This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
We are pleased to announce Microsoft Defender Threat Intelligence (MDTI)’s powerful new integration with Silobreaker. Silobreaker produces a reputation score for indicators of compromise (IOCs) based on a variety of open and commercial intelligence sources. Silobreaker users can now also access MDTI’s rich reputation scoring against IOCs, specifically IP addresses and domains, using Silobreaker’s 360 Search. MDTI’s reputation feature combines the power of its raw and finished threat intelligence, which tap into more than 65 trillion daily threat signals, machine learning algorithms, and over 8,500 cybersecurity researchers to calculate if an indicator is malicious or benign. If you’re a Silobreaker user and have an MDTI Premium and API subscription, you can begin taking advantage of this integration today.
Navigating Silobreaker's 360 Search
Figure 1 – Searching an IP address returns MDTI’s reputation data. Results displayed in Silobreaker’s Enrichment module.
Note: Users can hover over and select the blue text values to perform the relevant entity search within Silobreaker.
Figure 2 – Prompt box displayed with Severity, Description, and More information is a result from selecting an (i) within the Triggered reputation rules section.
Figure 3 – Full display of Silobreaker’s UI. Enrichment module visible on the right-side pane.
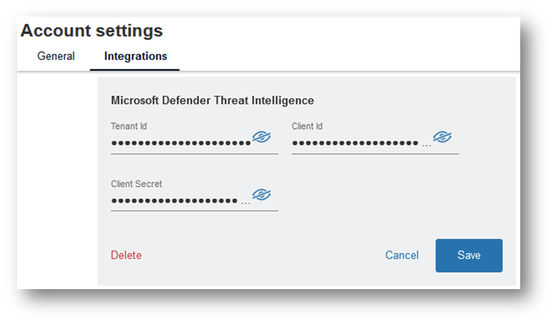
Connecting Your MDTI Credentials
For Silobreaker users with an MDTI Premium and API subscription, setup is easy. Just enter your Microsoft Tenant ID, Client ID, and Client Secret associated with your Azure MDTI application in Silobreaker’s Account Settings > Integrations page. And if you haven’t yet set up an Azure Application to configure your MDTI credentials, please reference our MDTI API blog for details.
Silobreaker Use Cases
Many organizations use Silobreaker to aggregate both raw and finished cyber threat intelligence from a variety of commercial and open-source intelligence providers to lessen the burden on security teams by eliminating the need for creating custom threat intelligence reports and setting up the ingestion of finished and IOC feeds. With the addition of MDTI intelligence, Silobreaker and Microsoft customers can enhance their security operations with the context and visibility made possible by Microsoft’s massive telemetry.
Don’t have MDTI Premium and the API license? Please reference our Getting Started with MDTI blog for details regarding setting up your MDTI Premium and API trial.
We Want to Hear from You!
Be sure to join our fast-growing community of security pros and experts to provide product feedback and suggestions. Let us know how MDTI is helping your team stay on top of threats. With an open dialogue, we can create a safer internet together. Learn more about MDTI.