This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Azure Data Explorer (ADX) is a fast and scalable data analytics service that lets you query and analyze large volumes of data from various sources.
Have you ever thought of how to keep track of the health and performance of your workloads and business?
Have you ever encountered an issue where you wanted to get notified once something went wrong or needed your attention?
That's where alerts come in handy.
allow you to create rules that automatically trigger actions when certain conditions are met.
In this blog post, we’ll show you how to create alert rules that query an ADX database and trigger actions based on the results. This way, you can monitor the data that is important to you and get notified when something happens that needs your attention. Some example scenarios:
- You can create an alert rule to track your wind turbines yield and output. In case the output goes up to a level that risks the health of the facility an alert will be fired to allow you to take immediate action.
- You can create an alert rule that tracks the pollution metrics of your car fleet. If the pollution level goes above a certain threshold, an alert is fired and triggers a webhook that calls a custom function to notify operations managers and call cars to service.
Create an Azure Monitor alert rule
An Azure Monitor log search alert rule consists of three components:
Make sure you properly define the properties below when creating an alert rule:
- You need to specify the scope of the log search alert rule as the ADX cluster. You can do this in one of two ways:
- If you are creating the alert rule from the Alerts page of the Azure portal, in the pane to select the resource, select the ADX cluster as the scope for your alert rule . You can filter by subscription, resource type (“Azure data explorer cluster”), or resource location.
- If you are creating the alert rule directly from the ADX cluster blade, the scope is defined automatically as the ADX cluster.
- You need to define the ADX cluster as part of the query definition. 
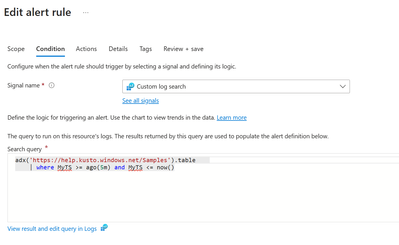
- Log Analytics can't automatically identify the column with the event timestamp. We recommend that if you're querying an ADX cluster, make sure that you add a time range filter to the query. For example: “adx('https://help.kusto.windows.net/Samples').table | where MyTS >= ago(5m) and MyTS <= now()”
- In the Managed Identity section, select which managed identity is used by the log search alert rule to send the log query. This managed identity is used for authentication when the alert rule executes the log query. If you are querying an ADX database you must add Reader role for all workspaces (or specific data) accessed by the query. As a part of the log search alert rule you will need to define one of the following options for the identity used by the alert rule (more details here):
- System assigned managed identity: Azure creates a new, dedicated identity for this alert rule. This identity has no permissions and is automatically deleted when the rule is deleted. After creating the rule, you must assign permissions to this identity to access the workspace and data sources needed for the query. For more information about assigning permissions, see Assign Azure roles using the Azure portal.
- User assigned managed identity: Before you create the alert rule, you create an identity and assign it appropriate permissions for the log query. When you select this type of identity, a pane opens for you to select the associated identity for the rule.
Conclusion
With ADX alerts, you can easily monitor your data and get notified when something important happens. You can also use ADX alerts to automate your workflows, such as triggering a remediation action, sending a report, or updating a dashboard. Click here to learn more about Azure Monitor log search alerts that query ADX.