This post has been republished via RSS; it originally appeared at: New blog articles in Microsoft Community Hub.
Secure your organization’s access to manage customers with recommendations built for Managed Service Providers
We know that Managed Service Providers (MSPs) take on large responsibilities in managing multiple customers at once. Having the right permissions at the right time enables MSPs to minimize security risks and exposure. To help right-size your delegated access, we recommend that you use Granular Delegated Admin Privileges (GDAP) and adopt additional security measures like just-in-time (JIT) access.
We also understand the challenges of setting up permissions to provide IT services for managed customers. Delegated Admin Privileges (DAP) grant broad access across customer tenants, which makes it difficult to establish governance. Local accounts on customer tenants pose additional security risks, making it challenging to trace who made changes through auditing. Microsoft released GDAP to enable MSPs to move towards a least-privileged access approach by offering granular and time-bound permissions per customer. However, GDAP’s granularity can add to the complexity of setup. Through an experience designed specifically for MSPs, Lighthouse simplifies the process of setting up delegated access and empowers MSPs to set up GDAP end-to-end.
Use GDAP templates to configure delegated access
In collaboration with MSPs, we’ve developed five support roles in our default recommendations: Account manager, Service desk agent, Specialist, Escalation engineer, and JIT agent. An Account manager, for example, may require customer access occasionally to read licensing and usage information. In contrast, an Escalation engineer may require customer access more regularly to provide hands-on services across Microsoft workloads. MSPs can adopt recommended roles or customize them based on their organization’s needs. We’ve tailored our recommendations to accommodate MSPs of different sizes and operating models to help you eliminate the guesswork of assigning permissions.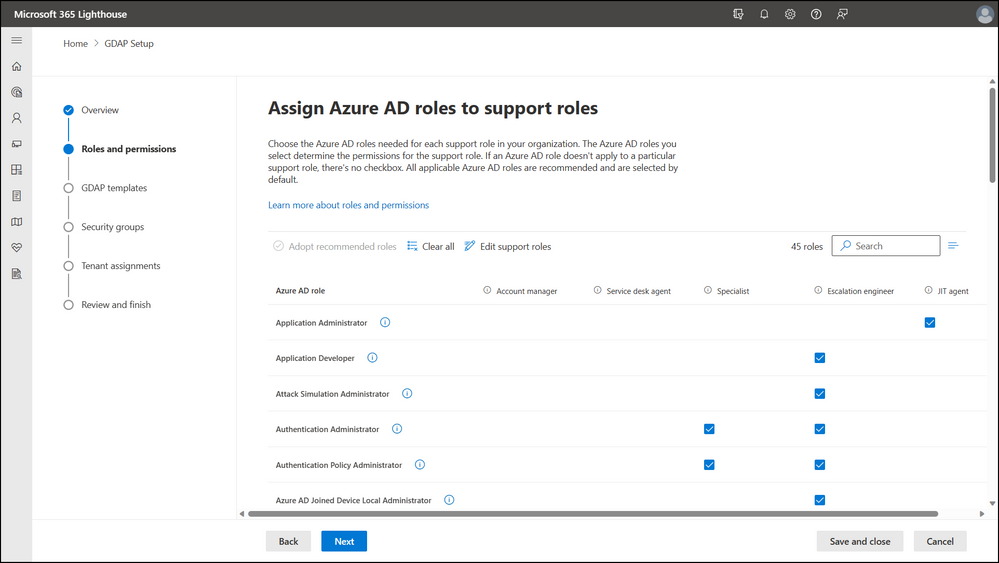
Lighthouse offers GDAP templates to help MSPs save time and reapply GDAP settings as new customers are onboarded. To segment permissions across customers, we’ve enabled the capability to set up multiple GDAP templates. MSPs can use GDAP templates to establish GDAP quickly and reduce the administrative overhead of manually assigning permissions one customer at a time.
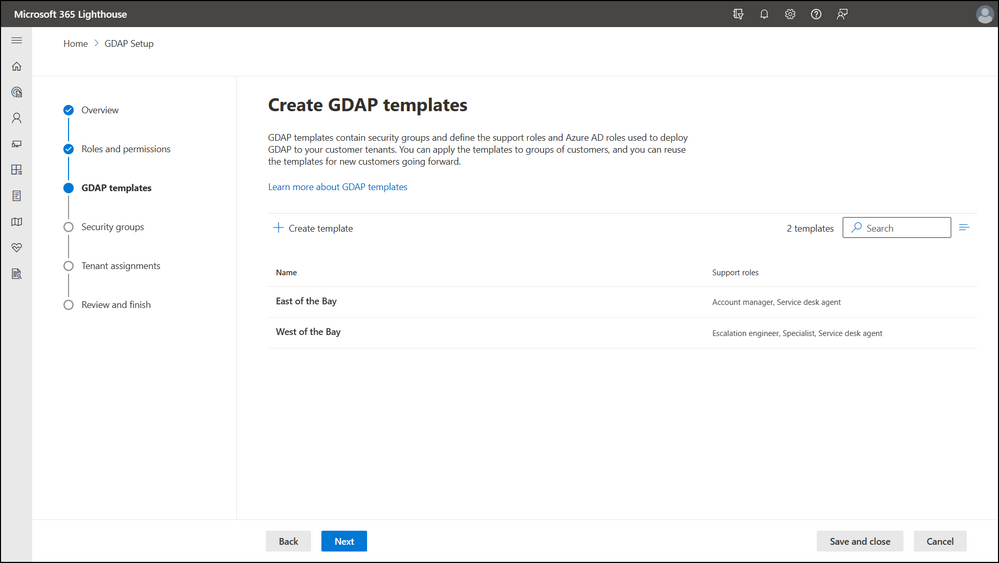
Assign users to roles and implement just-in-time access
Setting up GDAP means your customers and users are set up for success. To guide you through this process, we help you create security groups and assign users. These security groups are granted the roles defined in your GDAP template for the customers to whom the GDAP template is assigned. With Microsoft 365 Lighthouse, there is no need to jump between different admin portals to ensure users have the roles they need to do their jobs. Did a new Escalation Engineer join the team? Head to Lighthouse to set them up in the right security groups across your GDAP templates.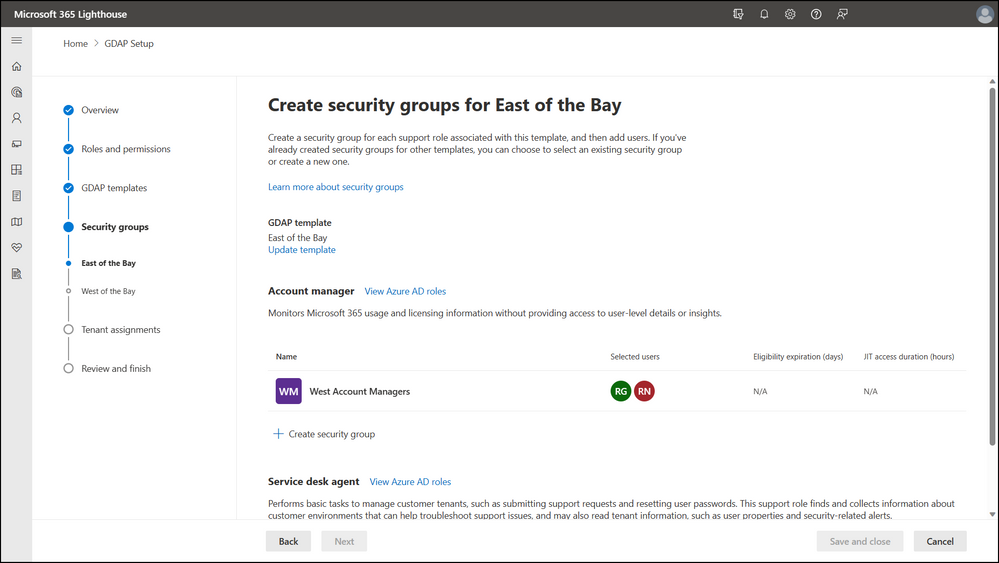
Furthermore, we know that highly privileged access may be needed by users especially when supporting IT for small and medium-sized businesses. At a moment’s notice, highly privileged access may be needed for urgent tasks like unlocking the CEO of a small business’s account or digging into the details of an active incident detected by Microsoft Defender for Business. Setting up just-in-time (JIT) access to prepare for these moments is critical to following Microsoft's Zero Trust cybersecurity protocol. GDAP templates with JIT access create a policy for users to access highly privileged roles, like Global Admin, only when needed. Users designated as approvers can review access requests for these roles, which establishes traceability, accountability, and transparency in granting highly privileged customer access.
Migrate to GDAP using Lighthouse’s recommendations before key milestones
Microsoft will begin automatically migrating DAP relationships to GDAP relationships with a limited set of roles at the end of May 2023. In July, Microsoft will begin deprecating DAP relationships. Updated dates for key milestones can be found here. Ahead of these dates, we recommend that MSPs use Lighthouse’s GDAP setup wizard to transition their customers to GDAP and adopt our recommendations to ensure customer access isn’t disrupted.
MSPs can use Lighthouse to migrate any customer tenant with DAP, GDAP, or a reseller relationship using our GDAP setup wizard. But, for a limited time, Lighthouse makes it possible to set up GDAP relationships automatically for any customer tenant that still has DAP. After DAP is deprecated, MSPs will require customer approval for new GDAP relationships. To simplify the transition process, it’s imperative that MSPs migrate customers from DAP to GDAP today
Get started by registering for Lighthouse, logging in with the required roles and using GDAP to configure delegated access.
To learn more about Microsoft 365 Lighthouse and GDAP, check out:
Secure Microsoft 365 Lighthouse (cloudguides.com)
Sign up for Microsoft 365 Lighthouse - Microsoft 365 Lighthouse | Microsoft Learn
Overview of Microsoft 365 Lighthouse - Microsoft 365 Lighthouse | Microsoft Learn
Set up GDAP for your customers - Microsoft 365 Lighthouse | Microsoft Learn
GDAP frequently asked questions - Partner Center | Microsoft Learn
