This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
We are announcing the new implementation of Azure CLI and Azure PowerShell commands to create Azure Key Vault.
Advantages
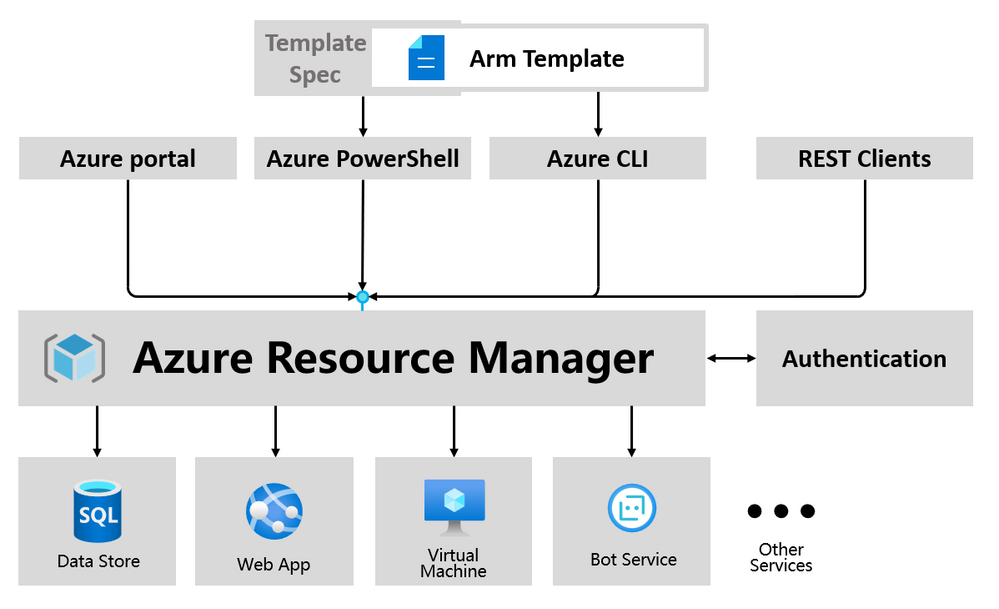
We leverage the ARM template mechanism to refactor the Key Vault command line. Compared with the previous implementation, calling REST API through SDKs, this implementation scheme has the following advantages that users can benefit from.
- Consistency. Ensure consistent behavior and defaults between Azure CLI, Azure PowerShell, and Portal.
- What-If. Support a ‘what if’ option to predict the impact of a deployment before the command is executed.
- Idempotency. Sending the same request multiple times will produce the same result, regardless of resource state.
What’s new
We implemented several new features when compared to the previous version of commands.
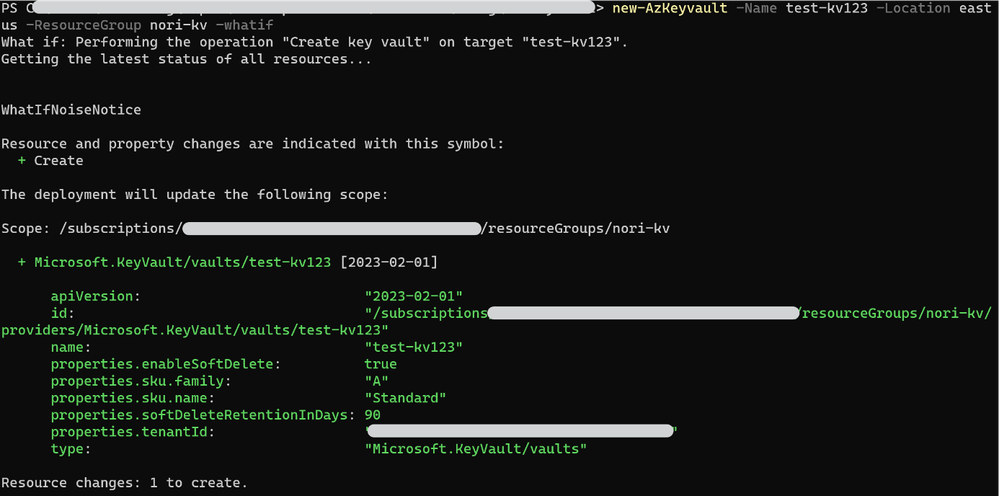
What-If
What-If is designed to show users as much information about what their deployment will do before it deploys.
Progress Bar
We have implemented a progress bar to visualize the deployment.
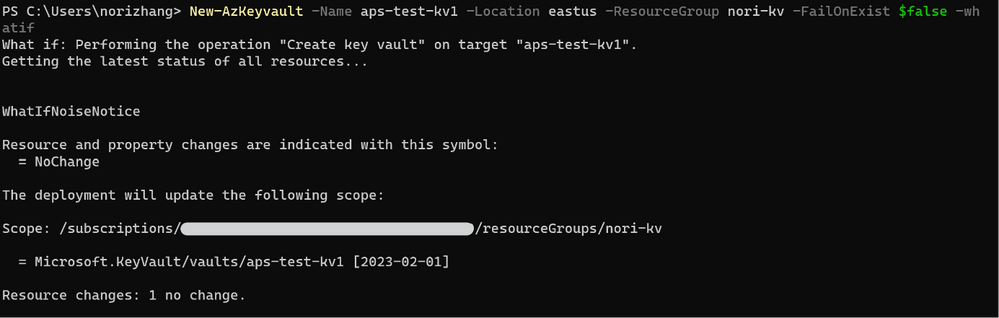
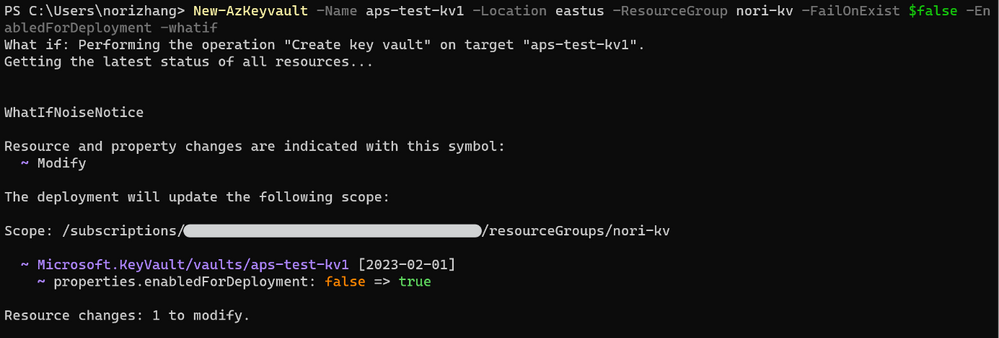
Idempotency
We are using the incremental mode of ARM deployment to create key vaults. By setting –FailOnExist as $false, we can repeatedly create the same key vault or update the existing one.
Deep Dive
For Key Vault creation, Azure Client Tools previously followed a different structure than Azure Portal, as shown in the following example:
With the ARM template included, we maintain consistency and communicate directly with ARM:
We are using template specs to make staging and sharing of ARM templates easy.
Next Steps
We look forward to your feedback. We will evaluate the effects and risks and consider expanding the command line scope of service, module, and extension.
Getting Started
You can test our new version by following the instructions provided below. Your feedback will help shape the strategy of how we build the command line tools for Azure.
Getting started with Azure PowerShell
The PowerShell package for private preview is provided on the PowerShell Gallery.
Installation
Copy and paste the following command to install this package using PowerShellGet:
Install-Module -Name Az.KeyVault -RequiredVersion 4.12.0-preview -AllowPrerelease
Quick Start
# 1. Create a Resource Group
New-AzResourceGroup -Name $resourceGroupName -location $location
# 2. Validate the creation of a key vault using `-WhatIf`
New-AzKeyvault -Name $keyvaultName -Location $location -ResourceGroupName $resourceGroupName -WhatIf
# 3. Create a key vault, observe the deployment once the command has completed
New-AzKeyvault -Name $keyvaultName -Location $location -ResourceGroupName $resourceGroupName
# 4. See what will happen if create a key vault in incremental mode and do a little change
New-AzKeyvault -Name $keyvaultName -Location $location -ResourceGroupName $resourceGroupName -FailOnExist $false -EnabledForDeployment –WhatIf
# 5. Create the existing key vault in incremental mode
New-AzKeyvault -Name $keyvaultName -Location $location -ResourceGroupName $resourceGroupName -FailOnExist $false
# 6. Clean-up Azure resources
Remove-AzResourceGroup -Name $resourceGroupName
Getting started with Azure CLI
The CLI package for public preview is provided as MSI / whl packages:
For MSI package Installation
Download and install the MSI package. When the installer asks if it can make changes to your computer, select "Yes". If you have previously installed the Azure CLI, make sure it has been uninstalled first.
For whl package Installation
- Prepare and use a separate virtual environment
# Create a python virtual env named `testenv` with: python -m venv testenv # Activate the env (if you are using powershell): .\testenv\Scripts\Activate.ps1 # Activate the env (if you are using bash): source venv/bin/activate - Unzip and install private .whl packages
# Unzip the file and install three cli whl packages (azure_cli, azure_cli_core, azure_cli_telemetry) pip install azure_cli-2.53.0.post20230920063357-py3-none-any.whl azure_cli_core-2.53.0.post20230920063357-py3-none-any.whl azure_cli_telemetry-1.1.0.post20230920063357-py3-none-any.whl
Quick Start
# 0 Define your variables
let "randomIdentifier=$RANDOM*$RANDOM"
location="eastus"
resourceGroupName="msdocs-keyvault-rg-$randomIdentifier"
keyvaultName = "msdocs-keyvault-name-$randomIdentifier"
# 1. Create resource group
az group create --resource-group $resourceGroupName --location $location
# 2. Validate the creation of a keyvault using `--what-if`
az keyvault create --name $keyvaultName --resource-group $resourceGroupName --location $location --what-if
# 3. Create a keyvault, observe the deployment once the command has completed
az keyvault create --name $keyvaultName --resource-group $resourceGroupName --location $location
# 4. See what will happen if create a keyvault in incremental mode and do a little change
az keyvault create --name $keyvaultName --resource-group $resourceGroupName --location $location --enabled-for-deployment --fail-on-exist false
# 5. Create the existing keyvault in incremental mode
az keyvault create --name $keyvaultName --resource-group $resourceGroupName --location $location --fail-on-exist false
# 6. Clean-up Azure resources
az group delete -name $resourceGroupName
For whl package clean up
# Deactivate the virtual environment
Deactivate
# Delete the virtual environment folder to clean up (if you are using linux)
rm –rf .\testenv
Feedback
This feature is already available. Feel free to share your experience by participating in our survey. We welcome your feedback!