider risk level. Or you can start anywhere. Together, these solutions can substantially diminish the vulnerabilities posed by insider risks that could lead to your security incidents. For a deeper dive into these strategies, check out our comprehensive series at aka.ms/DataSecurityMechanics and thanks for watching.