This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Introduction
Always Encrypted is a feature of Azure SQL and SQL Server that allows you to encrypt sensitive data in your database. The data is never exposed in plaintext to the database engine, or anyone who has access to it.
However, Always Encrypted has some limitations. For example, you cannot perform any computations or operations on the encrypted data, such as sorting, filtering, or indexing. Secondly, an initial encryption must be done on the application side which can be time consuming on a large set of data.
That's where Always Encrypted with secure enclaves comes in. A secure enclave is a protected region of memory within the SQL database engine process. It acts as a trusted execution environment for processing sensitive data inside the database engine. Always Encrypted with secure enclaves provides two key benefits:
- Rich confidential queries, including pattern matching (LIKE) and range comparisons. These capabilities make it possible to protect a much broader set of sensitive information (names, address, phone numbers, sensitive numerical data) without painful compromises.
- In-place encryption – allowing cryptographic operations inside the secure enclave, to eliminate the need to move the data outside of the database for initial encryption or key rotation.
In this blog post, we will show you how to convert your existing database that uses Always Encrypted to Always Encrypted with secure enclaves. We will assume that you already have an Azure SQL Database or SQL Server database with Always Encrypted enabled, and that you have access to the encryption keys. If you don't, you can follow this tutorial to set up Always Encrypted first.
Enable a secure enclave
To enable your database with a secure enclave for Always Encrypted, you need to choose which type of enclave you want to use: Intel SGX or VBS. The choice between Intel SGX enclaves and VBS enclaves depends on your security requirements. Think about who you want to protect your data for. Do you want to protect your data from malicious insiders, or do you also want to protect your data from the host provider? If you need the highest level of security, you should use Intel SGX enclaves. More information can be found on Always Encrypted with secure enclaves - Intel SGX vs VBS.
Depending on your choice, you need to perform different steps to enable the enclave on your database. For Intel SGX to be available, the database must use the vCore model and DC-series hardware in Azure SQL Database. To enable a VBS enclave on your Azure SQL database, you need to set the preferredEnclaveType database property to VBS, which activates the VBS enclave for the database. This can be done using the Azure portal, SQL Server Management Studio, Azure PowerShell, or the Azure CLI.
Before you can use Always Encrypted with secure enclaves in SQL Server, you need to configure your instance to initialize the secure enclave during startup.
Convert existing keys to enclave enabled keys – key rotation
After enabling the enclave on your Azure SQL database or SQL Server, you need to convert your existing column master keys to be enclave-enabled. This involves rotating the keys. Follow the steps below to perform key rotation:
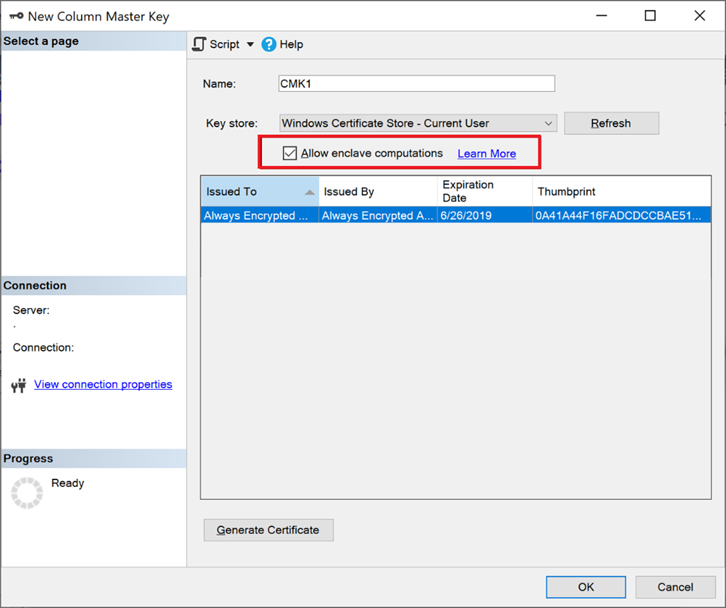
- Provision a new enclave-enclave enabled column master key, see Provision enclave-enabled keys. Make sure you select Allow enclave computations.
- Replace an existing key with the new key, see Rotate Always Encrypted keys using SQL Server Management Studio and Rotate Always Encrypted keys using PowerShell.
Change your application
Finally, you need to upgrade the driver and the connection string on your application to support enclave computations. The following tables summarizes the required .NET platforms and drivers to use Always Encrypted with secure enclaves.
|
Support Always Encrypted |
Support Always Encrypted with secure enclaves |
Target Framework |
Microsoft.Data.SqlClient Version |
Operating System |
|
Yes |
Yes |
. NET Framework 4.6+ |
1.1.0+ |
Windows |
|
Yes |
Yes |
.NET Core 2.1+ |
2.1.0+ |
Windows, Linux, macOS |
|
Yes |
No |
.NET Standard 2.0 |
2.1.0+ |
Windows, Linux, macOS |
|
Yes |
Yes |
.NET Standard 2.1+ |
2.1.0+ |
Windows, Linux, macOS |
|
Driver |
Always Encrypted |
Always Encrypted with secure enclaves |
|
ODBC |
13.1 |
17.4 If you do not require attestation - Version 18.1+ |
|
JDBC |
6.0 |
8.2 If you do not require attestation - Version 12.2+ |
|
PHP |
ODBC Driver version 17 |
ODBC Driver version 17.4 |
The connection string of your application will already have the parameter “Column Encryption Setting = enabled”. This will enable Always Encrypted for application queries. To enable enclave computations for a database connection, you must set the following connection string keywords, in addition to enabling Always Encrypted.
- Attestation Protocol – specifies the attestation protocol. If this keyword isn't specified, secure enclaves are disabled on the connection.
- Enclave Attestation URL - specifies an attestation URL (an attestation service endpoint). You need to obtain an attestation URL for your environment from your attestation service administrator.
Run rich confidential queries against encrypted columns
Congratulations! You have successfully converted your Always Encrypted database to Always Encrypted with secure enclaves. You can now enjoy the enhanced benefits like rich confidential queries on encrypted columns and in-place encryption.