This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
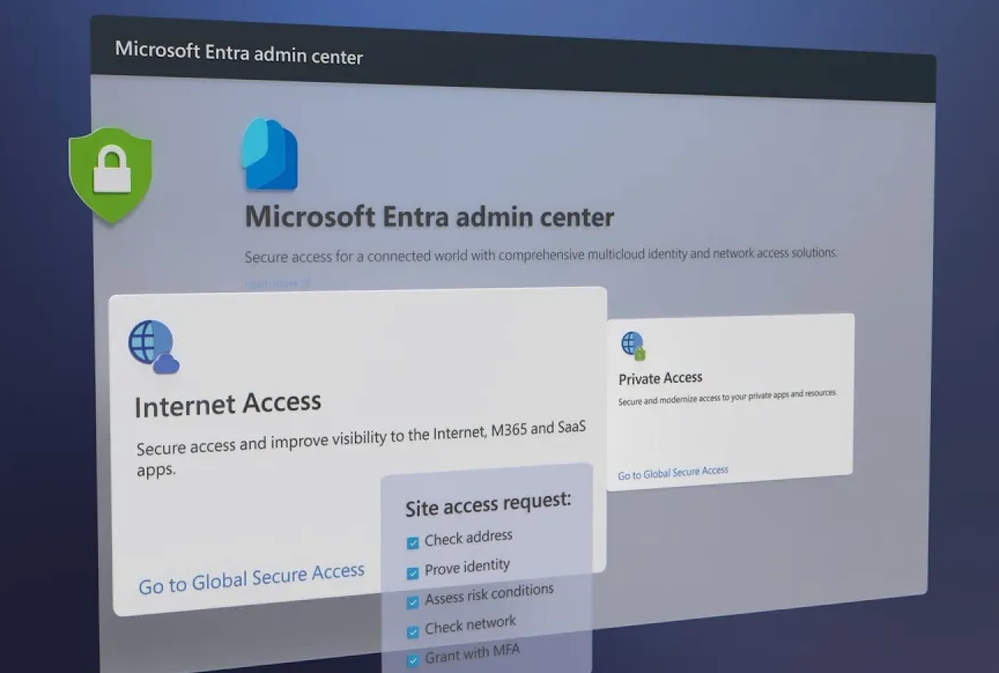
Keep your users, devices and data protected with Microsoft Internet Access. Combine identity and access management along with network access controls to help protect iInternet-based resources. Protections are context aware, made possible by deep integration with Conditional Access policies, with risk assessed in real time across identity, device, location, and applications, to protect ANY app or resource. See how Microsoft Entra Internet Access helps prevent sophisticated token theft attacks and insider data exfiltration to untrusted sites, including logging into unallowed sites that might increase your risk.
Camila Martins, Senior Product Manager for Microsoft Entra, shows policies you can set as an admin and the user experience with protections in place.
Manage identity and network access controls in one place.
Check out Microsoft Entra Internet Access.
Protect against data exfiltration.
Enable Universal Tenant Restriction across all managed devices with Microsoft Entra Internet Access. See it here.
Block internet sites that inhibit productivity.
Restrict end user access to unsafe or non-compliant content. Check out Microsoft Entra Internet Access.
Watch our video here:
QUICK LINKS:
00:00 — Keep users, devices, and data protected
01:20 — Token theft demo
02:09 — How it works as a user
03:00 — How the policy prevents data exfiltration
03:48 — Protect against malicious insider attacks
05:00 — See a policy in action
06:01 — Block sites that inhibit productivity
06:53 — Add Conditional Access policies
08:24 — Wrap up
Link References
Get started at https://entra.microsoft.com
For more information, check out https://aka.ms/SSEInternetAccessdocs
Check out our playlist at https://aka.ms/SSEMechanics
Unfamiliar with Microsoft Mechanics?
As Microsoft’s official video series for IT, you can watch and share valuable content and demos of current and upcoming tech from the people who build it at Microsoft.
- Subscribe to our YouTube: https://www.youtube.com/c/MicrosoftMechanicsSeries
- Talk with other IT Pros, join us on the Microsoft Tech Community: https://techcommunity.microsoft.com/t5/microsoft-mechanics-blog/bg-p/MicrosoftMechanicsBlog
- Watch or listen from anywhere, subscribe to our podcast: https://microsoftmechanics.libsyn.com/podcast
Keep getting this insider knowledge, join us on social:
- Follow us on Twitter: https://twitter.com/MSFTMechanics
- Share knowledge on LinkedIn: https://www.linkedin.com/company/microsoft-mechanics/
- Enjoy us on Instagram: https://www.instagram.com/msftmechanics/
- Loosen up with us on TikTok: https://www.tiktok.com/@msftmechanics
Video Transcript:
-As more of us work between both our home and office networks, the risk of cyber attacks is rising. And with that, the protection you may have in place need to expand to any network while ensuring the accessing party is in fact who they claim to be.
-In other words, we need a better way to combine identity and access management along with network access controls. And that’s where our Internet Access and Private Access solutions, part of Microsoft Entra, come in.
-Together, they form a Security Service Edge layer of defense that helps protect your internet-based resources, as well as resources running in your private cloud or on-premises infrastructure. Importantly, protections are context-aware, made possible by deep integration with Conditional Access policies, with risk assessed in real time across identity, device, location, and applications to protect any app or resource.
-And today, our focus on real attack scenarios is starting with Microsoft Entra Internet Access and how it helps prevent sophisticated token theft attacks, insider data exfiltration to untrusted sites, including logging into unallowed sites that might increase your risk. For each, I’ll show you the policies you can set as an admin and the experience as a user with the protections in place.
-Let’s start with the token theft use case. I’m in the Microsoft Entra admin center. And as a prerequisite, you’ll need to enable Adaptive Access signaling in Global Secure Access, under Global Settings, Session Management. This step enables a pre-configured, named location for use with your Conditional Access settings. Next, I’ll open a Conditional Access policy that I’ve already started creating.
-This is a policy scoped for SharePoint Online, which blocks access unless the user is connecting from an Entra Internet Access-enabled device and network specific to your tenant. In the Locations under Condition and in the Exclude tab, I’ve chosen the Compliant Network option.
-And notice that under Grant for access controls, I’ve selected Block if those conditions are not met. So now, let’s see how this works in action as a user. In my case, I’m working on a confidential design project with sensitive design files. I use Microsoft 365 apps, as well as other apps from Adobe’s Creative Cloud.
-In this case, I’m just browsing the web and this link takes me to a location in a SharePoint site. Pretty normal-looking stuff so far. But if I open this link, it’s actually masking a more sophisticated adversary in the middle attack. An attack like this often uses a legitimate-looking phishing site in the middle to lure the user to sign in.
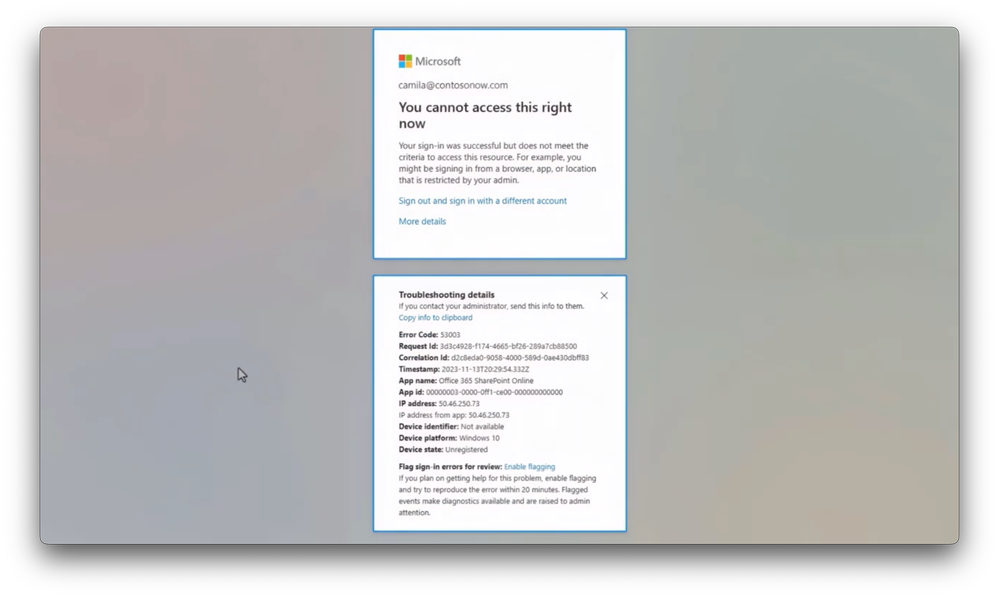
-This way, the adversary can compromise or steal the user’s authentication and active session tokens to hijack the signed-in session, which in turn allows them to access resources until the resource or an application requires re-authentication. In fact, let’s switch to the point of view of the adversary and show you how our policy to prevent data exfiltration via token theft works.
-And notice, despite having both authentication and active session tokens, when the adversary tries to connect to SharePoint Online, because the Compliant Network check is getting enforced for both the SharePoint data path as well as the Entra ID authentication path, their access is blocked.
-They are now stopped in their tracks because there’s no means for them to replicate the Compliant Network check for this tenant. This is a powerful example of how deep integration between identity, network security policies, and network compliance checks lead to faster and increased policy enforcement against sophisticated attacks.
-That said, what if the adversary is a malicious insider and they try an anonymous access or token replay attack to exfiltrate data from resources? An attack like this can work by using foreign identities to access cloud apps in external tenants. And we have a number of policies that can prevent it.
-I’m back in the Microsoft Entra Admin Center. In Identity, under External Identities, Cross-tenant access settings, you’ll see Tenant Restrictions for External users and groups, as well as External applications. And here, I’ll open the default Universal Tenant Restriction policy.
-This ensures that data is not exfiltrated to personal accounts or external organization sites that are not explicitly allowed. And this also applies to websites that do not require user authentication and allow anonymous access. And even with these default blocks in place, we can still allow users to collaborate with partner organizations using authorized external identities, as you can see here in the organizational setting step.
-For your Microsoft 365 apps, these policies protect against anonymous access or token replay attacks on all OS and browser platforms. Let me show you the policy in action. In this case, I am using a computer that Contoso provided for me as an external contractor. So it has all of the rights management and policy controls applied.
-I’m logged in as an external contractor from a design studio with access to Contoso’s network and resources so that I can collaborate and work with their staff on projects. Let’s say I want to share a sample of the work I’ve done on the sensitive project for Contoso on my company’s design studio domain.
-Here, I’ll log into my external domain using my design studio credentials and I’m blocked. And if I try to go to an unauthenticated, anonymous drop folder using an Anyone link in our SharePoint, I’m blocked there too. Again, that’s because based on the policy set as an external contractor, in both cases I am only allowed to collaborate on files within a defined Microsoft 365 tenant, in this case Contoso’s tenant, which stops me from sharing the data outside of that tenant.
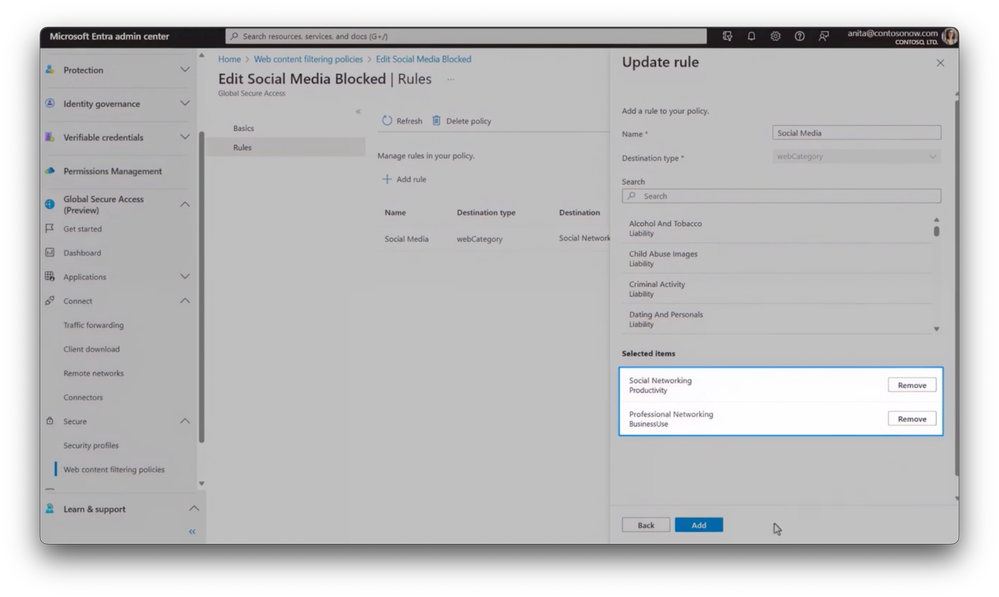
-Next, let me show you another application of Microsoft Entra Internet Access, which can also filter unsanctioned web content and block sites based on their domains, as well as user roles. Beyond preventing security events, this can also be a way of blocking sites that may have a negative impact on productivity. Here, I’m in the Connect tab and traffic forwarding profiles. I’ve enabled the Internet access profile.
-And doing so routes client Internet traffic to the global Secure Access proxy where policy can be enforced. Next, I’ll go to the Web content filtering policies under Secure and open Social Media Blocked. And inside this policy, you’ll see the two categories that I’ve selected with social networking and professional networking, along with additional options above those for other categories I can restrict.
-Let’s try something else. I’ll add a condition to block sites that inhibit productivity for all employee roles who are not in marketing. To do that, you can configure a Security Profile and link it to a Conditional Access policy. For example, in Secure, under Security Profiles, we’ve created a profile.
-And I’ve linked two policies, one allowing access to LinkedIn at a priority level 100 and then another one that blocks all productivity-inhibiting sites at a lower priority. Then, I’ve created a matching Conditional Access policy. This will enforce the Security profile I just created with all users in scope, except this group exclusion for the marketing roles. So you can apply policies with rich conditions.
-I’ll choose the target resource as the new Internet traffic profile from before. And from here, I can add any additional conditions or settings that I want. Then, in Session controls, this is where you select the Security Profile you want. And here, you can see that I’ve chosen the profile for blocking non-productive locations.
-With that, let’s look at what happens when someone not in the marketing group now attempts access. And as you can see, they’re blocked from social media sites like Twitter or X but they can access linkedin.com. Again, because our policy is set to allow and this web destination has a higher priority. And coming soon, Security profiles will contain other types of policies including threat intelligence-based filtering, cloud firewall, and more.
-So that was an overview of how Microsoft Entra adds Security Service Edge controls for internet connections to keep your users, devices, and data protected. You can get started with everything I showed today at entra.microsoft.com. By configuring these controls to work alongside the tools you have in place today, you’ll be able to rapidly and seamlessly protect your Microsoft 365 apps and internet traffic.
-To learn more, check out aka.ms/SSEInternetAccessdocs. Part two on Security Service Edge with Microsoft Entra Private Access will be available on our playlist at aka.ms/SSEMechanics. Hit subscribe to Microsoft Mechanics if you haven’t already and thanks for watching.