This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Security operations center (SOC) teams actively look for opportunities to optimize both processes and outcomes. Every organization is unique, with its own security challenges. Teams must regularly adjust security controls to keep up with changing threat landscape and business priorities, while balancing investment (cost, SOC resources, time) and security coverage.
Today, we’re happy to announce the public preview of a new experience and API – Microsoft Sentinel’s SOC Optimization, designed to empower security teams with precision-driven management capabilities. SOC optimization offers actionable tailored recommendations that adapt daily to the organization’s environment – starting with gaps in data utilization and detection of different types of attacks . These aren’t generic tips; they’re personalized strategies backed by Microsoft’s cutting-edge research, ensuring your defenses are always at their peak and that the balance between investment and outcome is always maintained. SOC optimization is available both in the Azure portal and in the unified security operations platform.
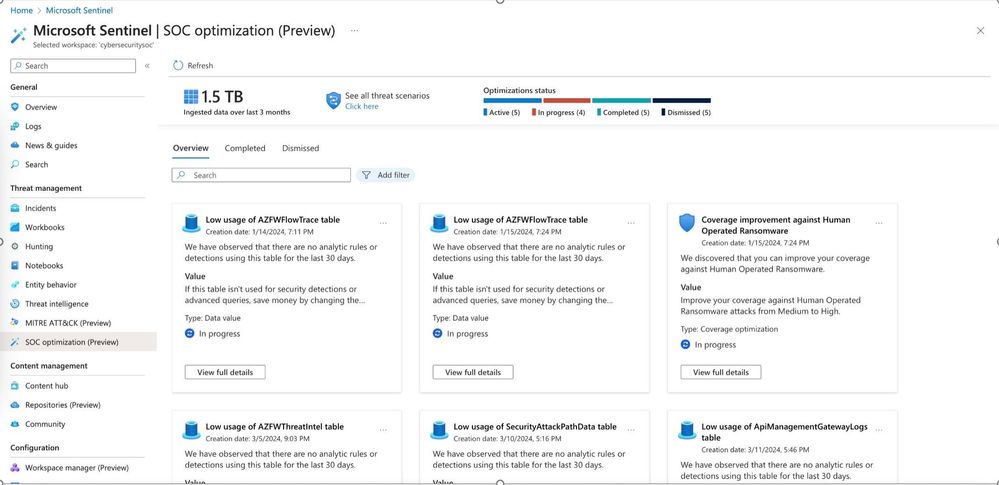

Use SOC optimization recommendations to help you close coverage gaps against specific threats and tighten your ingestion rates against data that doesn't provide security value. SOC optimizations helps you combine the power of the Microsoft out of the box content and knowledge with your organization's priorities, without having your SOC teams spend time on manual analysis and research.
Two types of recommendations are released today, but stay tuned as more types of recommendations will be added over time.
Data value optimizations:
Knowledge is power, especially when it comes to data. With SOC Optimization, you gain deep insights into your data usage patterns. These insights come with actionable recommendations for immediate improvements in threat protection, making your data work smarter, not harder. Leveraging a new deep integration with Log Analytics, Content hub and the Analytics wizard, you gain instant visibility to how billable data is being used and whether it can be leveraged further for better security coverage.
This is how it looks on the Azure portal:

Sometimes, ingested data doesn't have security value or doesn't justify the cost (investment) when considering usage and Microsoft's out of the box content for that data source. Then, SOC optimization will suggest changes in ingestion or re-consideration of ingestion to optimize costs.

In both cases, the action is straight-forward and integrated into the experience. At times, a table might have both options - better utilization for security coverage by adding detections, or - if the specific organization doesn't see value in detections on this data - ingestion changes.
In this case, this is how it looks in the unified security operations platform:

The balance between cost and security is delicate. SOC Optimization helps you strike the perfect balance, enhancing your security coverage while optimizing data ingestion and managing costs
Threat-based optimizations:
To optimize data value, SOC optimization recommends adding security controls to your environment in the form of extra detections and data sources, using a threat-based approach backed by Microsoft’s security researchers.
To provide threat-based recommendations, SOC optimization looks at your ingested logs and enabled analytics rules, and compares it to the logs and detections that are required to protect, detect, and respond to specific types of attacks - based on Microsoft's security research . A straight forward map shows the gap between the two, using the MITRE ATT&CK framework and actionable recommendations that leverage the integration with Content hub will guide you until the gap is bridged.


You can also find at the top of the page a link to view all threat scenarios currently covered by SOC optimization and see a concise view of your score for each one of those attacks.
Stay proactive against threats like Business Email Compromise and Human Operated Ransomware with precise, threat-based recommendations, ensuring your defenses are always up-to-date.
Empowering Automation with an API
Flexibility is key in modern cybersecurity, and SOC Optimization extends its capabilities through an API. This allows for seamless integration with existing systems and processes, enabling automation and enhancing the overall experience of managing your security operations. Using the API can also allow looking across workspaces and tenants, to ensure a broader conversation on gaps and optimizations.
Taking your SOC to the next level
SOC Optimization is not just a tool; it’s a strategic partner. It offers daily, personalized recommendations that align with your organization’s security needs while leveraging Microsoft's unique security expertise and signals. These recommendations are powered by Microsoft’s security research, ensuring you’re equipped with best practices for detecting and responding to threats.
Learn more:
For more exciting Sentinel news: Sentinel RSA news blog post
Documentation: SOC optimization overview ; Recommendation's logic
Experience overview and live demo in the Unified Security Operations Portal: SOC optimization Ninja show
