This post has been republished via RSS; it originally appeared at: ITOps Talk Blog articles.
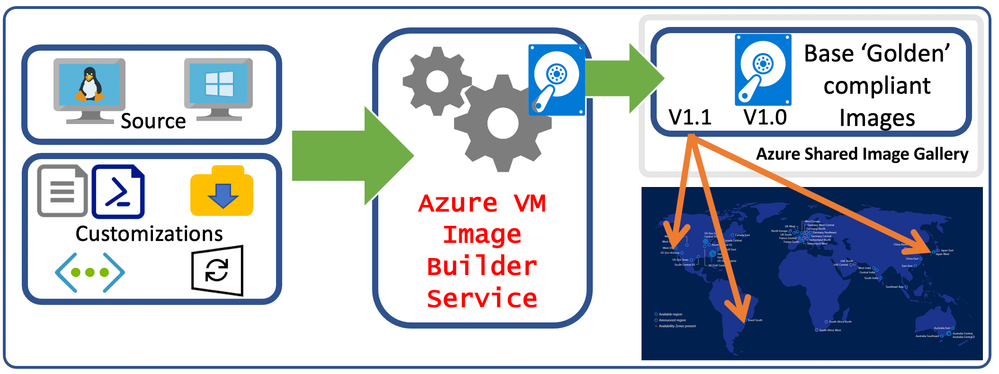
You might be familiar with building golden images or templates for use on-premises. Back in the olden days we used to "ghost" machines and now you may use a VM template with sysprep. Azure offers the managed service Azure Image Builder so you can configure your image as a template for reuse within your cloud. Golden or base images are usually built upon governance, standards and best practices within your organization. These images especially come into play if you have immutable infrastructure, servers or virtual machines that will not be modified after deployment. To ensure consistency and speed up deployment, you can create golden images or templates.
Azure Image Builder lets you transfer your image customization pipeline to Azure without changing your scripts, commands, and processes. VM Image Builder works with any base operating system image from the Azure Marketplace and uses an automation config for the build process. Your VM image build artifacts are stored as Azure resources. This feature eliminates the need for offline definitions and the risk of environment drifts due to accidental deletions or updates.
Side note - Azure Image Builder is based on Packer, so you can reuse your existing Packer shell provisioner scripts with it.
Scenarios
- Build, tailor and update "Base" virtual machine images and distribute them globally.
- Image creation for Azure Virtual Desktop.
- Access files in an Azure storage account or scripts from GitHub
- Have your build pipeline trigger automatic image creation based on specific criteria.
- Create images for both Azure and Azure Stack.
- Integrate with existing build pipelines using Azure VM Image Builder DevOps Task.
- Optimize Windows and Linux VM images.
- Deploy your image building pipeline on Azure faster by connecting to existing virtual networks that have configuration servers (DSC, Puppet, Chef), file shares, or any other servers or services that can be routed.
Many of these scenarios have code and quickstarts to get you going on the AZ VM Image builder Github repository.
I encourage you to check it out and you can contribute as well.
What's New
Auto-Image Creation, also known as “triggers”, is a feature that enhances developer productivity by automatically initiating image builds for new base images. This feature allows customers to streamline their image building process by setting up ‘triggers’ for the images they want to update automatically. Azure Image Builder also helps internal teams to ensure the security of their images through automation, reducing the manual work required to patch 1P images.
Isolated Image Builds. A feature of Azure Image Builder (AIB) is the ability to customize and validate VM images using dedicated Azure Container Instances (ACI) resources in your subscription. This provides compute and network isolation from shared infrastructure.
Azure VM Image Builder service DevOps task (preview). Create a virtual machine (VM) image with your application and operating system installed and configured, using the build artifacts.
Azure Portal. Users have been using CLI/PowerShell to create Azure Image templates but now that availability is in the Azure Portal.
The Azure Image Builder portal functionality allows the customer to explore the features of Azure Image Builder easily, without spending time on learning how to make a JSON template from the documentation. You can create an Azure Image from Bicep or an ARM template using JSON
Getting Started
Permissions
No matter which route you take, using the Portal or using command line you have to grant permissions for the service to work. The VM Image Builder service needs permissions to create, manage, and delete a staging resource group, which has the prefix IT_*. This resource group contains any resources that the image build requires. You can add these resources after you register for the service successfully. The service creates a service principal name in your subscription when you register.
To distribute images to either the managed images or Compute Gallery, you must create an Azure user-assigned identity that can read and write images. To access Azure Storage, you need permissions to read both private and public containers.
Register providers
If you haven't already done so, register the following resource providers to use with your Azure subscription:
- Microsoft.Compute
- Microsoft.KeyVault
- Microsoft.Storage
- Microsoft.Network
- Microsoft.VirtualMachineImages
- Microsoft.ManagedIdentity
- Microsoft.ContainerInstance
I'll go over registering the providers and granting permissions in this first video below.
PowerShell Scripts I used:
In the next post we will go over using the Azure portal to build a golden image and build from it.
Thanks for reading and feel free to comment with any questions.
Amy Colyer
