This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Sentinel Basics
You want to get started with Microsoft Sentinel but it looks overwhelming to you.
Here are some simple guidelines to follow for a very basic outline for you to get started with Microsoft Sentinel:
- Sentinel setup and prereqs ---Start here Player One
- Sentinel Permissions---------- What is your character/avatar and role
- Power UP/use AI+ML----------Enable User and Entity Behavior Analytics (UEBA)
- Where Data ------------------- What is your playing field (log analytics workspace)
- Keep Data --------------------- How long do you want to keep data
- How Data ----------------------What data do you want and how will you connect to data that you want to ingest (Connectors/Custom data connectors); including free
- Detect Threats in Data --------Automatically detect threats with Analytic RULES
- See/Visualize Data ------------Visualize data with workbooks
- Alert on Data-------------------Visualize incidents
- Prevent/Threat Hunt in Data---Be Proactive
- Automate Responses ----------SOAR to the highest with automation
- Deploy Solutions --------------like M2131, ZeroTrust, CMMC2.0, NIST 800-53
For more in-depth information, please check out the Sentinel Deployment planning guide.
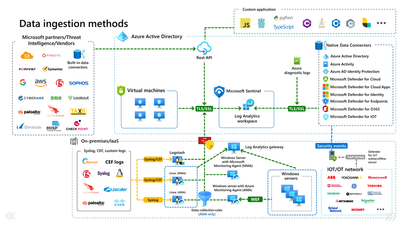
For a visual representation of Data flow from data sources and into Sentinel: