This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
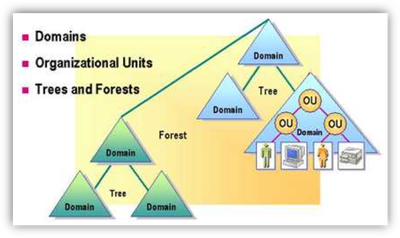
Greetings! Before the cloud, when on-prem Active Directory was the hub of many enterprise architectures, business needs often drove the requirement to expand single-domain AD forests into multi-domain AD forests. Even in the NT days, one might have 'Account Domains' and 'Resource Domains' - connected via one-ways trusts. As was often the case, multiple existing NT 4.0 domains were 'upgraded' into a single AD forest, as additional domains. These days, a single-domain AD Forest is pretty rare for main-stream use.
Over time, mergers and acquisitions, divestitures, compliance requirements, and other changes often saw AD forests stitched together into multi-forest AD environments. One might have an "Exchange Forest," just for email. There might be an "Administration Forest" where highly privileged accounts lived and operated from. The requirements for multiple AD domains and forests drove the need for expanded technical capabilities, such as new kinds of trusts - and new functionality between/across those trusts. Trusting and trusted domains and forests, one-way, two-way, external, short-cut trusts, forest, transitive trusts - and the authentication levels allowed across them - all came to Active Directory over time.
- Here’s a throw-back image from our old Directory Services course with forest and domain triangles, trusts, etc. Anyone else remember those huge “Microsoft Official Curriculum” (MOC) 3-ring binders that were often 2-3 inches thick? They were awkward to carry but I learned SOOO much from those materials/courses back then.
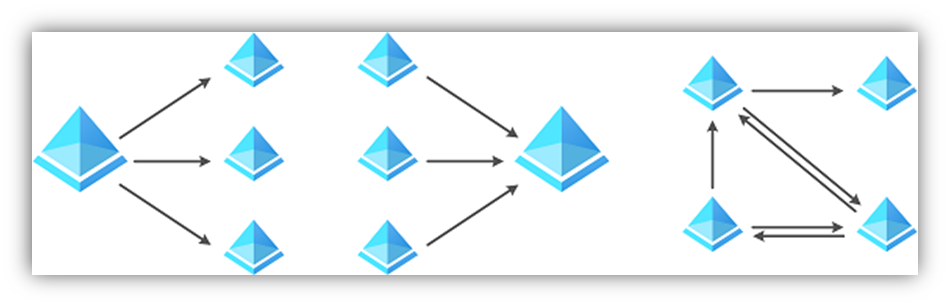
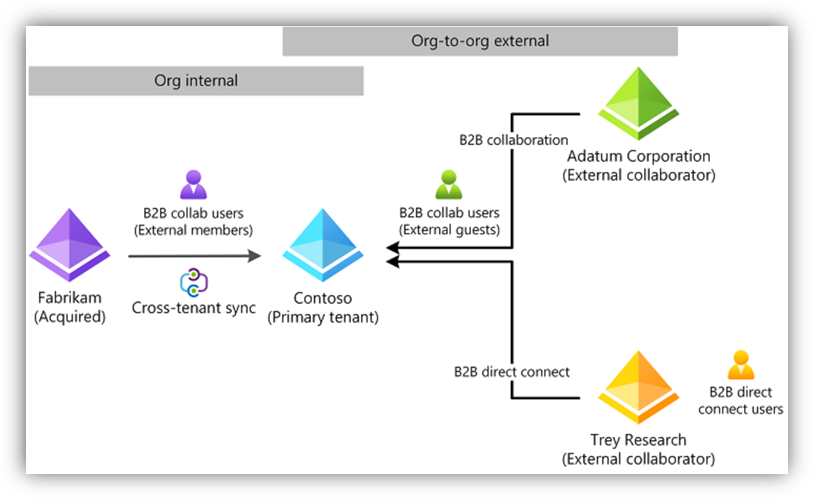
And so, it follows in the cloud – where we sometimes see single-tenant O365 orgs suffer 'growing pains' due to the need for better multi-tenant collaboration, service insulation/isolation, access control, delegation models, etc. Initially, we had only B2B (which is still there) but we continue to deliver more and more expanded functionality between/across tenants for complex scenarios. Now, you can 'join' tenants into collections via hub-and-spoke or full-mesh designs, sync users into other tenants, disable the invite redemption process and associated permissions-consent pop-ups, etc. All of it configured and controlled via policy.
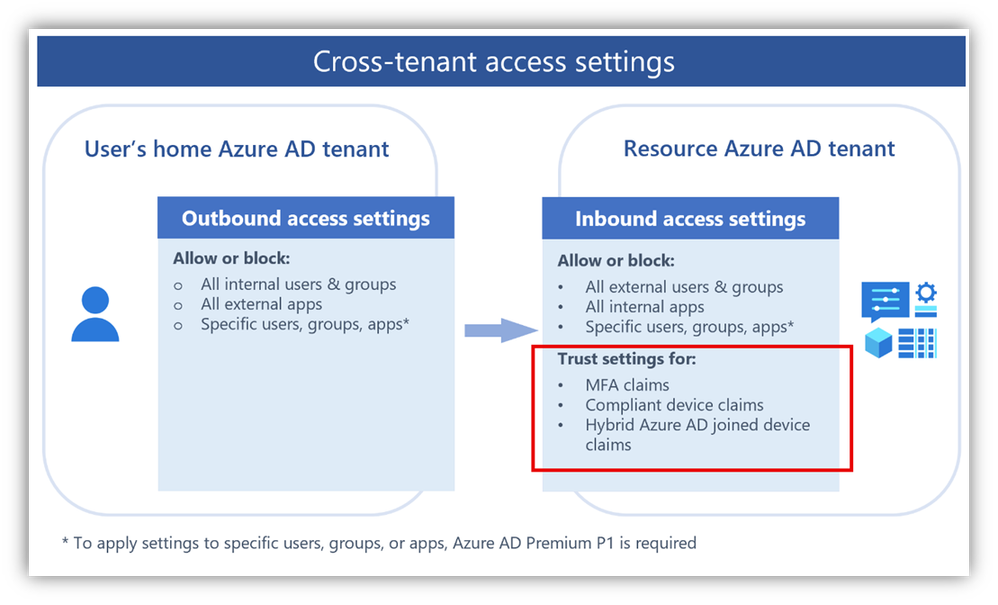
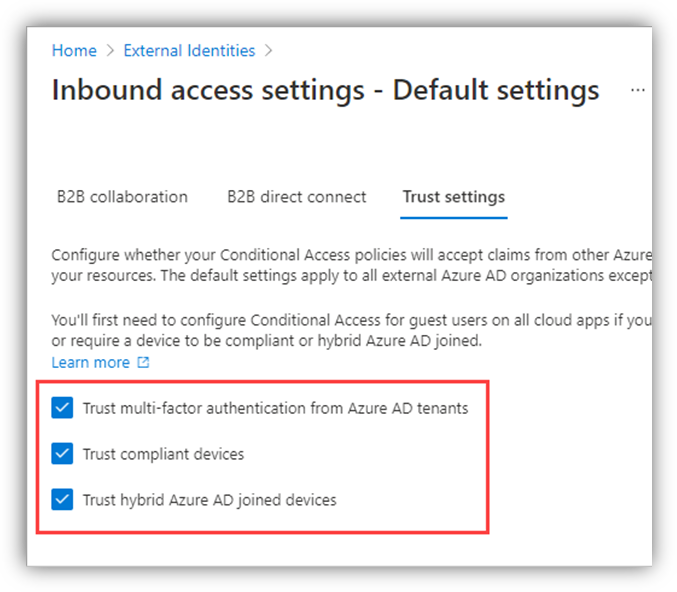
Notice the 'Trust settings' in the red boxes below. There has been a long-standing ask to accept Conditional Access claims from devices in other tenants. Well, now you can. This is something you might not want to allow for an external partner - but you might. And now, you can. Or, if the 'external' tenant is now yours (say, through an acquisition), this capability can make a world of difference in secure collaboration, very quickly.
As someone who frequently works with complex enterprise orgs who run into the need for these capabilities, this is great news.
Now, of course, this is cloud. So, we're talking web-based authentication and authorization protocols vs kerberos or NTLM. Web-service endpoints, not internal DNS SRV records or DCLocator processes. It's not an exact 'like-for-like' to Active Directory trust models but in concept, it's very similar. Heck, we even re-used the triangles. ![]()
A series recap (so far):
- The Twelve Days of Blog-mas: No.1 - A Creative Use for Intune Remediations - Microsoft Community Hub
- The Twelve Days of Blog-mas: No.2 - Windows Web Sign in and Passwordless - Microsoft Community Hub
- The Twelve Days of Blog-mas: No.3 - Windows Local Admin Password Solution (LAPS) - Microsoft Communi...
- The Twelve Days of Blog-mas: No.4 - Sync Cloud Groups from AAD/Entra ID back to Active Directory - M...
- The Twelve Days of Blog-mas: No.5 - The Endpoint Management Jigsaw - Microsoft Community Hub
- The Twelve Days of Blog-mas: No.6 - The Reporting Edition - Microsoft Community Hub
- The Twelve Days of Blog-mas: No.7 - Architecture Visuals - for Your Reference or Your Own Docs - Mic...
- The Twelve Days of Blog-mas: No.8 - The Evolution of Windows Server Management - Microsoft Community Hub
See you soon ...
Hilde