This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Introduction
Mobile devices are increasingly targeted by cyberattacks that can compromise your data, privacy, and productivity. To protect your devices from these threats, you need a Mobile Threat Defense (MTD) solution that can detect and respond to malicious activities on your device and network.
Microsoft Defender for Endpoint is a unified endpoint security platform that provides comprehensive protection for your devices, including Windows, macOS, Linux, iOS, and Android. It leverages cloud-powered intelligence, behavioral analysis, and machine learning to detect and block advanced threats, phishing, malware, and ransomware. It also integrates with Microsoft 365 Defender to provide cross-domain visibility and coordinated response across your Microsoft 365 environment.
In this blog post, you will learn how to protect unmanaged (personal) or 3rd party MDM managed iOS and Android devices with Microsoft Defender for Endpoint as your MTD. The solution leverages Intune’s App Protection Policies aka MAM to enforce Device Protection with MDE regardless of the device enrollment state.
If you need help with MDE enrollment of your Intune Managed iOS/iPadOS devices, you can check out my earlier posts here where I discussed about Zero Touch enrollment and User Enrollment methods.
Prerequisites
To use Microsoft Defender for Endpoint as an MTD solution for your iOS and Android devices, you need to meet the following requirements:
- An Intune and Defender licensed user.
- Broker App for App Protection Policies, which can be either:
- Company Portal App (iOS and Android).
OR
-
- MS Authenticator App (Only iOS/iPadOS)
The Broker App you choose above acts as an intermediary between the Intune service, the managed app, and the device. Its primary function is to securely facilitate communication and enforce policies. For more details around this workflow, refer this learn docs.
- An Intune supported iOS or Android Device
Enable Connector Integrations
Assuming you have already enabled MDE Integration with Intune, the next steps involve ensuring that the App Protection Policy Evaluation is honored and enabled within MDE connector.
To make this change from the Intune console, your account needs permissions equal to the Endpoint Security Manager built-in Role Based Access Control (RBAC) role.
- Refer the screenshot below to ensure the toggles for evaluating App Protection Policy are set to On for the desired OS platforms.
Configure App Protection Policy
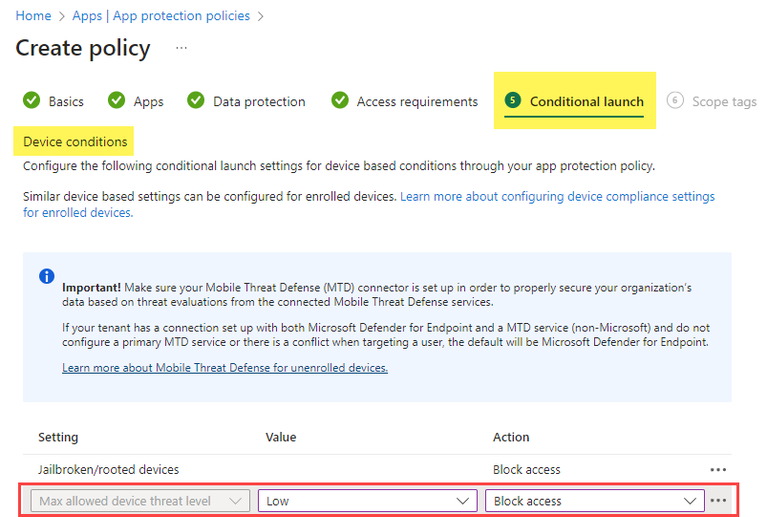
Create a new App Protection Policy or customize an existing one to configure Max allowed device threat level under Conditional Launch.
- From the Intune Console Select Apps > App protection Policies.
- Select Create policy and select the platform of the device for your policy.
- Select Configure required settings to see the list of settings available to be configured for the policy.
- By scrolling down in the Settings pane, you view a section titled Conditional launch with an editable table.
- Under Device conditions choose Max allowed device threat level with a desired Value and Action.
- Assign the policy to the target set of users group.
MDE Onboarding Experience
When the users launch an app protected with App Protection Policy, the Broker App which can be the Microsoft Authenticator for iOS, or Microsoft Company portal for Android devices performs a Conditional launch check against the specified Device conditions from policy above.
A VPN (Virtual Private Network) is created on the device by MDE for the Web Protection feature. This is not a regular VPN and is a local/self-looping VPN that does not take traffic outside the device.
Here's a walkthrough of the onboarding experience on an iOS/iPadOS device in the GIF below:
- End user launches MS Outlook App
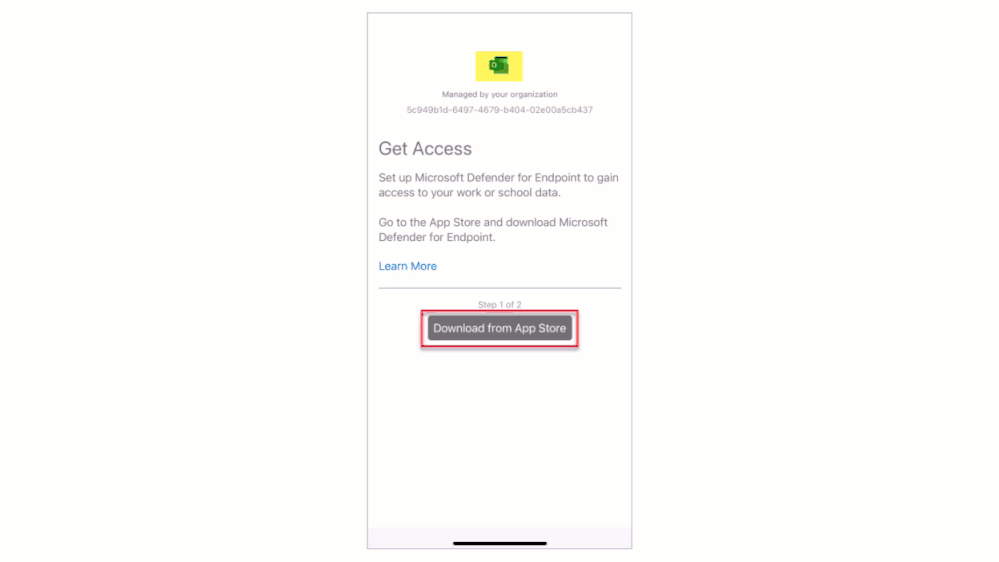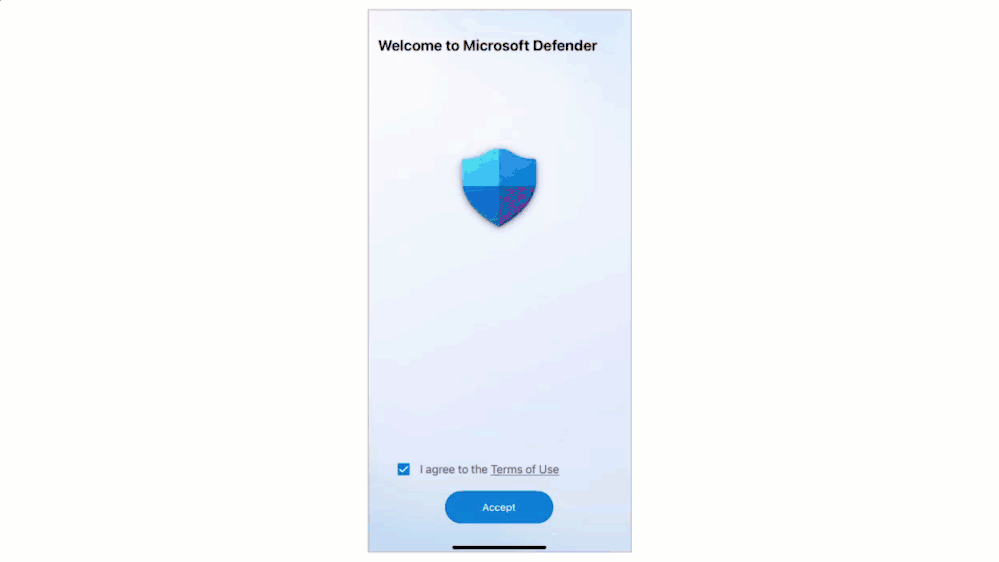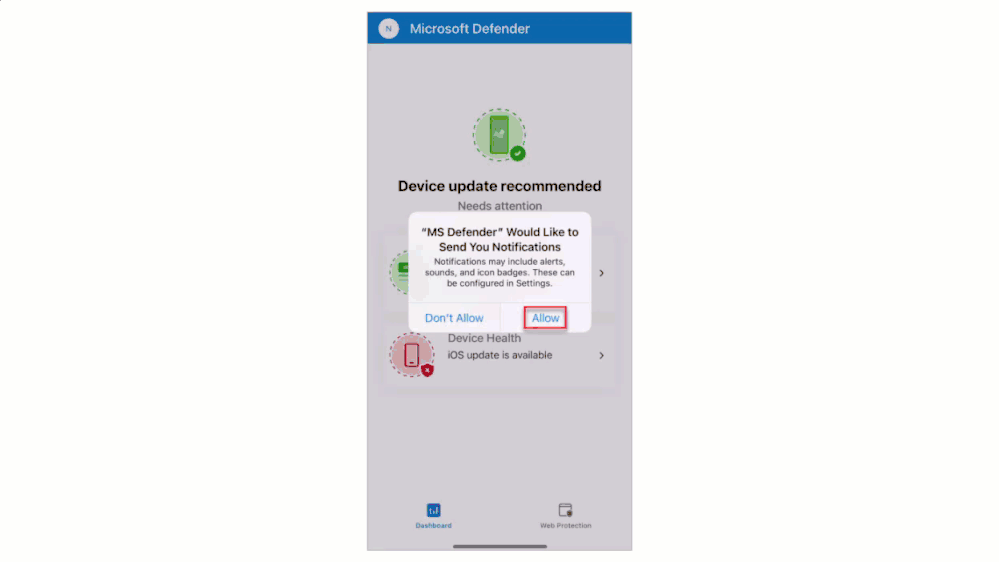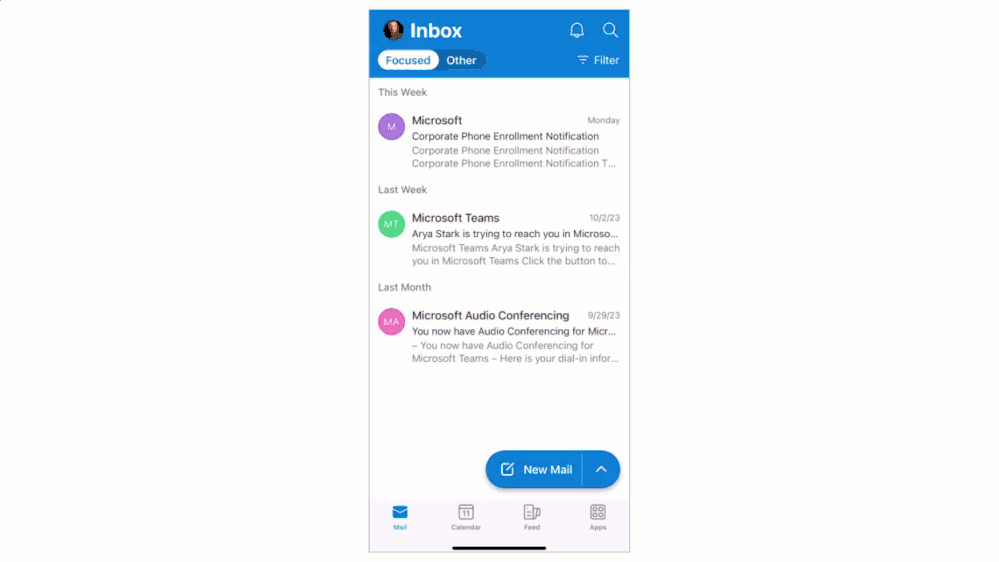
- App Protection Policy kicks in to check the device health however the MS Defender App is missing.
- Next the MS Defender App is downloaded and installed by the user from the public app store.
- The user sign’s in and accepts the EULA.
- The user approves the creation of a local VPN and an App notification for configurations.
- Another “recheck” of the Conditional launch condition restores access to the corporate emails.
Next, let’s take a walkthrough of the onboarding experience on an Android device where we launch Outlook for the first time in the GIF below:
- End user launch MS Outlook App to add their corp. email account.
- App Protection Policies kick in prompting to install the broker app Intune Company Portal from the public store.
- It immediately detects Microsoft Defender for Endpoint App missing and prompts user to install the app.
- The user needs to launch the MDE app to complete the onboarding.
- The next sets of prompts include accepting the EULA followed by required permissions to protect the device & creates a local VPN.
- Once the device is healthy, access to corp. emails via Outlook is granted.
MDE Device Protection
Microsoft Defender for Endpoint provides real-time protection for your iOS and Android devices by monitoring the network traffic, web browsing, and app behavior on your device. It can detect and block malicious or risky activities, such as:
- Malware or ransomware downloads that try to infect your device or encrypt your files.
- Unsecure or compromised network connections that try to intercept or modify your data.
- Unwanted or malicious apps that try to access your device features or data.
- Phishing attempts that try to steal your credentials or personal information.
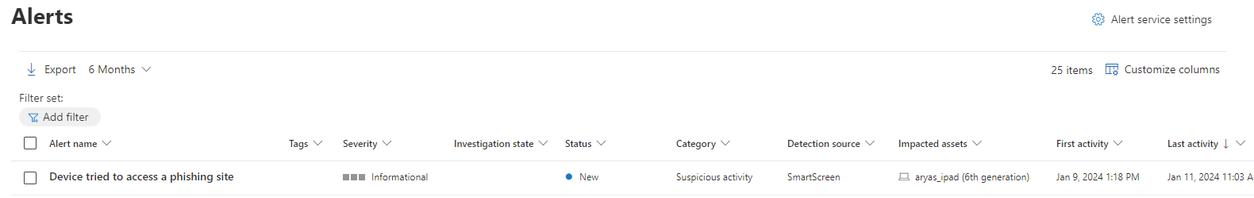
When Microsoft Defender for Endpoint detects a threat on your device, it will alert you and provide you with guidance on how to resolve the issue. You can also view the details of the alert and the device status on the Microsoft Defender Security Center portal.
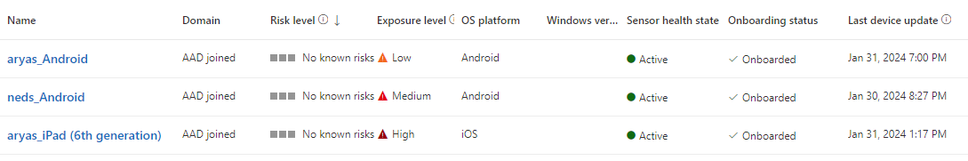
The device name in Defender for Endpoint portal is of the format <username_OS>. You can also use Microsoft Entra device ID to identify the device.
- To generate an alert, browse a test malicious site from the onboarded device which should be immediately blocked: https://smartscreentestratings2.net
Additional References
Use Intune MAM to Control Office Mobile Apps and Office 365 Content - Microsoft Community Hub
Thanks,
Arnab Mitra