This post has been republished via RSS; it originally appeared at: Microsoft Tech Community - Latest Blogs - .
Later this month, we'll be making architectural updates to the security settings management capabilities in Microsoft Defender for Endpoint that simplify the device enrollment process. The updates include removing Azure Active Directory (AD) join or Hybrid Azure AD joinas a pre-requisite for onboarding Windows devices that use security settings management in Defender for Endpoint. To learn more about this capability, see Manage Microsoft Defender for Endpoint on devices with Microsoft Intune.
This update applies to customers that are opted into public preview functionality for Defender for Endpoint. Customers that don’t use public preview features will continue with the existing settings management experience. To opt in, go to the Microsoft Defender for Endpoint portal, and select Settings > Endpoints > Advanced features > Preview features. Ensure your Windows device is up to date to take advantage of these enhancements.
How this works
Customers already using this functionality will seamlessly transition to the updated infrastructure with no impact for their existing Windows devices managed by Defender for Endpoint that are using this functionality. Endpoint security policies will continue to apply as expected. Additionally, there will be no changes to the device, its identity, or registration type. Any new devices enrolled into security settings management for Defender for Endpoint will use the updated infrastructure.
Important: If a Windows device was managed by Defender for Endpoint via security settings management for Defender for Endpoint but was unable to enroll due to not being Azure AD joined or Hybrid Azure AD joined, these devices will now succeed enrollment and policies targeted to the device will apply. Once enrolled, the device will appear in the device lists for Microsoft 365 Defender, Microsoft Intune, and Azure AD portals. Note that while the device won’t be fully registered with Azure AD it'll still count as one device object.
To filter for devices that were previously unable to enroll in Defender for Endpoint due to not meeting the Azure AD join or Hybrid Azure AD join pre-requisite, navigate to the Microsoft 365 Defender portal > Devices list and filter by enrollment status. Since these devices are still not fully registered, they’ll show the device attributes where MDM = Intune and Join Type = Blank. With the new release, these will begin to successfully enroll.
What to expect in the Microsoft 365 Defender portal
In the Microsoft 365 Defender device inventory, you can confirm that the device is using the security settings management capability in Defender for Endpoint by checking its status in the Managed by column. This is also available on the device side panel or device page and should consistently indicate managed by MDE.
On the device side panel or device page, you can also confirm it’s successfully enrolled by checking the MDE Enrollment status is Success.
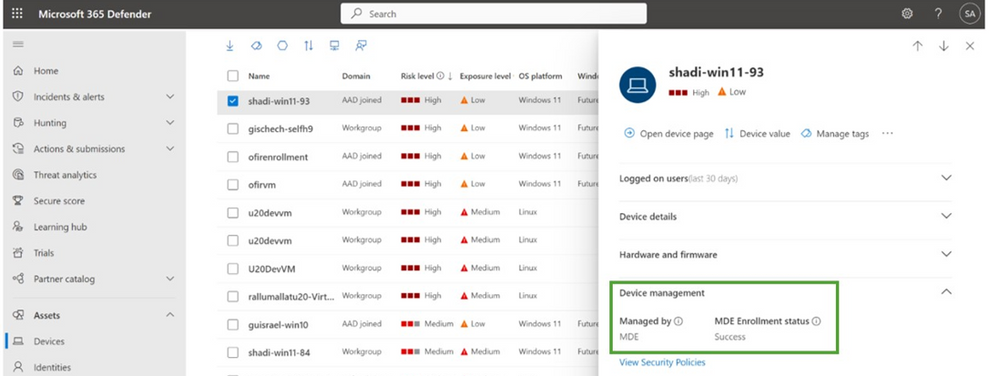
If the MDE Enrollment status is not “Success,” make sure you’re looking at a device that was updated and is in scope for settings management (based on how you configured the feature in the 'enforcement scope’ page).
What to expect in the Microsoft Intune admin center
In the Intune admin center, search for the device name on the All Devices page. The device should appear here as well, with the Managed by field set to MDE.

If policies were assigned to devices that had previous enrollment errors, then policies will apply as these devices start to onboard via the updated infrastructure.
What to expect in the Microsoft Azure portal

To ensure that all devices enrolled in security settings management for Microsoft Defender for Endpoint receive policies, we recommend creating a dynamic Azure AD group based on the systemLabels property containing the “MDEManaged” value. This will automatically add devices managed by Defender for Endpoint to the group, without requiring admins to perform any additional tasks, such as creating a new policy.
Stay tuned to What’s new in Intune for the release and for further additions to this functionality! If you have any questions, let us know in the comments or reach out to us on Twitter @IntuneSuppTeam.
