This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Background:
In the azure portal, we usually manually assign the access control for app service such as storage account, Virtual Machine, Log analytics workspace. However in some scenario, user wants create a container in the storage account and then give the RBAC to other user automatically by logic app. This article is a design to use logic app to give other user RBAC permission via rest API.
Design:
Step 1: We need to know the role definition Id for the aim RBAC
We can using the power shell code in the azure portal to get the role definition id:
- Open the PowerShell in azure portal:
-
Enter 'az' to connect to use azure CIL, this step might need to wait one minute
3. Enter the commend: 'Get-AzRoleDefinition | select-object name, id'For example:
Storage Blob Data Contributor ba92f5b4-2d11-453d-a403-e96b0029c9fe
Step 2: Create a service principle/app registration to have the authorization to assign the RBAC role.
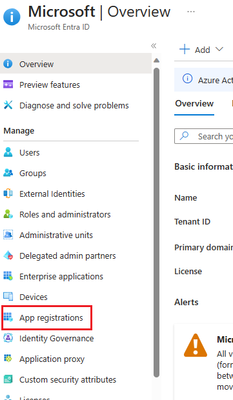
- Go to the Microsoft Entra ID -> App registrations -> New registration (Skip this one if you already has an app registration can be used to assign the authorize)
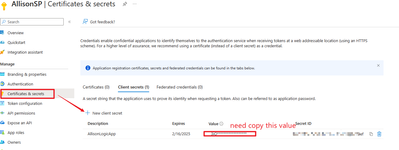
2. In the new registration, create a 'certificates& secrets'(If you already has one and remember the vaule, you can skip this one). Copy the value as it only will appear once when it created.
3. Go to the subscription and give this app registration the authorization.
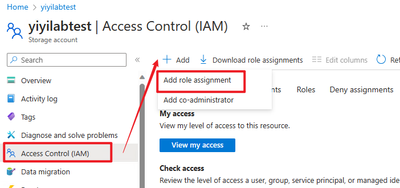
Open 'Subscription' -> open your recourse subscription -> Access control (IAM)
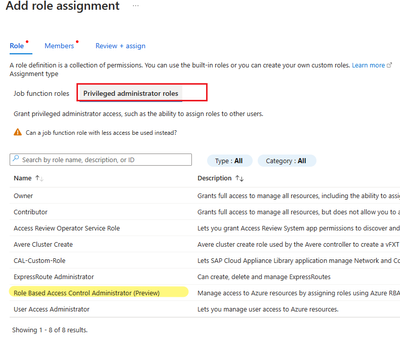
4. Give 'Privileged administrator roles' -> 'RBAC administrator'
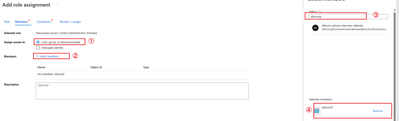
Click select and assign
5. Go to the azure apps page, for example, if you want to assign the storage account RBAC, then go to the your storage account, open the Access control, do the same step as 3-4
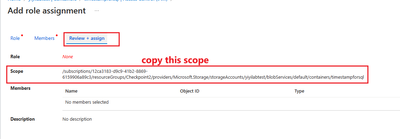
6. Get the scope for the storage account container, the quicker way is open the container folder, click access control, add role assignment, copy the scope
Then we already did prepare step. Create a logic app workflow
Step 3: Logic app design:
- Create a trigger as your need
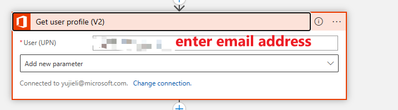
- Get the 'be assigned' user object id/principle id: office 365- get user profile:
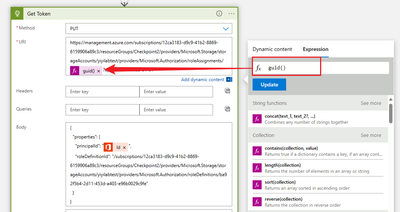
3. According to the document, fill the scope and role definition id from the previous step. The Role assignment id can be created via 'Guid' expression
Reference: Assign Azure roles using the REST API - Azure RBAC | Microsoft Learn
Body part:
{
"properties": {
"roleDefinitionId": "/{scope}/providers/Microsoft.Authorization/roleDefinitions/{roleDefinitionId}",
"principalId": "{principalId}"
}
}
4. Create a 'http' action: use 'put' method, fill the url and body,
5. click add new parameter -> Authentication -> Choose Active Directory Oauth
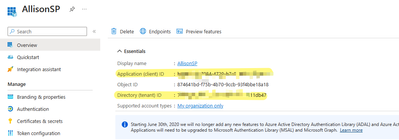
Go to the App registration, and copy the Tenant, client id and value(this is the value you copied when the client secrets created. )
Save the logic app and now you can run the logic app and test