This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Today we're announcing the general availability of the SIEM Migration experience in Microsoft Sentinel, that unlocks the capability to bring over your SIEM detections into Microsoft Sentinel. This is an initial step in the direction to help customers accelerate and simplify migrations to Microsoft Sentinel. Migrating a SIEM solution is often complex, resource-intensive, and expensive and current processes in this space are manual and arduous.
The experience supports SIEM migrations from Splunk to Microsoft Sentinel. The migration experience is compatible with both Splunk Enterprise and Splunk Cloud editions. At GA, this experience supports migration of Splunk detections to Microsoft Sentinel analytics rules with scope of simple, single table queries based on Splunk CIM. It includes capabilities to determine the level of migration success for each detection with a built-in editor to modify the query before bringing it over.
Get started with the SIEM migration experience
Prerequisites
As you prepare to migrate Splunk detections to Microsoft Sentinel you will need:
- A Splunk admin role to export all Splunk alerts to a JSON file from Splunk.
- This capability requires Microsoft Sentinel Contributor role. For more information, see Permissions in Microsoft Sentinel.
- Set up your data tables by installing and configuring necessary out-of-the-box (OOTB) data connectors and parsers from Microsoft Sentinel content hub for fulfilling data pre-requisites.
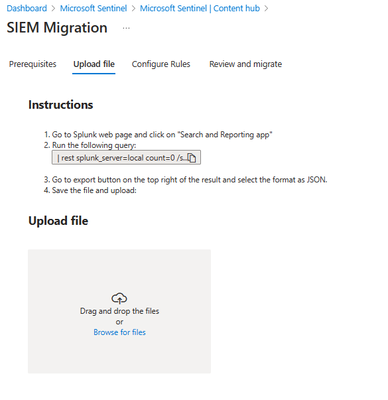
- Follow the steps listed in the learn documentation to prep and save your Splunk export file.
SIEM migration experience flow
- In the Microsoft Sentinel portal, select SIEM Migration under Content hub.
- Upload the exported Splunk JSON file.
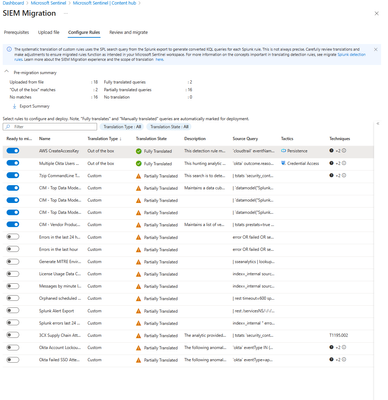
- Select Configure Rules to review the analysis of the export.
The analysis highlights the Translation State of the query translation from SPL to KQL. Splunk alerts can have any one of the following states:
- Fully Translated - These are rules with queries that were fully translated to Kusto.
- Partially Translated - All rules with queries that the migration experience has attempted to translate but couldn’t completely translate for any reason are tagged as Partially Translated.
- Not Translated – All Splunk alerts that had an error in translation are tagged as Not Translated.
- Manually Translated - If any Custom Fully/Partially/Not Translated rule is reviewed and saved, the translation state changes to Manually Translated.
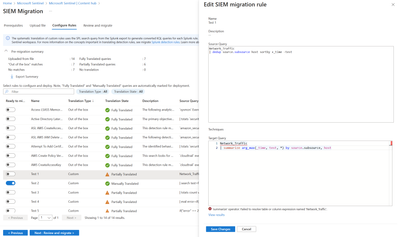
You can edit any of the partially translated or not translated rules to fix and include in the migration scope as illustrated below. The editor flags errors where fixes would be needed to get a functionally valid KQL. Over time we plan to expand translation coverage and success to reduce partially and not translated states and reduce toil.
- Toggle the “Ready to migrate” to Yes for all rules that must be in scope of migration & should be deployed as Microsoft Sentinel Analytics.
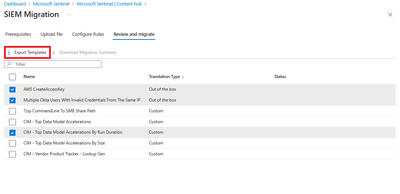
- When the review is complete, select Review and migrate.
- (Optional) Select and export the Analytics as ARM templates to plug these in your CI/CD or custom deployment processes.
- Click Deploy to deploy ALL the in-scope Splunk alerts as Microsoft Sentinel Analytics. The rules are installed in your active rules tab of Microsoft Sentinel Analytics experience. The rules are in disabled state and you can review, select and bulk enable them to start generating alerts.
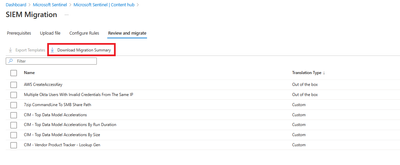
Download Migration Summary enables you to get a summary of the Analytics deployment.
We plan to continue to invest and evolve this migration experience with the following top priorities:
- Splunk Common Information Model (CIM) to Microsoft Sentinel's Advanced Security Information Model (ASIM) translation support.
- Support for Splunk macros.
- Support for Splunk lookups.
- Translation of complex correlation logic that queries and correlates events across multiple data sources.
Learn more
For more information on the migration experience and Microsoft Sentinel check out these resources: