This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Hello Folks,
Azure Networking is the foundation of your infrastructure in Azure. Each month we bring you an update on What’s new in Azure Networking.
In this blog post, we’ll cover what's new with Azure Networking in April 2024. In this blog post, we will cover the following announcements and how they can help you.
- Listener TLS certificates management in the Azure portal
- Application Gateway for Containers
- Application Gateway (v2) IPv6 support
- Microsoft open sources Retina: A cloud-native container networking observability platform
- Azure Virtual Network encryption now in additional regions
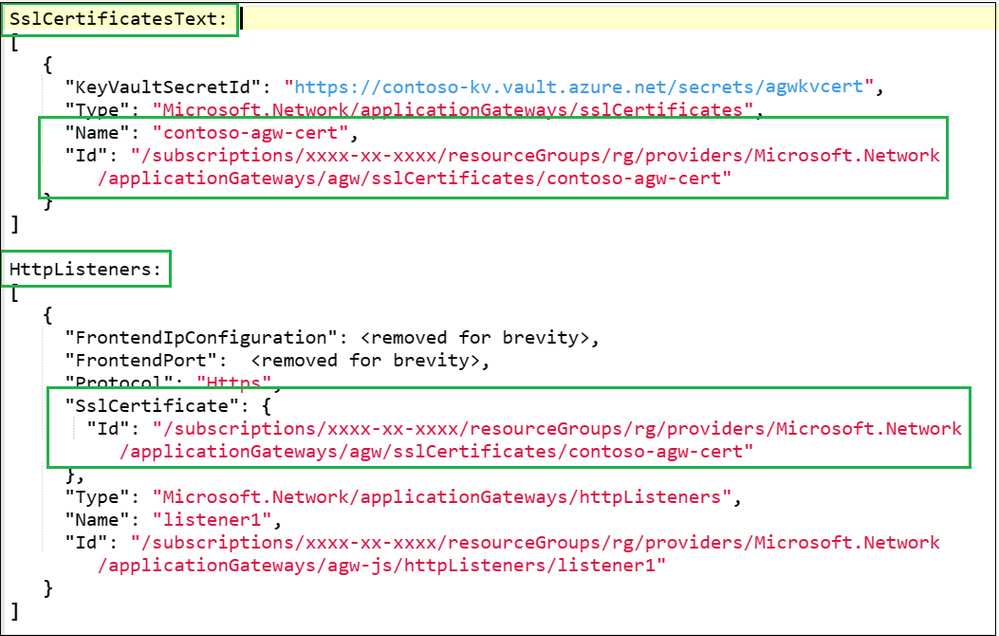
Listener TLS certificates management in the Azure portal
With this GA release, you can more easily manage TLS certificates for your Application Gateway workloads in the Azure Portal.
The Azure Application Gateway is a proxy load balancer that operates at Layer-7, the application layer of the OSI model. Now it supports Layer-4 proxy with TCP and TLS protocols as well. This provides scalable, highly available, and secure application delivery. One of its key features is the ability to secure client traffic through TLS termination, which requires TLS server certificates for listeners. For large gateways with multiple HTTPS or TLS listeners, this means managing multiple .PFX certificates.
- For certificate management in the portal, you can list and manage your certificates.
- Expiry
- Common Name
- Thumbprint
- Issuer Name
- Each certificate includes the following details for quick identification:
Managing certificates in any organization can be a challenge. This is a great addition for reducing friction for admins responsible for secure workloads utilizing certificates.
References:
- Application Gateway TCP/TLS proxy overview (Preview)
- Listener TLS certificate management in Application Gateway
- Quickstart: Direct web traffic using the portal - Azure Application Gateway
- TLS termination with Azure Key Vault certificates
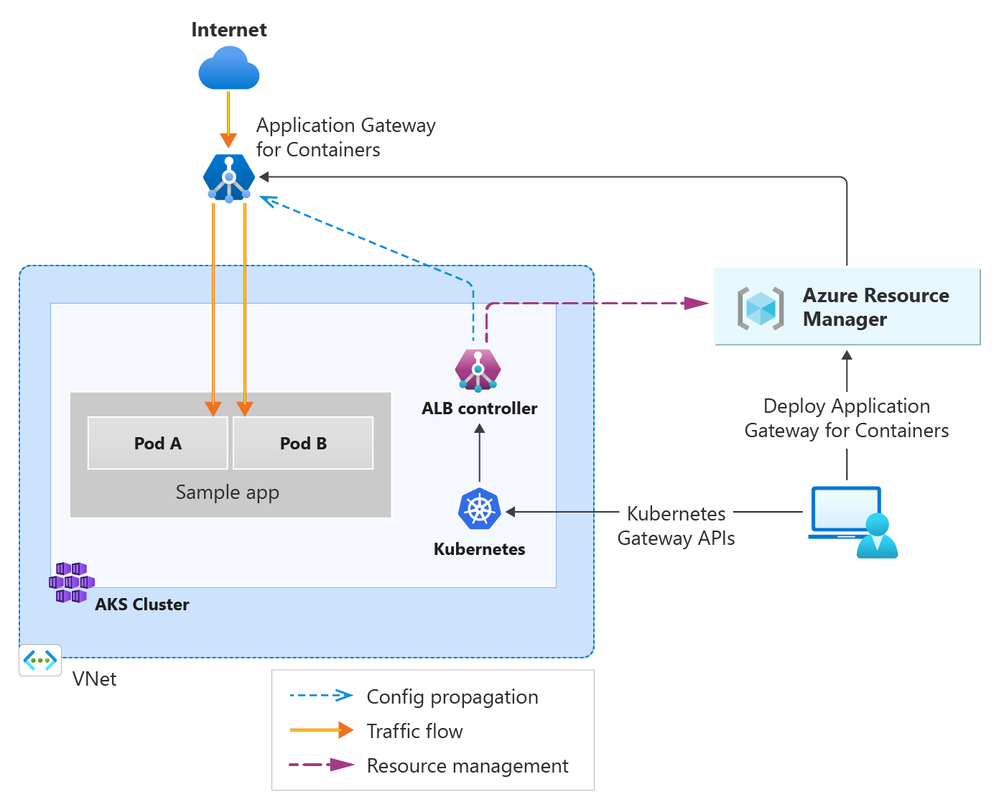
General availability: Application Gateway for Containers
Application Gateway for Containers is GA. With this release, you get application (layer 7) load balancing and dynamic traffic management capabilities for workloads running in a Kubernetes cluster.
Application Gateway for Containers is the evolution of the Application Gateway Ingress Controller (AGIC), a Kubernetes application that enables Azure Kubernetes Service (AKS) customers to use Azure's native Application Gateway application load-balancer. In its current form, AGIC monitors a subset of Kubernetes Resources for changes and applies them to the Application Gateway, utilizing Azure Resource Manager (ARM).
- Features - Public preview and GA has added support for Custom Health Probes, URL Redirect, URL / Header Rewrite.
- Controller High Availability – Have peace of mind if a node goes down, changes within your cluster will continue to be propagated to the network.
- Gateway API v1 – Bring the familiarity and role based access control provided by Gateway API to your network configuration.
- Additional Region Availability – Take advantage of Application Gateway for Containers in a region closest to you.
- SLA for Production Workloads – Feel confident in running your production workloads with Application Gateway for Containers.
References:
- What is Application Gateway for Containers?
- Application Gateway for Containers components
- Quickstart: Deploy Application Gateway for Containers ALB Controller
- What is Azure Application Gateway Ingress Controller?
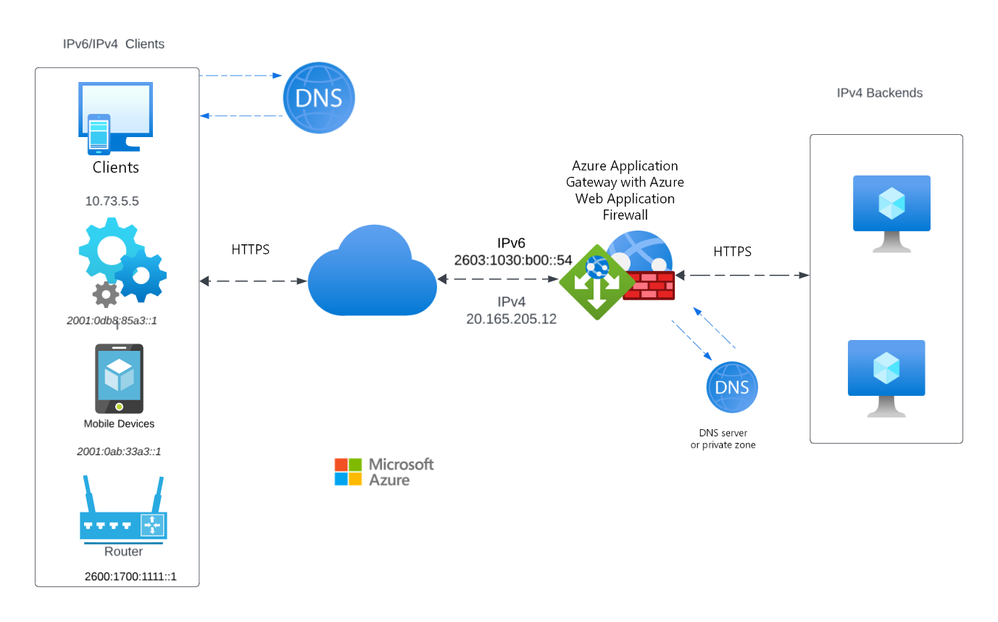
Application Gateway (v2) IPv6 support
We are announcing that IPv6 support for Azure Application Gateway (v2) is now generally available.
With the addition of IPv6 support, you can take advantage of the increased address space and improved routing efficiency that IPv6 provides. This is especially important for customers who are running out of IPv4 addresses or who need to support IPv6 clients.
To get started with IPv6 support for Azure Application Gateway (v2), simply create a new Application Gateway and select both IPv4 and IPv6 frontends during the creation process. You can also find more information about IPv6 support in our documentation.
References:
- Configure Application Gateway with a frontend public IPv6 address using the Azure portal
- What is Azure Application Gateway v2?
Microsoft open sources Retina: A cloud-native container networking observability platform
Retina is an open-source Kubernetes Network Observability platform designed to assist with DevOps, SecOps, and compliance use cases. It acts as a centralized hub for monitoring the health, security, and performance of applications and networks within Kubernetes clusters. The platform caters to Cluster Network Administrators, Cluster Security Administrators, and DevOps Engineers.
- Provides actionable network insights for cloud-native applications: Retina offers users a way to see how their containerized microservices interact on the network, helping them troubleshoot issues like latency, packet drops and many more.
- Non-intrusive and easy to use: Retina works with existing applications without requiring any code changes and provides users with simple ways to observe and troubleshoot network issues.
- Supports diverse environments: Designed to be adaptable, Retina works seamlessly with any CNI's (container network interface), OS, or cloud provider, making it a valuable tool across different environments.
Resources:
Azure Virtual Network encryption now in additional regions
Whenever Azure customer traffic moves between datacenters, Microsoft applies a data-link layer encryption method using the IEEE 802.1AE MAC Security Standards (MACsec). This encryption is implemented to secure the traffic outside physical boundaries not controlled by Microsoft or on behalf of Microsoft. This method is applied from point-to-point across the underlying network hardware. Virtual network encryption enables you to encrypt traffic between Virtual Machines and Virtual Machines Scale Sets within the same virtual network. It also encrypts traffic between regionally and globally peered virtual networks. Virtual network encryption enhances existing encryption in transit capabilities in Azure.
With Virtual Network encryption, customers can enable encryption of traffic between Virtual Machines and Virtual Machines Scale Sets within the same virtual network and between regionally and globally peered virtual networks. This new feature enhances the existing encryption in transit capabilities in Azure.
Azure Virtual Network encryption is available in the following additional regions:
- West Us
- West US 2
- East US 2
- US East
- Europe North
- Europe West
- France Central
- India Central
- UAE North
- East Asia
- Japan West
- Japan East
Resources:
That’s it for this month.
Cheers
Pierre