This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
In the face of today's complex cybersecurity challenges, the ability to proactively manage and mitigate potential attack vectors has never been more crucial. Identifying, understanding, and countering attack paths effectively are essential steps in safeguarding an organization's digital assets. This Azure Workbook Attack Path Dashboard has been designed for monitoring attack paths over time—ranging from days to a month or more. This tool empowers organizations to leverage deep insights into their cybersecurity posture, enabling them to evaluate and enhance their processes for mitigating threats proactively. This blog article explores the dashboard’s layout, its detailed insights, and how it supports organizations in enhancing their security posture.
How Implement the Workbook - Requirements
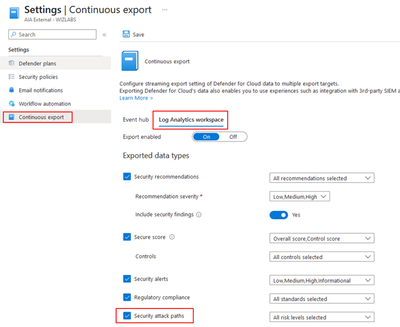
To implement the workbook you must enable Defender for Cloud Continuous Export feature at the Subscription level, select the export Security Attack Paths data and the Azure Log Analytics Workspace to store the data. The configuration is done through Defender for Cloud Environment Settings.
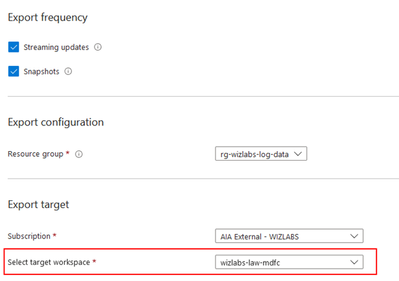
Here, select the Subscription and select Continuous Export. Configure the settings and save.
Note: Data exported to the Log Analytics Workspace is subject to the Workspace ingestion cost. Learn more about Log Analytics pricing and the many techniques to optimize your cost. Data retention is by default 31 days, however longer retention can be configured -90 days is recommended for an optimal time rage analysis (longer retention will incur additional charges as explained in Log Analytics pricing). Upon activation, the system will begin populating the designated Workspace with data as it updates the Attack Paths. This process is typically completed within 24 hours, at which point the initial data records will be visible.
Dashboard Layout and Insights
The Attack Path Dashboard features an intuitive layout design that makes monitoring and analyzing attack paths over time not just more manageable, but also more effective. This dashboard stands out not only for its user-friendly interface but for the insights it provides into the attack path over time analysis. Below, we explore the key features that make this tool an asset for security teams.
Latest vs. Previous Attack Path Distribution
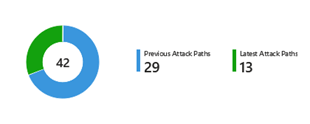
One of the dashboard’s standout features is its ability to differentiate between the latest and previous attack paths. This distinction is critical for security teams to immediately identify new potential threats as they surface in your environment, allowing for the swift prioritization of responses. By comparing current attack paths against historical data, teams can allocate their resources more efficiently, focusing on newly detected vulnerabilities while continuing to monitor ongoing threats.
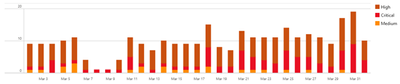
Risk Level Distribution Over Time
Understanding how risk levels of attack paths evolve over time is essential for strategic planning and defense optimization. The dashboard’s dynamic visualization of risk level distributions—categorized into critical, high, and medium—over various time frames provide a clear picture of possible threat evolution. While this chart may not delineate specific attack methodologies, its value lies in enabling security teams to quickly assess and prioritize the severity of possible attack vectors and their volume variation over time. By observing trends in the volume of critical versus less severe attack paths, teams can plan remediation strategies accordingly.
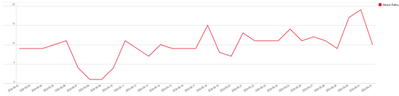
Overall Number of Attack Paths Over Time
The chart offers a visual summary of the attack paths detected over a selected time frame, illustrating the outcomes of security monitoring efforts. It doesn't predict when attacks might happen but shows the results of the security team's vigilance in identifying potential vulnerabilities. A consistent decline in detected paths could suggest that proper security posture and defensive measures are improving, while an increase may signal the need for a review of current security protocols. This type of chart adds value by helping security teams measure the effectiveness of their strategies, adjust their focus, and monitor their progress.
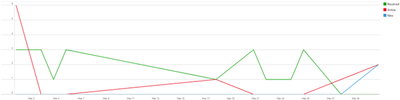
Active vs. Resolved Attack Paths
The dashboard further enhances operational transparency by categorizing attack paths as either active or resolved. This classification, coupled with metrics such as the duration of activity and new identifications, sheds light on the security team’s effectiveness and responsiveness. The inclusion of the Mean Time to Remediation (MTTR) metric provides an additional layer of insight, allowing teams to gauge the urgency and efficiency of their responses across different threat levels.
Active vs. Resolved Overtime
Visualizing the relationship between active and resolved attack paths overtime offers a narrative of the security team's ongoing efforts and challenges. This time chart distribution is an important tool for assessing progress, identifying periods of high threat activity, and evaluating the success of mitigation strategies.
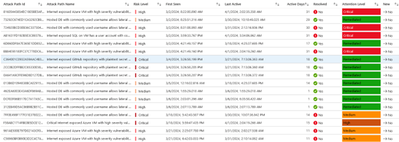
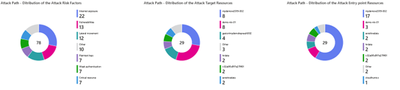
Risk Factor, Target, and Entry Point Distribution
Delving deeper into the nature of threats, the dashboard provides a granular analysis of attack paths by risk factors, targeted resources, and entry points. This breakdown identifies the most exploited vulnerabilities and high-risk assets, enabling security teams to tailor their defense mechanisms and prioritize hardening efforts where they are most needed.
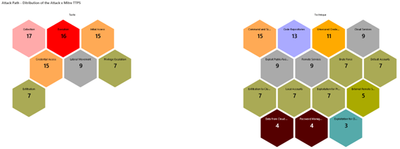
MITRE TTPs Distribution
The analysis of MITRE Tactics, Techniques, and Procedures (TTPs) distribution grants a strategic overview of prevalent attack methodologies. By understanding the tactics and techniques favored by adversaries, security teams can anticipate potential threats and refine their defenses accordingly. This strategic insight is crucial for staying one step ahead of attackers and fortifying cybersecurity defenses against the most common and impactful attack vectors.
Interpreting Advanced Metrics
Beyond the basic insights, understanding Percentiles for Time to Remediation, Count of Attack Paths by Remediation Time Brackets, and MTTR adds depth to your security analysis:
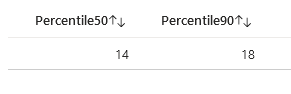
Percentiles for Time to Remediation
Time to Remediation (TTR) is a critical metric that measures the elapsed time of the creation of an attack path and its resolution. In the context of this Azure Workbook Attack Path Over Time Dashboard, Percentiles for Time to Remediation, specifically the 50th (median) and 90th percentiles, provide a detailed view of how quickly and efficiently an organization can mitigate threats.
50th Percentile (Median TTR): This metric represents the median response time, offering a snapshot of the typical remediation speed. A lower 50th percentile value is indicative of a swift median response time to threats, signifying that half of all detected attack paths are mitigated faster than the median value. This is an essential benchmark for security teams, reflecting their general responsiveness.
90th Percentile: The 90th percentile exposes concerns on the longer tail of remediation times, capturing how the most protracted responses are managed. A higher 90th percentile value may signal potential bottlenecks or complexities in resolving the most challenging incidents. This metric is crucial for identifying outliers in the remediation process, which, if addressed, could significantly improve overall security efficiency.
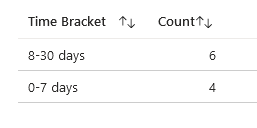
Count of Attack Paths by Remediation Time Brackets
To further refine the analysis, the dashboard segments the Count of Attack Paths into various Remediation Time Brackets (e.g., 0-7 days, 8-30 days, 31-60 days, over 60 days). This segmentation allows organizations to understand the distribution of their remediation efforts across different time frames.
High counts in shorter brackets (e.g., 0-7 days) suggest a robust capability to rapidly respond to a majority of threats, highlighting an effective incident response mechanism.
Conversely, significant counts in longer brackets (especially over 60 days) pinpoint areas where improvements are necessary. This could indicate more complex security issues requiring additional resources or more effective strategies to reduce the remediation time.
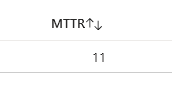
Mean Time to Remediation (MTTR)
Mean Time to Remediation (MTTR) aggregates the overall efficiency of the attack path resolution process into a single, comprehensive metric. It calculates the average time taken to resolve threats, offering a bird's eye view of the organization's response efficacy.
A lower MTTR value denotes quicker average remediation times, implying a highly efficient and agile response mechanism. This is the ideal scenario, as it minimizes the window of vulnerability, reducing the potential impact of breaches.
A higher MTTR, on the other hand, suggests room for improvement in the speed of remediation handling. It prompts security teams to delve deeper into the causes—be it the complexity of the attack paths exposed threats, resource constraints, or gaps in existing processes—and seek ways to enhance their response strategies.
Together, these advanced metrics serve as a compass for organizations, guiding them toward more effective and timely threat mitigation strategies. By analyzing Percentiles for Time to Remediation, the Count of Attack Paths by Remediation Time Brackets, and Mean Time to Remediation, security teams can gain insights into their operational strengths and areas in need of enhancement. This level of understanding is crucial for continuously refining cybersecurity defenses, ensuring organizations remain resilient in the face of an ever-evolving threat landscape.
Fictional Use Case: Woodgrove Bank's Cybersecurity Overhaul
Woodgrove Bank, a fictitious, rapidly growing tech company, recently faced a surge in cybersecurity threats as it expanded its digital footprint. Recognizing the critical need to enhance its security posture, the company adopted Microsoft Defender for Cloud and enabled the Defender CSPM so they could leverage the integrated attack path analysis feature. Woodgrove Bank also decided to adopt the Azure Workbook Attack Path Over Time Dashboard to monitor and analyze attack paths over time.
The Challenge
With its expansion, Woodgrove Bank experienced an increase in sophisticated cyber threats targeting its infrastructure. Initial analyses revealed a lack of clarity in prioritizing threats and an inconsistent approach to threat remediation. The security team's challenge was to streamline the process, ensuring rapid response to the most critical vulnerabilities.
Implementing the Azure Workbook Attack Path Over Time Dashboard
Upon implementing the Azure Workbook Attack Path Over Time Dashboard, Woodgrove Bank's security team gained valuable insight into the company's cybersecurity dynamics. The dashboard's metrics highlighted various aspects of their security posture, from the distribution of attack paths to the efficiency of response mechanisms.
The Monthly Report
Based on the insights gleaned from the dashboard, Woodgrove Bank produced a monthly report encapsulating their findings and strategies for improvement:
- Remediation Efficiency: The Mean Time to Remediation (MTTR) stood at 30 days. This metric, while reflective of a competent level of response, suggested room for improvement, particularly in handling complex attack vectors more efficiently.
- Distribution of Resolution Times: Analysis revealed a distribution that highlighted both strengths and areas for improvement:
- 0-7 days: 100 attack paths were remediated, showcasing the team's ability to quickly address a significant number of threats.
- 8-30 days: 75 attack paths, indicating a moderate response time for a substantial portion of threats.
- 31-60 days: 50 attack paths, pointing to complexities or resource allocation issues for a noteworthy fraction of incidents.
- Over 60 days: 25 attack paths remained unresolved for extended periods, underscoring critical vulnerabilities in the existing response framework.
- Classification of Overall Attack Path Remediation Efficiency: Considering the metrics, Woodgrove Bank classified its remediation efficiency as 'Moderate.' The rapid resolution of many threats demonstrated strong capabilities, but the slower response to a significant number of incidents highlighted the necessity for strategic enhancements.
Strategies for Improvement
Based on the insights from the monthly report, Woodgrove Bank outlined several key strategies to bolster its cybersecurity posture:
- Prioritizing Rapid Response: Focusing on reducing the MTTR by streamlining response protocols and enhancing the agility of the security operations team.
- Resource Reallocation: Shifting additional resources to address complex threats within the 31-60 day bracket more effectively.
- Enhanced Training and Tools: Investing in advanced training for the security team and integrating cybersecurity tools to tackle attack vectors efficiently.
- Continuous Monitoring and Adjustment: Leveraging the Azure Workbook Attack Path Over Time Dashboard for ongoing monitoring and fine-tuning of security strategies based on data and emerging threat landscapes.
Through the adoption of the Azure Workbook Attack Path Over Time Dashboard and the insights from the monthly report, Woodgrove Bank embarked on a strategic overhaul of its cybersecurity defenses. This use case illustrates the power of advanced analytics in transforming an organization's approach to cybersecurity, enabling a proactive, data-driven strategy to safeguard digital assets against an ever-evolving array of threats.
Conclusion
The Azure Workbook Attack Path Over Time Dashboard represents a significant advancement in cybersecurity defense, providing deep insights into the dynamics of proactive attack paths insights. It equips security teams with the necessary knowledge and tools to enhance their security posture, enabling proactive and informed responses to a diverse array of threats. By leveraging this powerful dashboard, organizations can not only respond to threats more effectively but also elevate their security operations to new levels of efficiency and sophistication
Additional Resources
If you are using Attack Path and Cloud Security Explorer and want to share your feedback with the Defender for Cloud Team, please e-mail us directly from here. You can also use the resources below to learn more about these capabilities:
- Cloud security explorer and Attack path analysis (Video)
- Identify and remediate attack paths
- Microsoft Defender for Cloud Security Posture Management
Reviewers
Yuri Diogenes, Principal PM Manager, CxE Defender for Cloud