This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Introduction
The healthcare industry is no stranger to complex data management challenges, especially when it comes to securing sensitive information. As technology continues to evolve, healthcare professionals are increasingly turning to modern frameworks like Blazor to streamline operations and improve patient outcomes. However, as with any new technology, there are challenges to overcome. One of the biggest hurdles is implementing delegated OAuth flow, a security measure that allows users to authenticate with delegated permissions. In this blog post, we'll explore step-by-step how Visual Studio and MSAL tools can accelerate your time to value and abstract away many of the complexities in the OAuth delegated flow for Blazor.
Pre-requisites
-
Latest version of Visual Studio 2019 with the ASP.NET and web development workload
-
Azure Active Directory Tenant with access to:
Setting up the Blazor Web Assembly Project
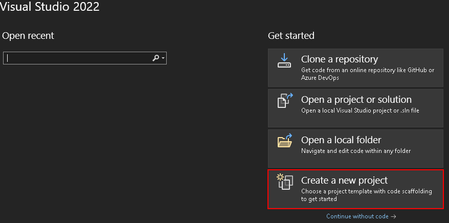
- Open Visual Studio and create a New Blazor Web Assembly project and provide the name of your project and local file path to save the solution.
- On the Additional Information screen, select the following options:
- Framework: .NET 7
- Authentication Type: Microsoft Identity Platform
- Check the box for ASP.NET Core Hosted
- Hit Create to continue
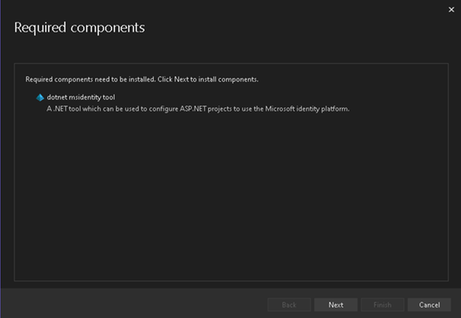
- You will now be seeing the Required components window with the dotnet msidentity tool listed. Press next to continue.
- Follow the guided authentication window to authenticate your identity to your target Azure tenant.
- this is so that Visual Studio is able to assume your identity to create the AAD application registrations for the Blazor Web Assembly.
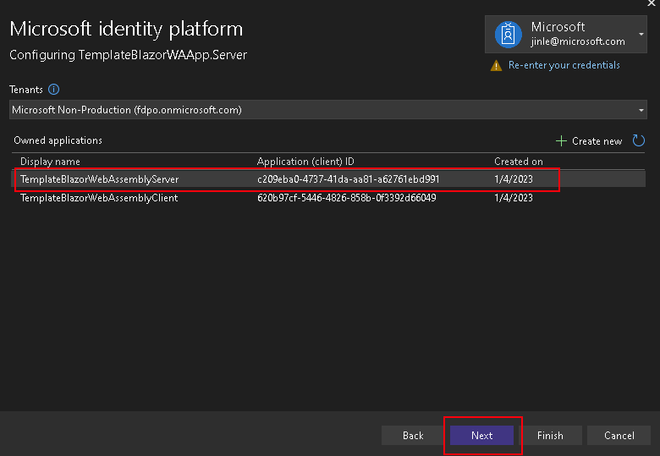
- Once authenticated, you will see a list of owned applications for the selected tenant. If you have previously configured application registrations, you can select the respective application here.
- For the purposes of this demo, we will create a new application registration for the server.
- Once the application is created, select the application you have created.
- Hit Next to proceed.
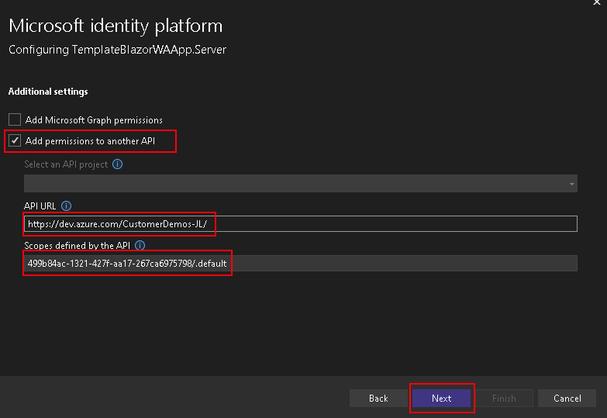
- In the next prompt we will provide information about the target Azure DevOps service, choose the Add permissions to another API option to let Visual Studio configure the Azure DevOps downstream API.
- API URL - Provide your Azure DevOps organization URL (example: https://dev.azure.com/CustomerDemos-JL).
- Scopes - set to 499b84ac-1321-427f-aa17-267ca6975798/.default
- Note: this value does not change, as it is the unique GUID for Azure DevOps APIs with the default scope.
- Hit Next to proceed.
- Next, the tool will create a client secret for your newly created app registration. You can choose to save this locally (outside of the project/git scope) or copy it to manage it yourself.
- Note: if you choose to not save to a local file, the secret will not be accessible again and you will need to regenerate the secret through the AAD app registration portal.
- Afterwards, review the Summary page and selectively decide which components the tool should modify in case you have your own configuration/code already in place.
- For this demo, we will keep all boxes selected.
- Hit Finish to let the tool configure your project with the Microsoft Identity Platform!
Test your Blazor Web Assembly Project's Microsoft Identity Platform Connectivity
Now that the Blazor Web Assembly project is provisioned, we will quickly test the authentication capabilities with the out-of-the-box seed application.
- On the Visual Studio window after provisioning is completed, our solution will now have both the Client and Server projects in place
- Ensure your Server is set as your Startup Project
- If it isn't, you can do so by right clicking your Server Project on the Solution Explorer.
- Ensure your Server is set as your Startup Project
- Test your OAuth configuration
- Run your application locally
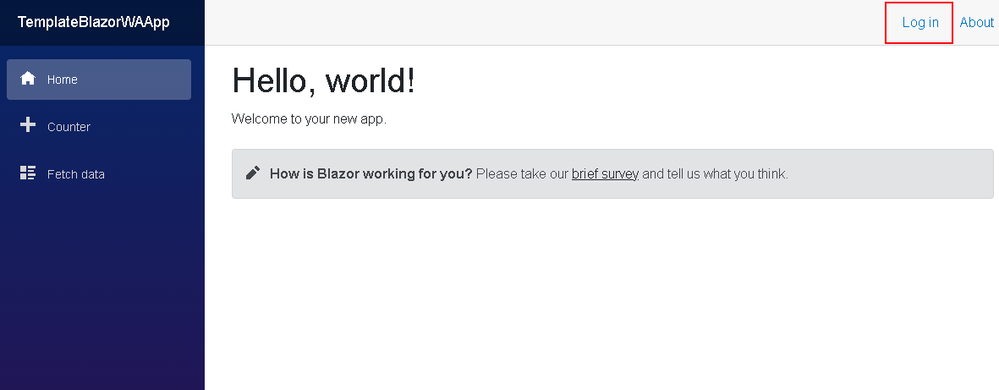
- On the web application, press the Log in button on the top right corner to log into your Azure DevOps organization
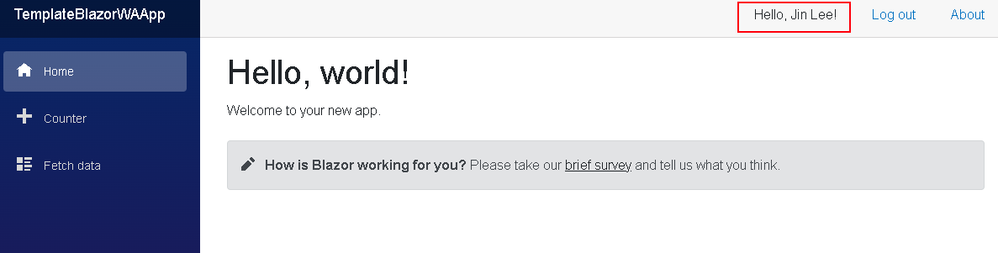
- Once logged in, you should see a Hello, <First name> <Last name>! message
- Getting to this point verifies that you are able to authenticate to Azure Active Directory, but not necessarily Azure DevOps as we have yet to configure any requests to the Azure DevOps REST APIs.
- Run your application locally
[Alternative Route] AAD App Registration Configuration
If you chose not to use the template-guided method of provisioning your Blazor application with MS identity, there are some steps you must take to ensure your application registration to function properly.
- Navigate to your tenant's Active Directory > App registrations
- Note the two application registrations - one for the Server, and another for the Client
- Configuring the Server app registration
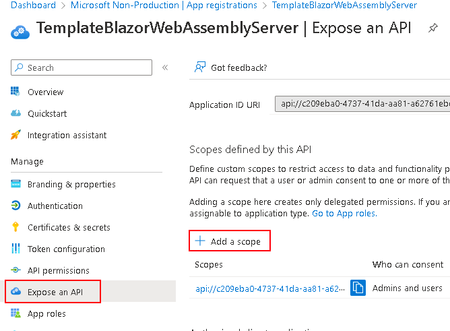
- In order to allow your application to assume the logged-in identity's access permissions, you must expose the access_as_user API on the application registration.
- to do this, select Expose an API on the toolbar and select Add a Scope
- For the Scope Name, ensure you provide access_as_user as well as selecting Admins and users for Who can consent?
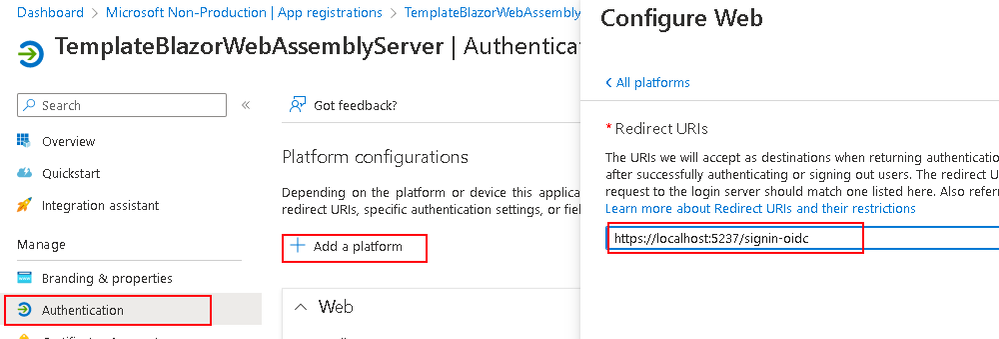
- Now go to the Authentication blade and select Add a platform to configure your Web platform's API redirect
- For when you deploy to your cloud services, the localhost will be replaced by your application's site name but will still have the /signin-oidc path by default for redirects (can be configured within your appsettings.json)
- to do this, select Expose an API on the toolbar and select Add a Scope
- On the same page (Expose an API) select Add a client application around the bottom to add your Client app registration's Application ID to allow for your client to call this API
- Save the authorized scopes for your client configuration within your Visual Studios project
- Save the authorized scopes for your client configuration within your Visual Studios project
- In order to allow your application to assume the logged-in identity's access permissions, you must expose the access_as_user API on the application registration.
- Configuring the Client app registration
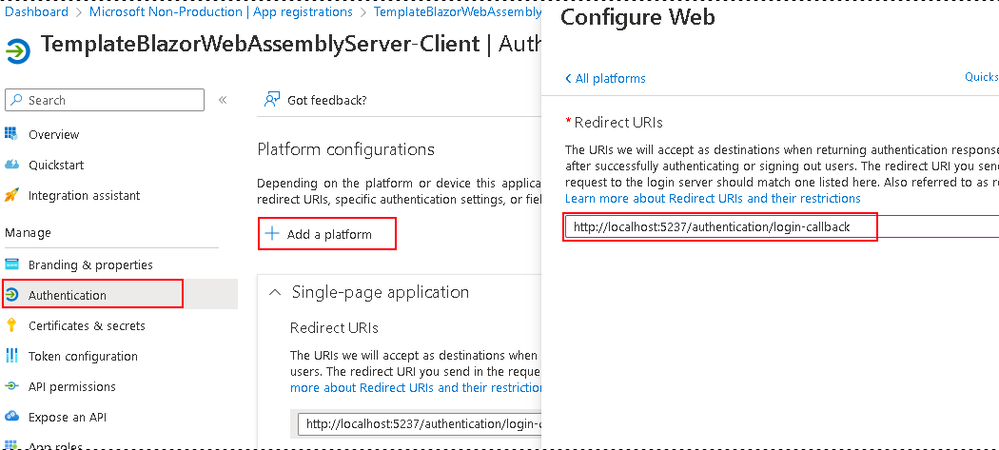
- Navigate to the Authentication blade and do the same as in step 2.b but for your client's callback URL
- Now ensure that both your client and server's appsettings.json in the Web Assembly project mirrors your app registration's configurations
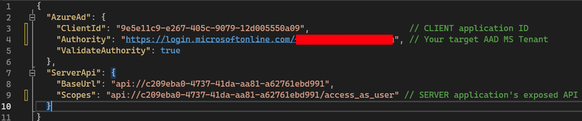
- Client app settings can be found within the wwwroot directory by default and should have the following details
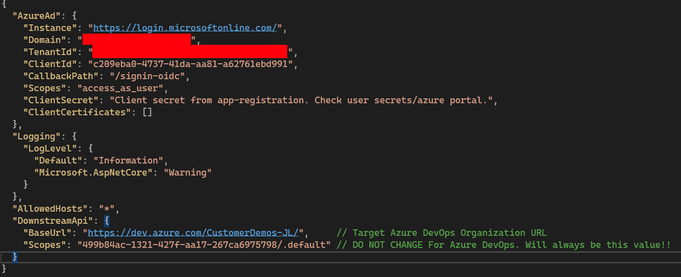
- Server app settings can be found at the base tree and should look like the following
- Client app settings can be found within the wwwroot directory by default and should have the following details